[ad_1]

A new ChromeLoader campaign is underway, infecting visitors to pirated warez and movie sites with a new variant of the search hijacker and advertising browser extension named Shampoo.
This discovery of the new campaign comes from the threat research team at HP (Wolf Security), which reports that the operation has been ongoing since March 2023.
ChromeLoader History
ChromeLoader is a browser hijacker that forcibly installs browser extensions that redirect search results to promote unwanted software, fake giveaways, surveys, adult games, dating sites and other irrelevant results.
About a year ago, analysts at red canary reported a sudden spike in ChromeLoader distribution that started in February 2022, now including macOS in the targeting scope along with Windows.
In September, VMware and Microsoft savvy another massive ChromeLoader campaign featuring the experimental ability to drop additional malware, including ransomware.
More recently, in February 2023, security researchers from ASEC discovery a campaign where the ChromeLoader malware was distributed in VHD files named after popular video games.
Most recent campaign
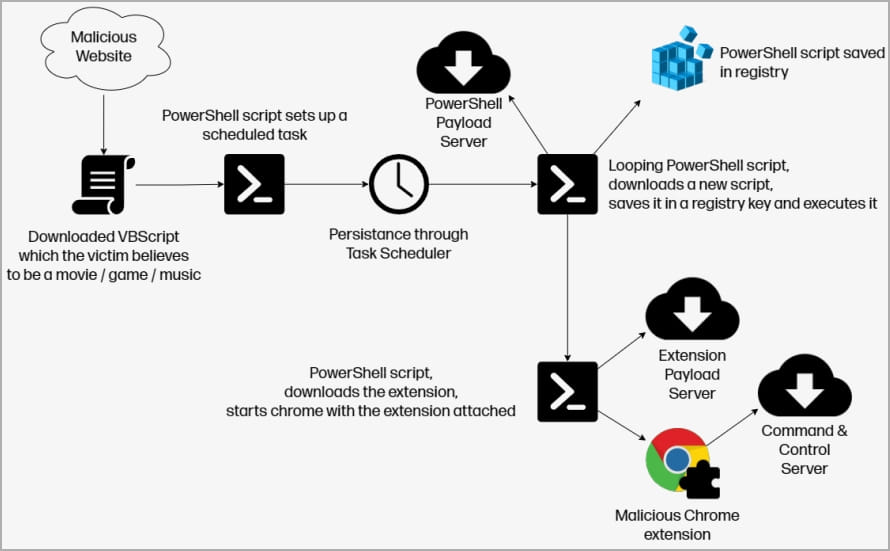
HP analysts report that in the campaign that began in March 2023, ChromeLoader is being distributed through a network of malicious websites that promise free downloads of copyrighted music, movies or video games.
Instead of media files or legitimate software installers, victims download VBScripts that run PowerShell scripts setting up a scheduled task prefixed with “chrome_” for persistence.
This task triggers a series of scripts that download and register a new PowerShell script in the host’s registry as “HKCU:\Software\Mirage Utilities\” and also fetch the malicious Chrome extension, Shampoo.
Shampoo is a variant of ChromeLoader, capable of injecting advertisements on websites visited by the victim and performing search query redirects.
In a sample analyzed by BleepingComputer, searches from the browser’s address bar or Google are first redirected to a website at ythingamgladt[.]com, then to Bing search results.
Once the malicious extension is installed, it prevents the victim from accessing the Chrome extensions screen. Instead, users are redirected to Chrome’s settings screen when they attempt to do so.
The operation of the adware is believed to be financially motivated, aiming to generate revenue from search redirects and advertisements.
Of course, it is not difficult for victims to notice these redirects, because they do not get what they are looking for on Google, but removing the malware is complicated.
“Removing ChromeLoader Shampoo is not as simple as uninstalling a legitimate extension,” warns HP in the report.
“The malware relies on looping scripts and a scheduled Windows task to reinstall the extension each time the victim removes it or restarts their device.”
Therefore, if the victim restarts the system, the Chrome malware will be temporarily disabled, but it will be reinstalled quickly.
To get rid of ChromeLoader Shampoo, HP Wolf Security says users can perform the following steps:
- Delete all scheduled tasks preceded by “chrome_”. Legit Chrome scheduled tasks are normally prefixed with “Google”.
- Delete the “HKCU\Software\Mirage Utilities\” registry key.
- Then restart the computer.
BleepingComputer also found the PowerShell scripts extracting the malicious extension to the ‘C:\Users\
HP warns that these removal steps should be done quickly before the looping script reinstalls the malware.
An easy way to determine if a ChromeLoader variant is running on your web browser is to check if Chrome is running with the “-load-extension” argument. You can use tools like Process Explorer to examine the properties of a process and see the command line arguments.
HP explains that those working in corporate environments infected with ChromeLoader may be reluctant to seek help from colleagues in IT, as they fear the consequences of violating their employer’s policies by downloading software from dubious sources.
However, the threat of adware should not be ignored or minimized, as it is still a trojan running on your system that could attempt to cause greater damage at any time, should its operators decide to seek more aggressive monetization routes from their infections.
[ad_2]
Source link
