[ad_1]

A member of the US Navy’s Red Team has released a tool called TeamsPhisher that exploits an unresolved security issue in Microsoft Teams to circumvent restrictions for incoming files from users outside a targeted organization, self- called external tenants.
The tool uses a issue highlighted last month by Max Corbridge and Tom Ellson of UK-based security services firm Jumpsec, who explained how an attacker could easily bypass Microsoft Teams file upload restrictions to deliver malware from an account external.
The exploit is possible because the application has client-side protections that can be tricked into treating an external user as an internal user simply by changing the ID in a message’s POST request.
Streamline attacks against Teams
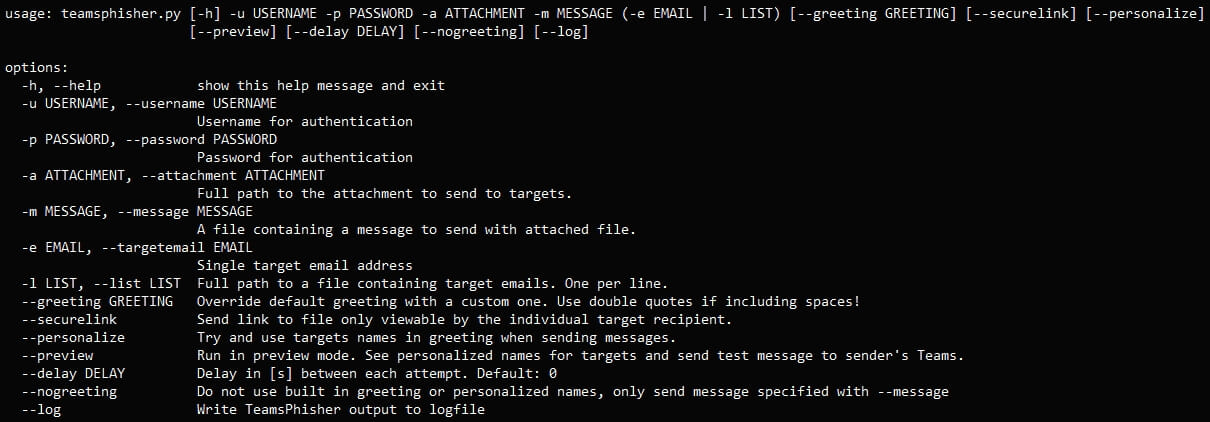
‘TeamsPhisher’ is a Python-based tool that provides a fully automated attack. It incorporates the attack idea from Jumpsec researchers, techniques developed by Andrea Santeseand Bastian Kanbach’s ‘authentication and assistance features’TeamsEnum‘ tool.
“Give TeamsPhisher an attachment, a message, and a list of target Teams users. It will download the attachment to the sender’s Sharepoint, then iterate through the list of targets,” reads the description from Alex Reid, the developer of the Red Team utility.
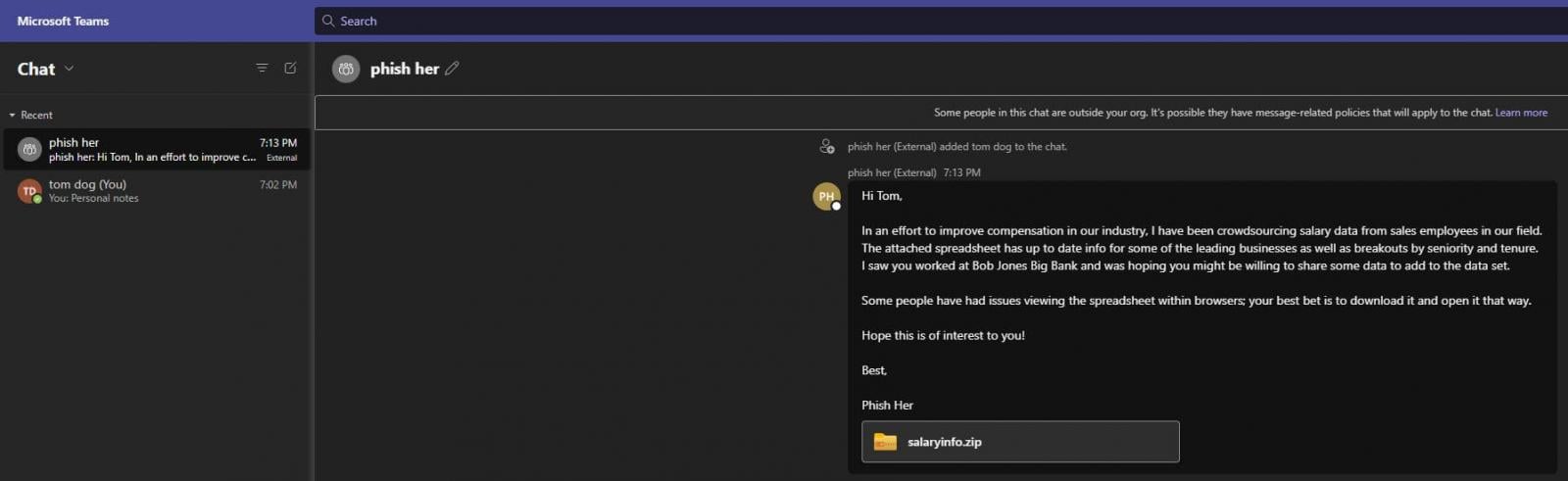
TeamsPhisher first verifies the existence of the target user and their ability to receive external messages, which is a prerequisite for the attack to work.
It then creates a new thread with the target, sends them a message with a Sharepoint attachment link. The thread appears in the sender’s Teams interface for (potential) manual interaction.
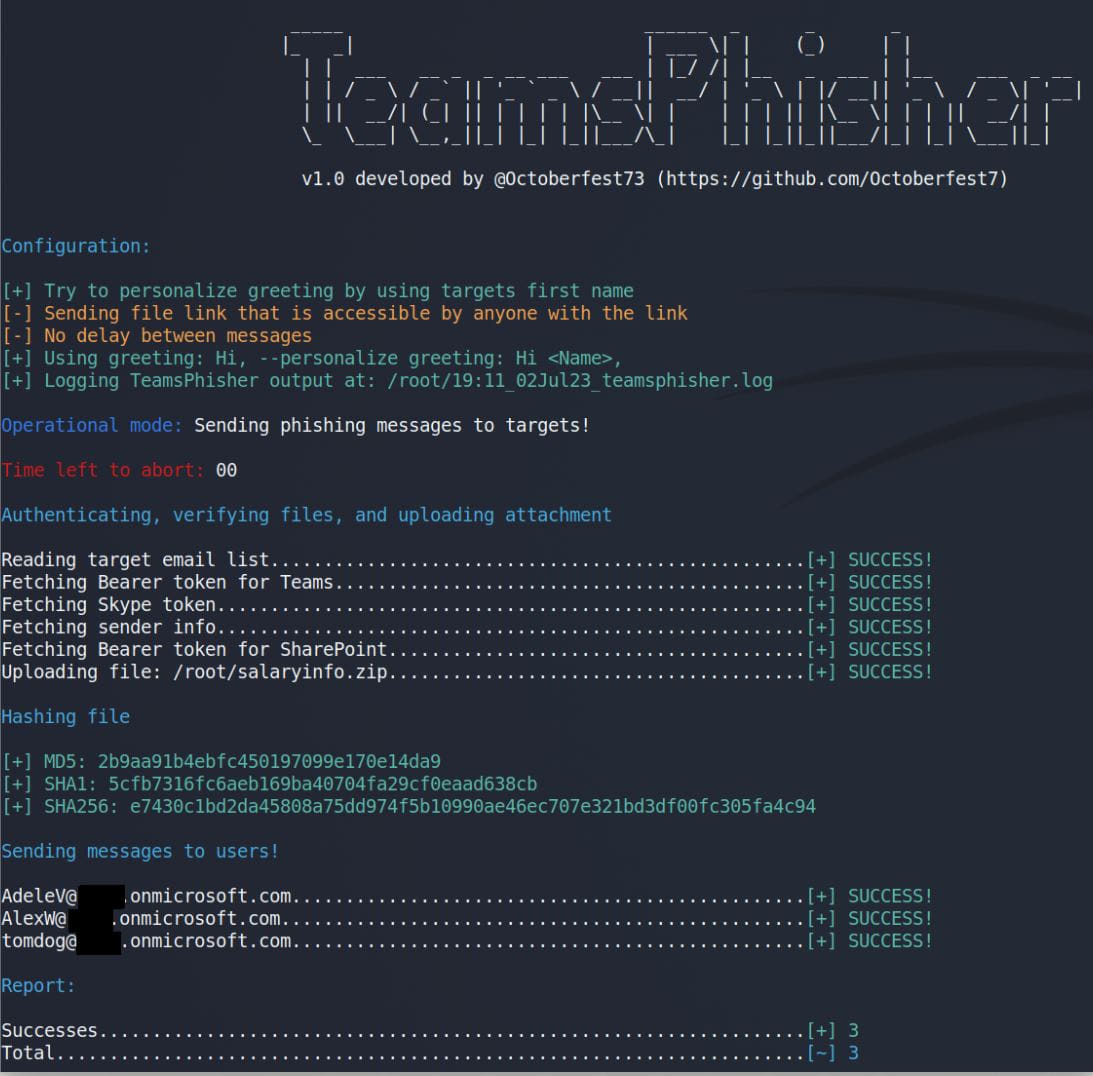
TeamsPhisher requires users to have a Microsoft Business account (MFA is supported) with a valid Teams and Sharepoint license, which is common for many large companies.
The tool also offers a “preview mode” to help users verify defined target lists and check how messages look from the recipient’s perspective.
Other optional features and arguments in TeamsPhisher could refine the attack. These include sending secure file links that can only be viewed by the intended recipient, specifying a delay between message transmissions to circumvent rate limiting, and writing outputs to a log file. .
Unresolved issue
The problem that TeamsPhisher exploits is still present, and Microsoft told researchers at Jumpsec that it did not hit the bar for immediate service.
BleepingComputer also contacted the company last month for comment on plans to fix the issue, but did not receive a response. We reiterated our request for comment from Microsoft but did not receive a response at press time.
Although TeamPhisher was created for authorized red team operations, threat actors can also leverage it to deliver malware to target organizations without raising alarms.
Until Microsoft decides to take action on this, organizations are strongly advised to disable communications with external tenants if they are not needed. They can also create a whitelist with trusted domains, which would limit the risk of exploitation.
[ad_2]
Source link
