[ad_1]

A new reflective denial-of-service (DoS) amplification vulnerability in the Service Location Protocol (SLP) allows hackers to launch massive denial-of-service attacks with 2,200X amplification.
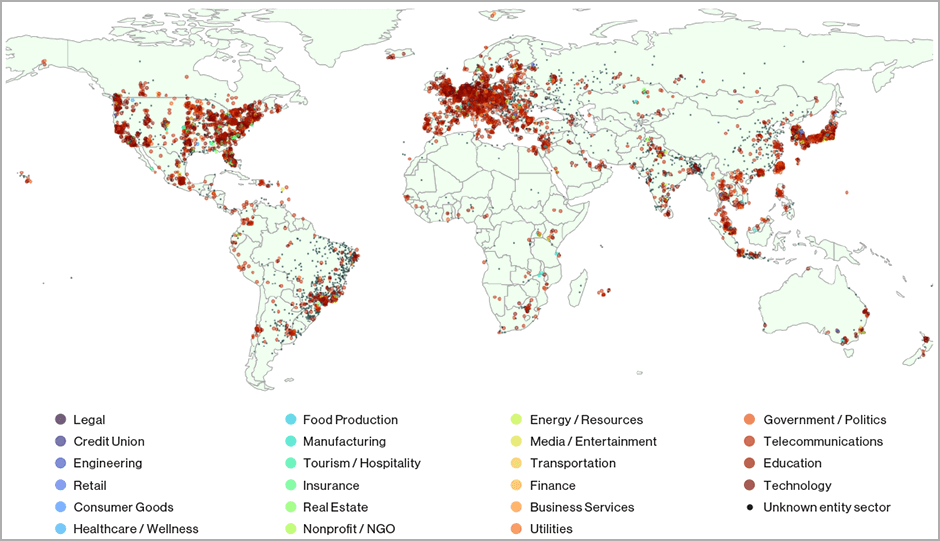
This flaw, identified as CVE-2023-29552, was discovered by researchers from BitSight and Curesec, who claim that more than 2,000 organizations use devices that expose approximately 54,000 exploitable SLP instances for use in amplification attacks. DDoS.
Vulnerable services include VMWare ESXi hypervisors, Konica Minolta printers, IBM embedded management modules, and Planex routers deployed by unsuspecting organizations around the world.
The most vulnerable cases are in the United States, Britain, Japan, Germany, Canada, France, Italy, Brazil, the Netherlands and Spain, held by several Fortune 1000 companies in the fields of technology, telecommunications, health, insurance, finance, hotels and transport.
The SLP vulnerability
Service Location Protocol (SLP) is an old Internet protocol created in 1997 for use in local area networks (LANs), allowing easy connection and communication between devices using a service availability system via UDP and TCP on port 427.
While its intended use was never to be exposed on the public internet, organizations have exposed SLP on tens of thousands of devices over the years.
“Service Location provides a dynamic configuration mechanism for applications in local area networks. It is not a global resolution system for the entire Internet; rather, it is intended to serve enterprise networks with Shared Services,” says the protocol description.
According to BitSight, all of these instances are vulnerable to CVE-2023-29552 (CVSS score: 8.6), which attackers can exploit to launch reflective DoS amplification attacks on targets.
Specifically, the flaw allows unauthenticated attackers to register arbitrary services on the SLP server, manipulating the content and size of its response to achieve a maximum amplification factor of 2,200x.
These many exposed servers could allow threat actors to carry out massive DDoS attacks against businesses, government entities and critical services to render them inaccessible or no longer function as intended.
Due to the critical nature of this flaw, the US Department of Homeland Security’s Cybersecurity and Infrastructure Agency (CISA) conducted an extensive outreach campaign to notify potentially affected vendors of the vulnerability.
DoS boost
DoS boost attacks involve sending a request with the attack target’s source IP address to a vulnerable device, letting the data size grow within the abused service to the maximum point, and then releasing the response to the victim.
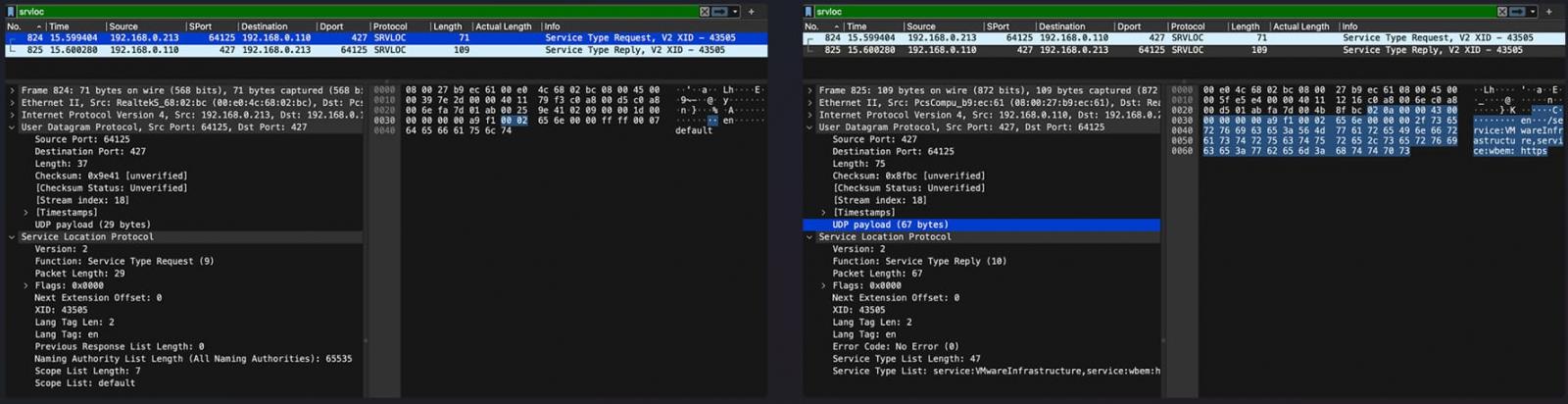
Usually, the size of a typical response packet from an SLP server is between 48 and 350 bytes, so without manipulation the amplification factor can reach up to 12x.
However, by exploiting CVE-2023-29552, it is possible to increase the server’s UDP response size by registering new services until the response buffer is full.
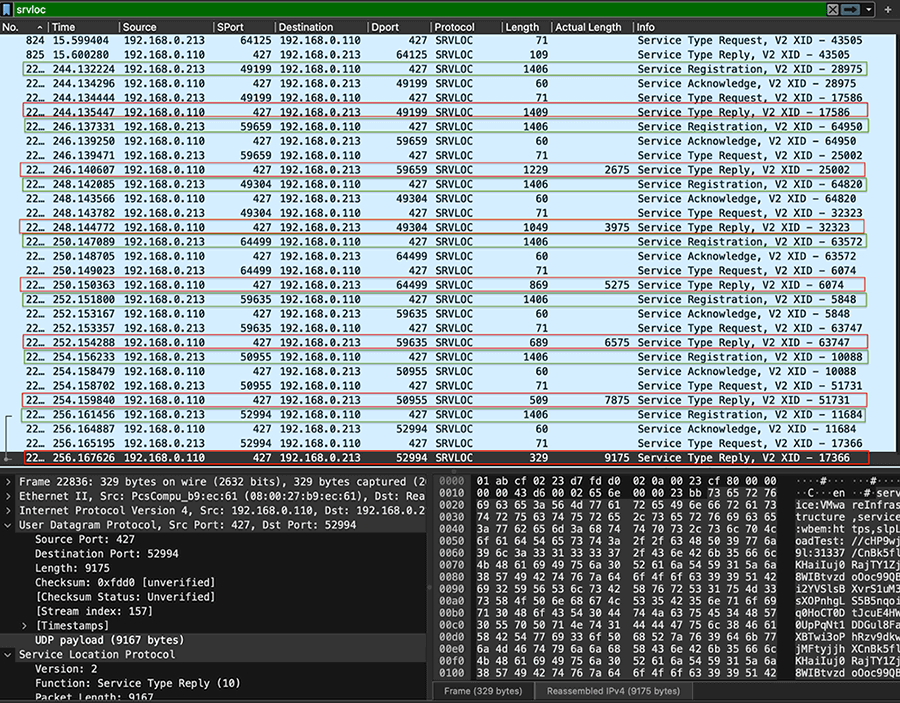
By doing so, attackers can achieve a maximum amplification factor of 2,200x, turning a tiny 29-byte request into a massive 65,000-byte response directed at the target.
“This extremely high amplification factor allows an under-resourced threat actor to significantly impact a targeted network and/or server via a reflective DoS amplification attack,” warns the BitSight report.
In a real-world attack scenario, a threat actor would leverage multiple SLP instances to launch such an attack, coordinating their responses and overwhelming their targets with massive traffic.
To protect your organization’s assets from potential abuse, SLP should be disabled on systems exposed to the Internet or untrusted networks.
If this is not possible, it is recommended to configure a firewall that filters traffic on UDP and TCP port 427, which is the main entry for malicious request that exploits SLP services.
VMWare also has published a newsletter on this, clarifying that the problem only affects older versions of ESXi that are no longer supported, advising administrators to avoid exposing them to untrusted networks.
[ad_2]
Source link
