[ad_1]

Microsoft says a Chinese cyber espionage group it is tracking as Volt Typhoon has been targeting critical infrastructure organizations across the United States, including Guam, since at least mid-2021.
Their victims span a wide range of critical sectors, including government, navy, communications, manufacturing, information technology, utilities, transportation, construction, and education.
“Microsoft assesses with moderate confidence that this Volt Typhoon campaign continues the development of capabilities that could disrupt critical communications infrastructure between the United States and the Asian region in future crises,” the Microsoft Threat Intelligence team said. said.
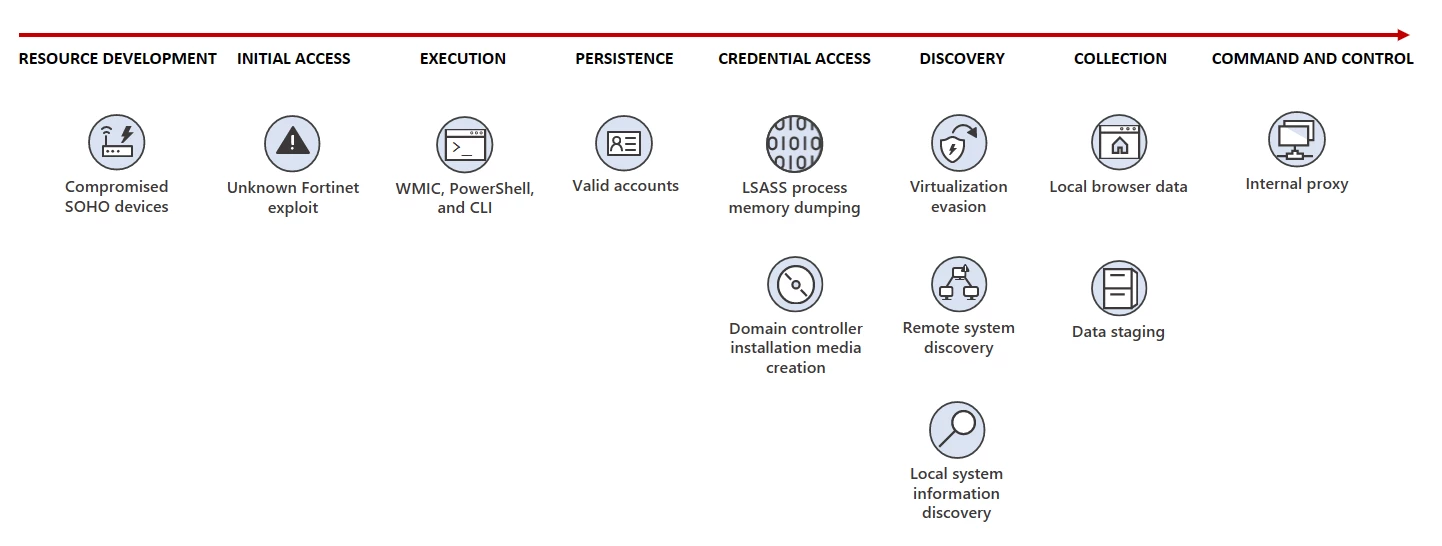
The initial attack vector is the compromise of Fortinet FortiGuard devices exposed to the Internet by exploiting an unknown zero-day vulnerability.
After breaching the targets’ networks, they launch what Microsoft describes as “living-off-the-land” attacks with hands-on keyboard activity and living-off-the-land binaries (LOLBins) such as PowerShell, Certutil, Netsh, and the Windows Management Instrumentation (WMIC) command line.
However, they have also been seen using open source tools such as Fast Reverse Proxy (frp), credential theft tool Mimikatz and networking framework Impacket, according to a joint council released today by the FBI, NSA, CISA, and cybersecurity agencies in Australia, New Zealand, the United Kingdom, and Canada.
To ensure that their malicious activities mix with legitimate network traffic to evade detection, Volt Typhoon uses compromised Small Office and Home Office (SOHO) network equipment from ASUS, Cisco, D-Link, Netgear, FatPipe and Zyxel, such as routers, firewalls, and VPN devices.
Leveraging the privileged access gained after compromising Fortinet devices allows state hackers to dump credentials through the Local Security Authority Subsystem Service (LSASS).
The stolen credentials allow them to deploy Awen-based web shells for data exfiltration and persistence on hacked systems.
As Mandiant Intelligence chief analyst John Hultquist told BleepingComputer, these intrusions into U.S. critical infrastructure organizations are likely part of a concerted effort to provide access to China in the event of a future conflict between the two countries.
“There are a variety of reasons actors target critical infrastructure, but a persistent focus on these sectors may indicate readiness for a disruptive or destructive cyberattack,” Hultquist said.
“States carry out long-term intrusions into critical infrastructure to prepare for a possible conflict, as it may simply be too late to access them in the event of a conflict. Similar emergency intrusions are regularly carried out by states .
“Over the past decade, Russia has targeted a variety of critical infrastructure sectors in operations that we believe were not designed for immediate effect. China has done the same in the past, targeting the oil and gas sector. These operations are aggressive and potentially dangerous, but they do not necessarily indicate that attacks are looming.”
In accordance with its standard procedures for dealing with nation-state actor activity, Microsoft says it has proactively reached out to all customers who were targeted or compromised in these attacks to provide them with the information necessary to secure their networks against future hacking attempts.
[ad_2]
Source link
