[ad_1]
A new ransomware group named “RA Group” targets pharmaceutical, insurance, wealth management and manufacturing companies in the United States and South Korea.
The new ransomware operation began in April 2023, when they launched a dark web data leak site to publish victims’ details and stolen data, engaging in the typical “double extortion” tactic used by most ransomware gangs.
While the extortion portal was launched on April 22, 2023, the first batch of victim organizations was released on April 27, including sample files, a description of the type of content that was stolen, and links to stolen data.
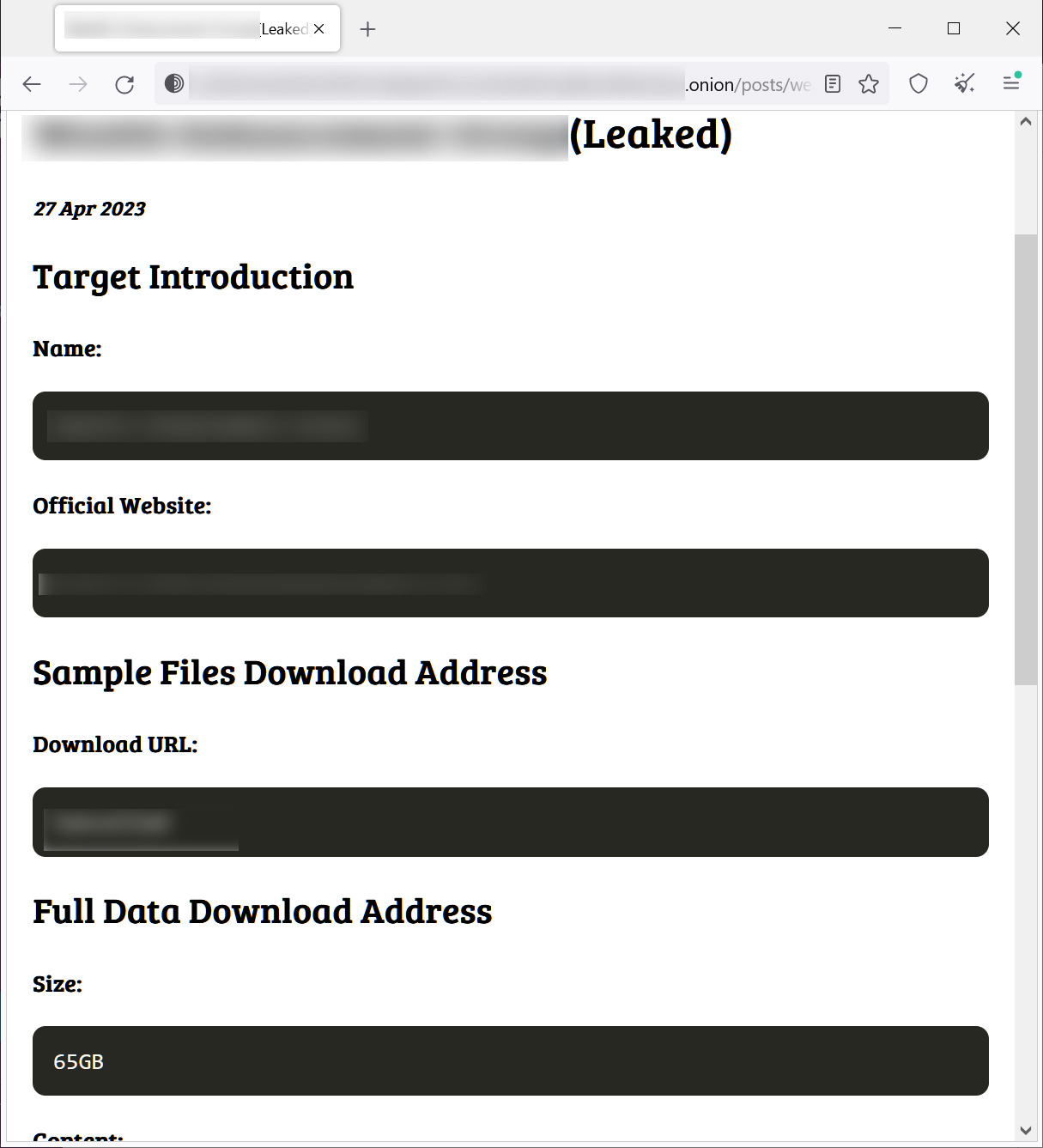
Source: BleepingComputer
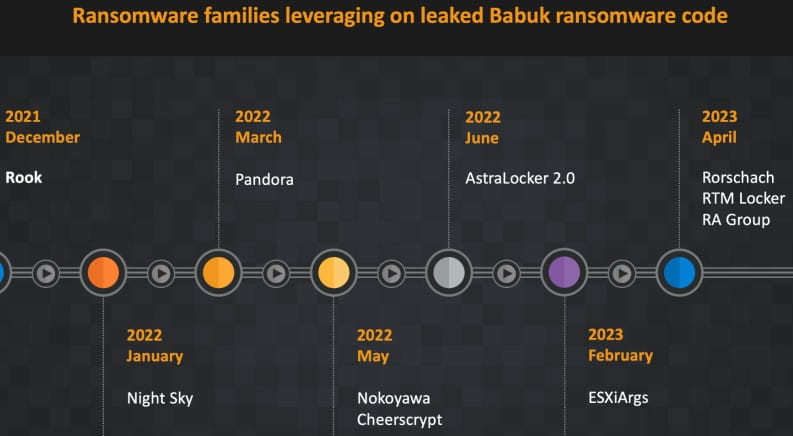
In a new report from Cisco Talosthe researchers explain that RA Group uses an encryptor based on the Babuk ransomware source code leakeda ransomware operation that stopped in 2021.
Last week, Sentinel Labs reported that at least nine separate ransomware operations use Babuk source code that was leaked on a Russian-speaking hacker forum in September 2021, as it gives threat actors an easy way to expand their reach to cover Linux and VMware ESXi.
In addition to the ransomware groups cited in the Sentinel Labs report as Babuk users, Cisco Talos also mentions Rook, Night Sky, Pandora, Nokoyawa, Cheerscrypt, AstraLocker 2.0, and ESXiArgs.
Details of the attack of the RA group
A notable feature of RA Group is that each attack carries a personalized ransom note written specifically for the targeted organization, while the executable also bears the victim’s name.
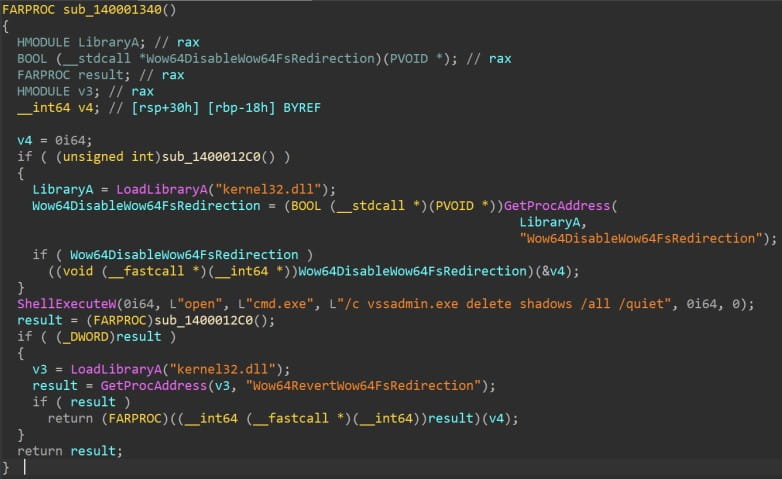
The ransomware targets all logical drives on the victim’s machine and network shares and attempts to encrypt specific folders excluding those related to Windows system, startup, program files, etc.
This is to avoid rendering the victim’s system unusable, thus making the payment of a ransom unlikely.
The RA Group encryptor uses intermittent encryption, which alternates between encrypting and unencrypting sections of a file to speed up the encryption of a file. However, this approach can be risky because it allows partial recovery of some data from files.
When encrypting data, the encryptor will use curve25519 and eSTREAM hc-128 encryption algorithms.
Encrypted files are appended with the filename extension “.GAGUP” while all Volume Shadow Copies and Recycle Bin contents are erased to prevent easy data restoration.
The ransom note dropped on the victim’s system is named ‘How to restore your .txt files‘ and forces the victim to use qTox messaging to contact threat actors and negotiate a ransom.
The note also includes a link to a repository containing files stolen from the victim as evidence of the data breach.
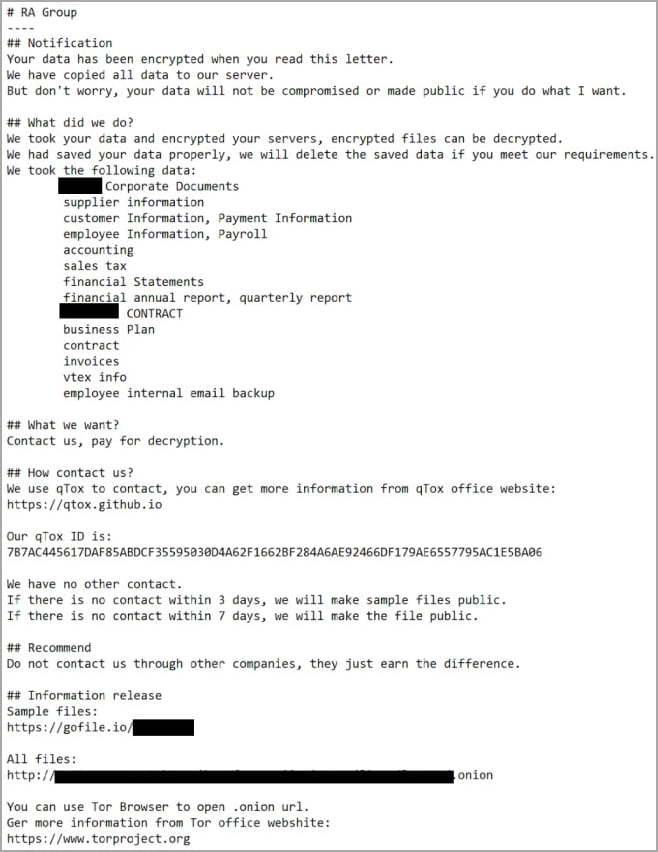
Threat actors claim to give victims three days before a sample of stolen data is posted on extortion sites, but like other ransomware operations, this is likely open to negotiation.
As this is a relatively new ransomware operation, with only a few victims, it is unclear how they breach systems and spread laterally across a network.
[ad_2]
Source link
