[ad_1]

A new exploit called “Sh1mmer” lets users unenroll a company-managed Chromebook, allowing them to install any apps they want and bypass device restrictions.
When Chromebooks are enrolled with a school or business, they are governed by policies established by the organization’s administrators. This allows administrators to force-install browser extensions, apps, and restrict device usage.
Also, once enrolled, it is almost impossible to unenroll the device without the organization administrator doing it for you.
To circumvent these restrictions, security researchers from the Mercury Workshop team have developed a new exploit called “Shady Hacking 1nstrument Makes Machine Enrollment Retreat”, or “Sh1mmer‘, which allows users to unenroll their Chromebooks from enterprise management.
The exploit requires a publicly disclosed RMA shim that the Sh1mmer exploit will modify to allow users to manage device enrollment. Researchers say the following Chromebook cards are known to have released RMA shims.
brask, brya, clapper, coral, dedede, enguarde, glimmer, grunt, hana, hatch, jacuzzi, kukui, nami, octopus, orco, pyro, reks, sentry, stout, strongbad, tidus, ultima, volteer, zorkFor those unfamiliar with RMA shims, these are disk images stored on USB devices that contain a combination of the ChromOS factory bundle components used to reinstall the operating system and used manufacturer tools to perform repairs and diagnostics.
To use this exploit, you need to download an RMA shim for your Chromebook card, use the finder online builder to inject him with the Sh1mmer exploit, then run chrome recovery utility.
By following the steps detailed on the Sh1mmer site, you can load the modified RMA shim to launch the Sh1mmer menu, shown below.
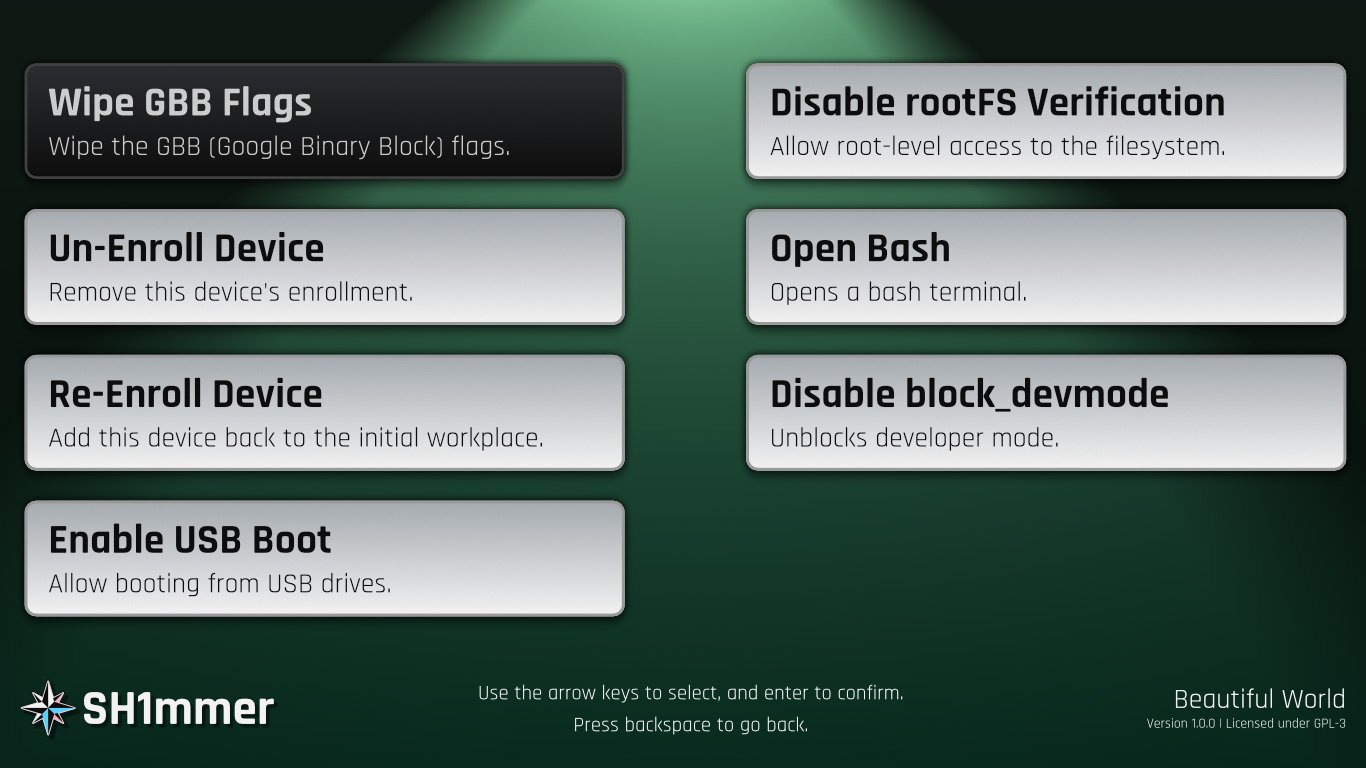
From this menu, you can unenroll and re-enroll a device as needed, enable USB booting, allow root-level access to the operating system, open a bash shell, and more.
A member of the k12sysadmin Reddit group tested the exploit and said he could use it to unenroll his Chromebook and use it as a brand new device.
“I tested with my spare Acer 311/722 this morning. It does exactly what it says. Go into Utilities, clear the GBB flags, then deprovision and reboot”, posted a technician to Reddit group /r/k12sysadmin.
“I could then register it with my personal email and everything will work like a new device out of the box without forced registration.”
Another system administrator warned that using this exploit likely violates the student code of conduct and could lead to serious consequences.
“Other IT admins are warning that this is a serious violation of the school. At this point it’s practically vandalizing school property and breaking your AUP (probably)”, wrote a k12sysadmin member.
“It’s not a technical issue, it’s a discipline issue. Once you find out, have the school confiscate the Chromebook and have the IT department re-register the Chromebook on the network.”
“Take the neighborhood children’s use of technology away for a year. They should learn their lesson.”
Google told BleepingComputer that they are aware of the exploit and are working to resolve the issue.
“We are aware of the issue affecting a number of ChromeOS device RMA shims and are working with our hardware partners to address it,” Google told BleepingComputer.
Unfortunately, they did not provide information on how administrators can prevent the exploit or detect exploited devices.
However, when the Sh1mmer exploit is used, the device will appear as inactive in the admin console.
Another member of the k12sysadmin Reddit group said admins can enable Inactive device notifications to receive emails when a device becomes inactive, allowing administrators to examine it further and see if the exploit has been used.
[ad_2]
Source link
