[ad_1]

A previously undocumented Python backdoor targeting VMware ESXi servers has been spotted, allowing hackers to execute commands remotely on a compromised system.
VMware ESXi is a virtualization platform commonly used in the enterprise to host many servers on a single device while using CPU and memory resources more efficiently.
The new backdoor was discovered by Juniper Networks Researchers, which found the backdoor on a VMware ESXi server. However, they could not determine how the server was compromised due to limited log retention.
They believe the server may have been compromised using the CVE-2019-5544 and CVE-2020-3992 vulnerabilities in ESXi’s OpenSLP service.
While the malware is technically capable of targeting Linux and Unix systems as well, Juniper analysts found several indications that it was designed for attacks against ESXi.
Backdoor Operation
The new python backdoor adds seven lines to “/etc/rc.local.d/local.sh”, one of the few ESXi files that survives between reboots and is executed on startup.
Usually this file is empty except for some advisory comments and an exit statement.
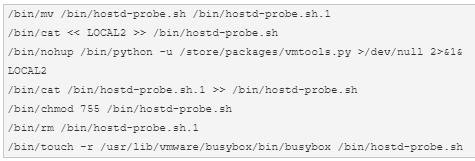
One of these lines launches a Python script saved under “/store/packages/vmtools.py”, in a directory that stores VM disk images, logs, etc.
The name and location of the script leads Juniper Networks to believe that the malware operators intend to specifically target VMware ESXi servers.
“Although the Python script used in this attack is cross-platform and can be used with little or no modification on Linux or other UNIX-like systems, there are several indications that this attack was designed specifically to target ESXi,” explains Juniper Networks. report.
“The file name and location, /store/packages/vmtools.py, was chosen to arouse little suspicion on a virtualization host.”
“The file begins with a VMware copyright consistent with the publicly available examples and is extracted character-by-character from an existing Python file provided by VMware.”
This script launches a web server that accepts password-protected POST requests from remote threat actors. These requests can carry a base-64 encoded command payload or launch a reverse shell on the host.
Reverse shell forces the compromised server to initiate connection with the threat actor, a technique that is often used to circumvent firewall restrictions or circumvent limited network connectivity.
One of the threat actor actions observed by Juniper analysts was to modify the configuration of the ESXi reverse HTTP proxy to allow remote access to communicate with the crashed web server.
Since the file used to set this new configuration, “/etc/vmware/rhttpproxy/endpoints.conf”, is also backed up and restored after reboot, any changes in it are persistent.
Mitigation
To determine if this backdoor has impacted your ESXi servers, check for the existence of the files mentioned above and additional lines in the “local.sh” file.
Any configuration files that persist across reboots should be examined for suspicious changes and reversed with the correct settings.
Finally, administrators should restrict all incoming network connections to trusted hosts, and available security updates that patch exploits used for the initial compromise should be applied as soon as possible.
[ad_2]
Source link
