[ad_1]

A darknet platform dubbed “Zombinder” allows threat actors to link malware to legitimate Android apps, forcing victims to infect themselves while still having the full functionality of the original app to escape suspicion.
This new platform was discovered by cybersecurity firm ThreatFabric, which spotted malicious Windows and Android campaigns distributing multiple malware families.
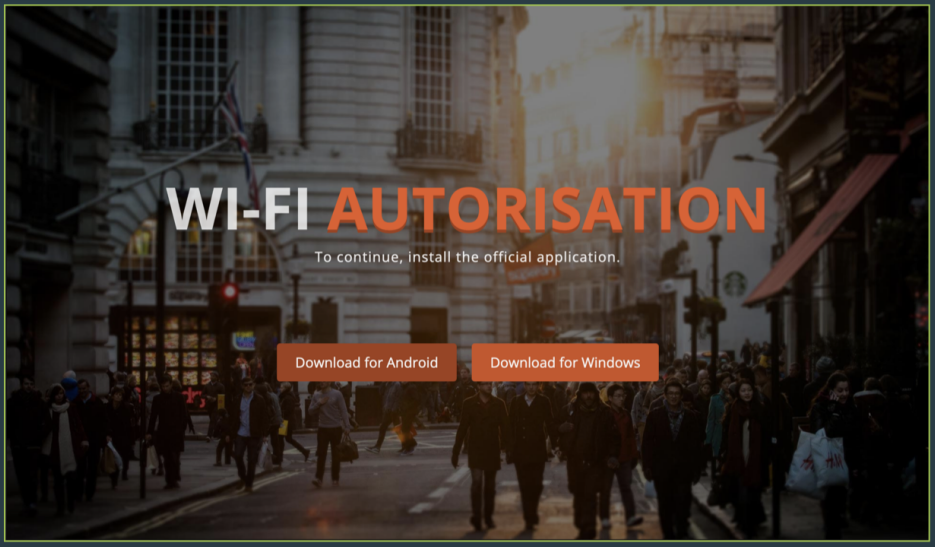
The campaign poses as Wi-Fi authorization portals, which are supposed to help users access internet hotspots as a decoy to push various families of malware. The site then prompts the user to download a Windows or Adware version of the app, which is actually malware.
ThreatFabric Reports that the operation claimed thousands of lives, with Erbium Thieves infections alone stealing data from 1,300 different computers.
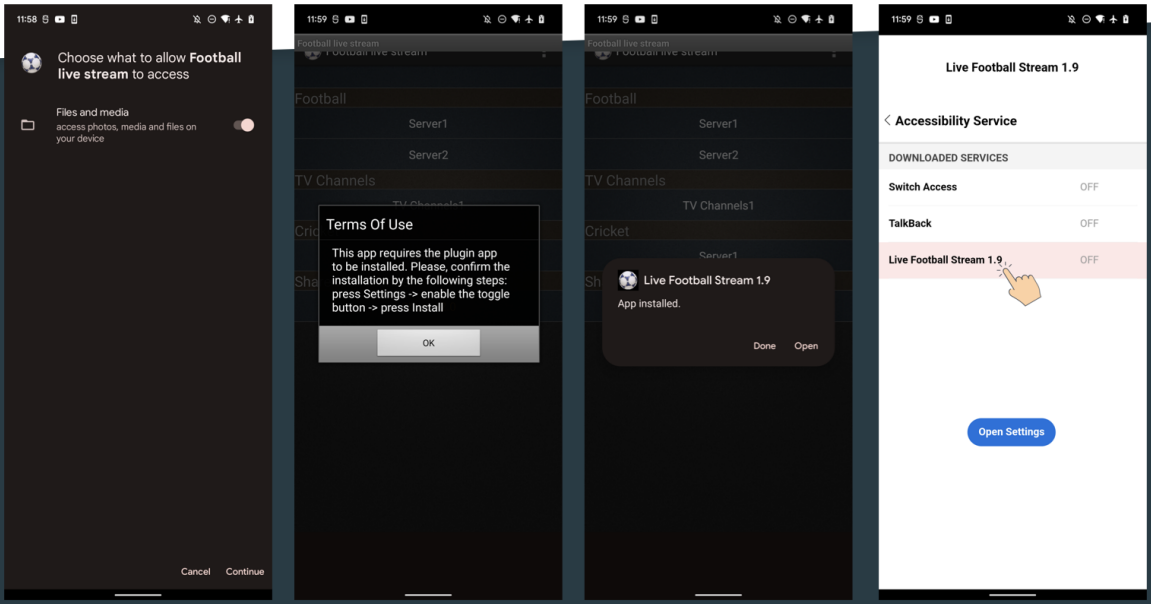
Zombinder for Android
An interesting aspect of the campaign is the darknet service, which researchers have dubbed “Zombinder”, which offers malicious APK linking of malware to legitimate Android apps.
Zombinder was launched in March 2022 as a malware packer on APK files, and according to ThreatFabric, it is now increasingly popular in the cybercrime community.
The APKs used in this campaign vary, with analysts reporting seeing a fake live football streaming app and a modified version of the Instagram app.
These apps work as expected because the functionality of the legitimate software is not removed. Instead, Zombinder adds a malware loader to its code.
The loader is obfuscated to evade detection, so when the user launches the application, the loader displays a prompt to install a plugin. If the prompt is accepted, the loader installs a malicious payload and launches it in the background.
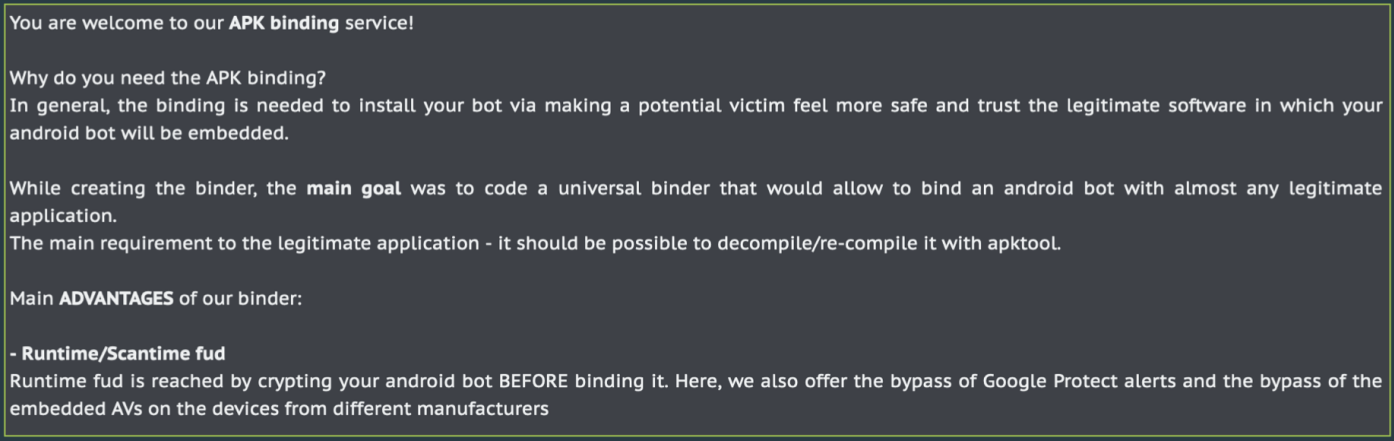
Service provider Zombinder claims that malicious app bundles created with it are undetectable at runtime and can bypass Google Protect alerts or antivirus running on target devices.
The campaign drops a Ermac payload for Android capable of performing keylogging, overlay attacks, stealing Gmail emails, intercepting 2FA codes and stealing crypto wallet seed phrases.
Windows Malware
If the visitor to the Wi-Fi authorization website clicks the “Download for Windows” button, they download Windows malware instead.
Examples seen by ThreatFabric include the Erbium Thiefthe Lawn mowerand the Aurora Info Thief.
These are all dangerous and high-performing malware strains currently under development, rented out to cybercriminals for a few hundred dollars a month.
Since there is an overlap in the capabilities of these malware strains, threat actors are likely experimenting with various tools to see what works best for them.
Commodity malware has become so readily available that threat actors can quickly trade in their tools and expand their portfolios simply by investing more.
ThreatFabric says the wide variety of Trojans delivered by the same landing pages could indicate that a single third-party malware distribution service serves multiple threat actors.
[ad_2]
Source link
