[ad_1]

Following a cyberattack on a US-based company, malware researchers have discovered what appears to be a new strain of ransomware with “technically unique characteristics”, which they have named Rorschach.
Among the abilities seen is encryption speed, which the researchers tested would make Rorschach the fastest ransomware threat today.
Analysts discovered that the hackers deployed the malware to the victim network after exploiting a weakness in a threat detection and incident response tool.
Rorschach details
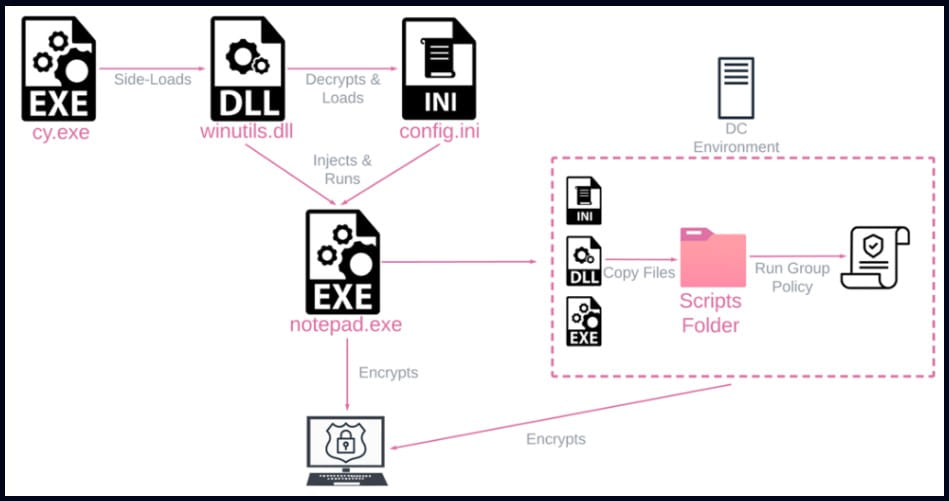
Researchers from cybersecurity firm Check Point, responding to an incident at a company in the United States, discovered that Rorschach had been deployed using the DLL sideloading technique via a signed component in Cortex XDR, the product Palo Alto Networks Extended Detection and Response.
The attacker used the Cortex XDR Dump Service Tool (cy.exe) version 7.3.0.16740 to sideload the loader and Rorschach injector (winutils.dll), which led to the ransomware payload, “config.ini”, being launched in a Notepad process.
The load file has UPX-style anti-analysis protection, while the main payload is protected against reverse engineering and detection by virtualizing parts of the code using VMProtect software.
Checkpoint reports that Rorschach creates Group Policy when run on a Windows domain controller to propagate to other hosts in the domain. After compromising a machine, the malware erases all event logs.
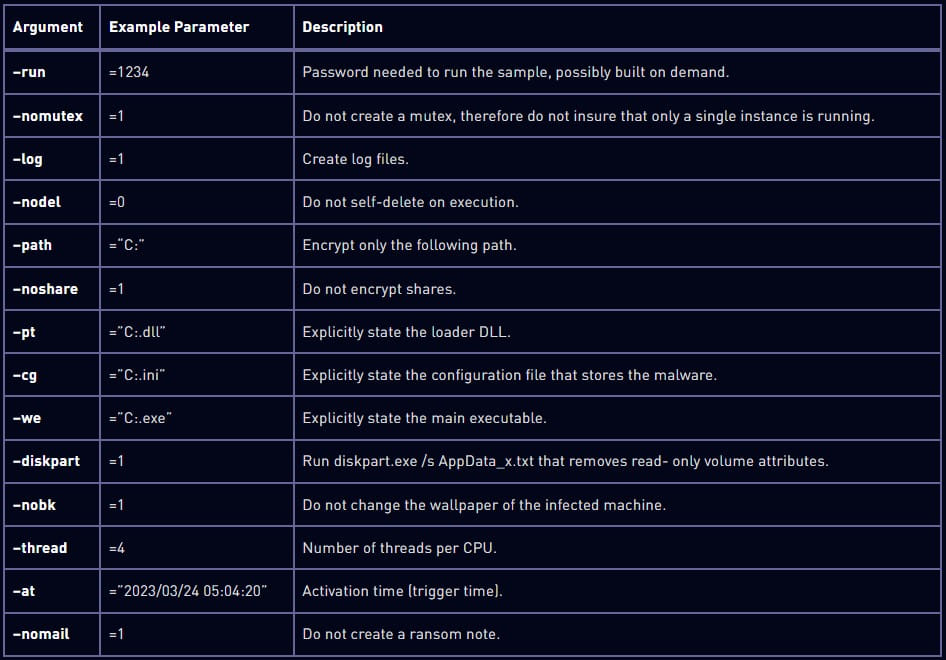
Although it comes with a hard-coded configuration, Rorschach supports command-line arguments that extend functionality.
Check Point notes that the options are hidden and cannot be accessed without reverse-engineering the malware. Here are some of the arguments discovered by the researchers:
The Rorschach encryption process
Rorschach will only start encrypting data if the victim machine is configured with a language outside of the Commonwealth of Independent States (IEC).
The encryption scheme combines the curve25519 and eSTREAM hc-128 encryption algorithms and follows the intermittent cipher trendmeaning that it only partially encrypts files, giving it increased processing speed.
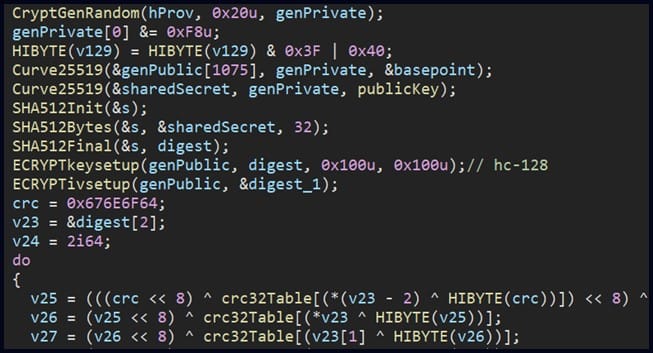
The researchers note that the Rorschach cipher routine indicates “a very efficient implementation of thread scheduling via I/O completion ports.”
To determine the speed of Rorschach encryption, Check Point set up a test with 220,000 files on a 6-core processor machine.
It took 4.5 minutes for Rorschach to encrypt the data, while LockBit v3.0, considered the fastest ransomware strain, completed in 7 minutes.
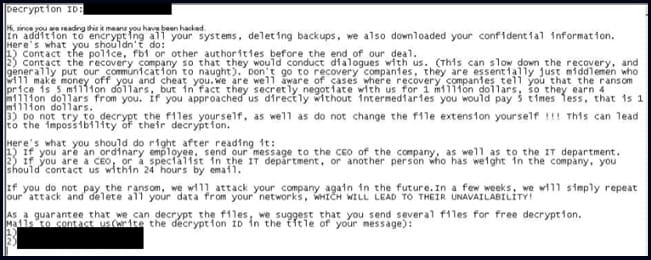
After locking the system, the malware drops a ransom note similar to the format used by Yanlowang ransomware.
According to the researchers, a previous version of the malware used a ransom note similar to the one used by DarkSide.
Check Point says this similarity is likely what led other researchers to confuse a different version of Rorschach with DarkSide, an operation that rebranded as BlackMatter in 2021, and disappeared the same year.
BlackMatter Members Edit formed the ALPHV/BlackCat ransomware operation launched in November 2021.
Check Point assesses that Rorschach has implemented the best features of some of the top ransomware strains leaked online (Babuk, LockBit v2.0, DarkSide).
In addition to self-spreading capabilities, the malware “raises the bar for ransomware attacks”.
At the moment, the operators of Rorschach ransomware remain unknown and there is no branding, which is rarely seen in the ransomware scene.
[ad_2]
Source link
