[ad_1]

A cyber espionage and hacking campaign being tracked as “RedClouds” uses custom malware “RDStealer” to automatically steal data from shared drives over Remote Desktop connections.
The malicious campaign was discovered by Bitdefender Labswhose researchers have seen hackers target systems in East Asia since 2022.
While they were unable to attribute the campaign to specific threat actors, they do mention that the threat actors’ interests align with those of China and have the sophistication of a level State-sponsored APT.
Additionally, Bitdefender claims that particular hackers have been leaving traces of activity since at least 2020, initially using off-the-shelf tools and moving to custom malware in late 2021.
Fly from a remote desktop
Remote Desktop Protocol (RDP) is a Microsoft proprietary protocol that allows users to remotely connect to Windows desktops and use them as if they were in front of the computer.
This feature is extremely useful for a variety of tasks, including remote work, tech and IT support, system administration, and server management.
RDP servers exposed to the Internet are among the most targeted online services because they provide a foothold on a corporate network. Once they gain access to it, threat actors can use this presence to spread laterally throughout the corporate network during data theft and ransomware attacks.
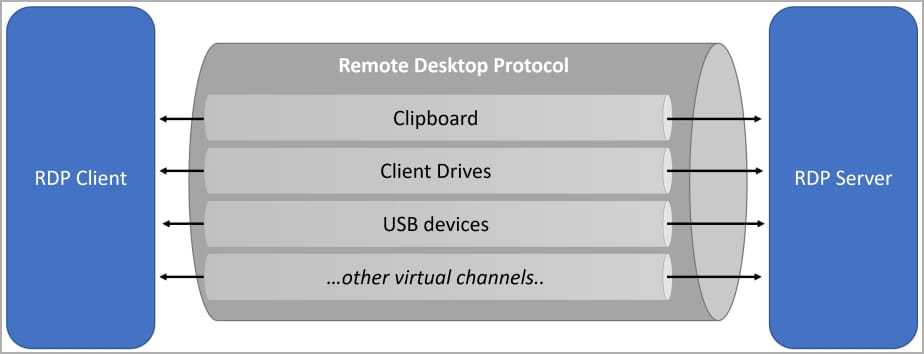
The Remote Desktop Protocol includes a feature called ‘device redirection,’ which allows you to connect your local drives, printers, Windows clipboard, ports, and other devices to the remote host, which are then accessible in your remote desktop sessions.
These shared resources are accessible through a ‘\\tsclient‘ (terminal server client) network share which can then be mapped to drive letters in your RDP connection.
For example, if the local C:\ drive was shared via device redirection, it would be accessible as ‘\\tsclient\c‘ in the RDP session, which can then be used to access locally stored files from the remote Windows desktop.
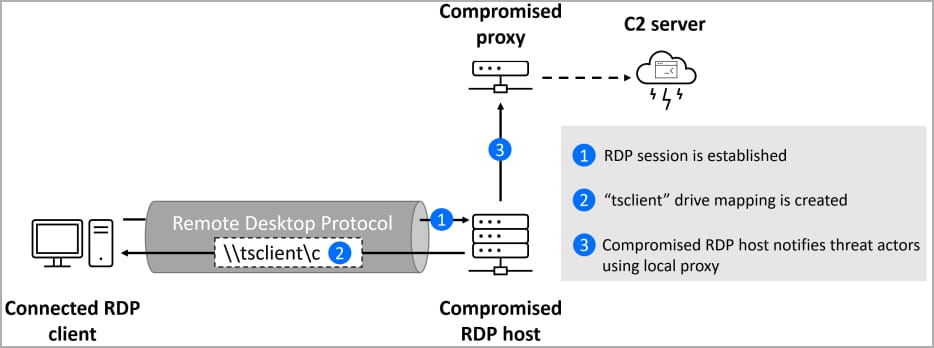
Threat actors infect remote desktop servers with custom RDStealer malware that takes advantage of this device redirection feature. It does this by monitoring RDP connections and automatically stealing data from local drives once they are connected to the RDP server.
The five modules that make up RDStealer are a keylogger, a persistence facility, a theft preparation and data exfiltration module, a clipboard content capture tool and encryption/decryption function control, logging and file manipulation.
Upon activation, RDStealer enters an infinite loop of calling the “diskMounted” function, which checks the availability of drives C, D, E, F, G or H on the \\tsclient network shares. If it finds any, it notifies the C2 server and begins to exfiltrate data from the connected RDP client.
It should be noted that the locations and filename extensions that the malware enumerates on C:\ drives include KeePass Password Database, SSH Private Keys, Bitvise SSH Client, MobaXterm, Logins mRemoteNG, etc., making it clear that attackers are looking for credentials they can use for lateral movement.
On all other drives, RDStealer will scan everything, with a few exceptions that are unlikely to host valuable data.
Bitdefender lacks information on how remote desktop servers are infected in the first place, but discovered that the malware was stored in the following folders:
%WinDir%\System32\
%WinDir%\System32\wbem\
%WinDir%\security\database\
%PROGRAM_FILES%\f-secure\psb\diagnostics
%PROGRAM_FILES_x86%\dell\commandupdate\
%PROGRAM_FILES%\dell\md storage software\md configuration utility\“As part of the evasion tactic, threat actors used folders that are less suspected of containing malware and are often excluded from scanning by security solutions,” says BitDefender.
All data stolen from the compromised device is stored locally as encrypted strings in the “C:\users\public\log.log” file until it is transmitted to the attackers’ servers.
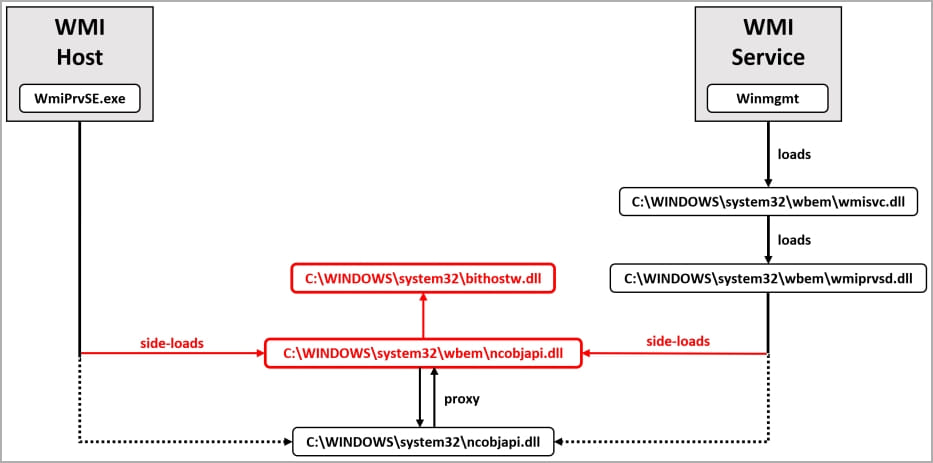
The final step in running RDStealer is to enable two DLL files, the Logutil backdoor (“bithostw.dll”) and its loader (“ncobjapi.dll”).
Custom Logutil malware
The RedClouds campaign also uses a custom Go-based backdoor named Logutil that allows threat actors to remotely execute commands and manipulate files on an infected device.
The malware uses passive and active DLL side-loading flaws to run on a hacked system undetected and uses Windows Management Instrumentation (WMI) as an activation trigger.
“This implant is very effective in establishing persistence on the system”, describes Bitdefender.
“It can be triggered either by the WMI service (started automatically with several recovery actions) or by the WMI host process.”
“There are often multiple instances of the WMI host process (WmiPrvSE.exe) running, and there are multiple ways to start this process (including through the DCOM interface for remote WMI calls).”
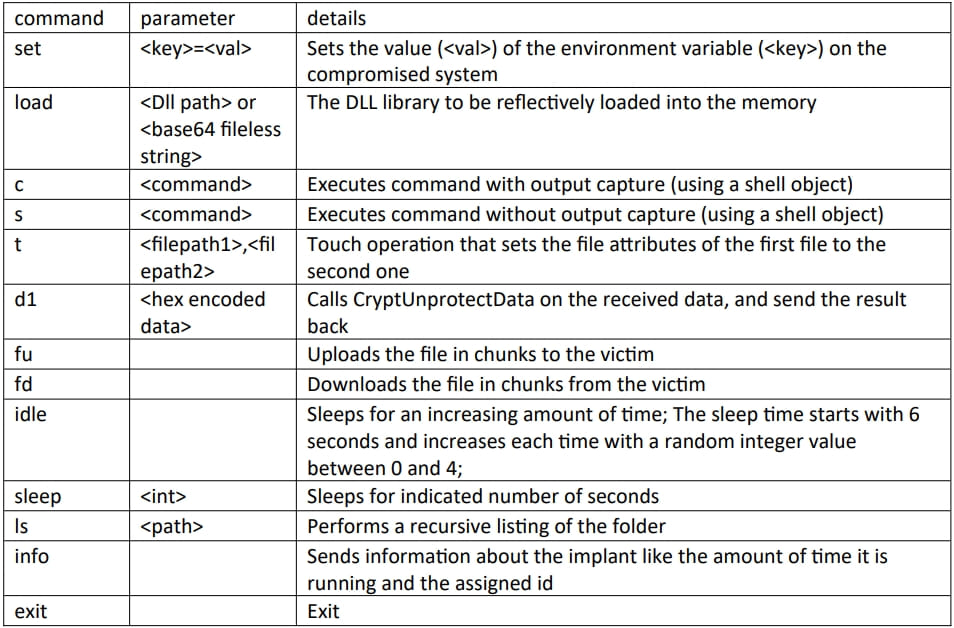
Logutil communicates directly with the C2 and gets the commands to execute, as explained in the table below:
Researchers point out that Logutil’s C2 contains references to ESXi and Linux, so it’s likely that threat actors are already using Go’s versatility to create a cross-platform backdoor.
Bitdefender shared a comprehensive list of indicators of compromise in its report, so defenders are recommended to take note and apply multiple layers of overlapping security measures.
[ad_2]
Source link
