[ad_1]

New PowerShell-based malware called PowerExchange has been used in attacks linked to Iranian state hackers APT34 to hijack on-premises Microsoft Exchange servers.
After infiltrating the mail server via a phishing email containing an archived malicious executable, the threat actors deployed a web shell named ExchangeLeech (first observed by the Digital14 Incident Response team in 2020) that can steal user credentials.
The FortiGuard Labs threat research team discovered the PowerExchange backdoor on the compromised systems of a government organization in the United Arab Emirates.
Notably, the malware communicates with its command-and-control (C2) server via emails sent using the Exchange Web Services (EWS) API, sending stolen information, and receiving encoded commands. base64 via text attachments to emails with “Microsoft Edge Update”. subject.
“Using the victim’s Exchange server for the C2 channel allows the backdoor to blend in with benign traffic, ensuring that the threat actor can easily avoid almost all network-based detection and remediation at inside and outside the target organization’s infrastructure,” FortiGuard Labs Threat said. The research team said.
The backdoor allows its operators to execute commands to deliver additional malicious payloads to hacked servers and exfiltrate harvested files.
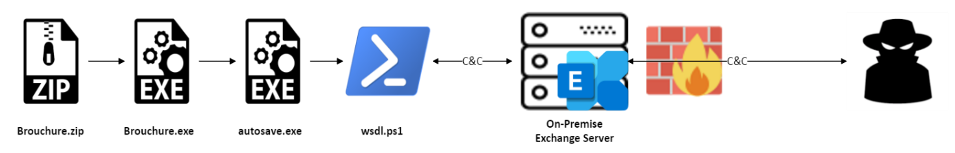
During the forensic investigation of the network, researchers also discovered other stolen terminals with various other malicious implants.
Among them they found the ExchangeLeech web shell, installed as a file named System.Web.ServiceAuthentication.dll which mimicked legitimate IIS file naming conventions.
ExchangeLeech collects the usernames and passwords of those connecting to compromised Exchange servers using basic authentication by monitoring plaintext HTTP traffic and capturing credentials from web form data or HTTP headers.
Attackers can instruct the web shell to send the credential log via cookie settings.
FortiGuard Labs linked these attacks to Iranian state-backed hacking group APT34 (aka Oilrig) based on similarities between PowerExchange and the TriFive malware they used to hijack the servers of Kuwaiti government organizations.
“The two backdoors share striking commonalities: they are written in PowerShell, activated by a periodic scheduled task, and the C2 channel leverages the organization’s Exchange server with the EWS API. And although their code is very different , we assume that PowerExchange is a new and improved form of TriFive,” the researchers said.
APT34 also uses phishing emails as an initial infection vector in its attacks and has previously breached other UAE entities, according to the Fortiguard Labs report.
[ad_2]
Source link
