[ad_1]

A new information-stealing malware named MacStealer targets Mac users, stealing their credentials stored in the iCloud KeyChain and web browsers, cryptocurrency wallets and potentially sensitive files.
MacStealer is distributed as malware-as-a-service (MaaS), where the developer sells pre-built versions for $100, allowing buyers to deliver the malware to their campaigns.
According to Uptycs Threat Research Team who discovered the new macOS malware, it can run on macOS Catalina (10.15) and up to the latest version of Apple’s operating system, Ventura (13.2).
Target Mac users
MacStealer was discovered by Uptycs analysts on a dark web hacking forum where the developer has been promoting it since earlier this month.
The vendor claims that the malware is still in an early beta development phase and does not offer any panels or builders. Instead, it sells pre-built DMG payloads that can infect macOS Catalina, Big Sur, Monterey, and Ventura.
The threat actor uses the lack of a builder and panel to justify the low $100 price tag for the malware, but promises that more advanced features are coming soon.
The malware developer claims that MacStealer can steal the following data from compromised systems:
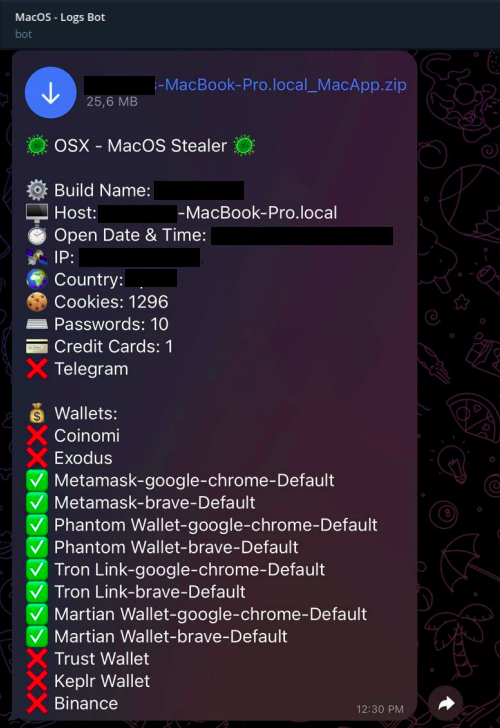
- Account passwords, cookies and credit card details from Firefox, Chrome and Brave.
- TXT, DOC, DOCX, PDF, XLS, XLSX, PPT, PPTX, JPG, PNG, CSV, BMP, MP3, ZIP, RAR, PY and DB files
- Extract the Keychain database (login.keychain-db) in base64 encoded form
- Collect system information
- Collect keychain password information
- Coinomi, Exodus, MetaMask, Phantom, Tron, Martian Wallet, Trust wallet, Keplr Wallet and Binance cryptocurrency wallets
The Keychain database is a secure storage system in macOS that holds users’ passwords, private keys, and certificates, encrypting them with their login password. The feature can then autofill login credentials on web pages and apps.
Malware functionality
Threat actors distribute MacStealer as an unsigned DMG file that poses as something the victim is tricked into running on their macOS.
By doing so, a fake password prompt is sent to the victim to execute a command which allows the malware to collect passwords from the compromised machine.
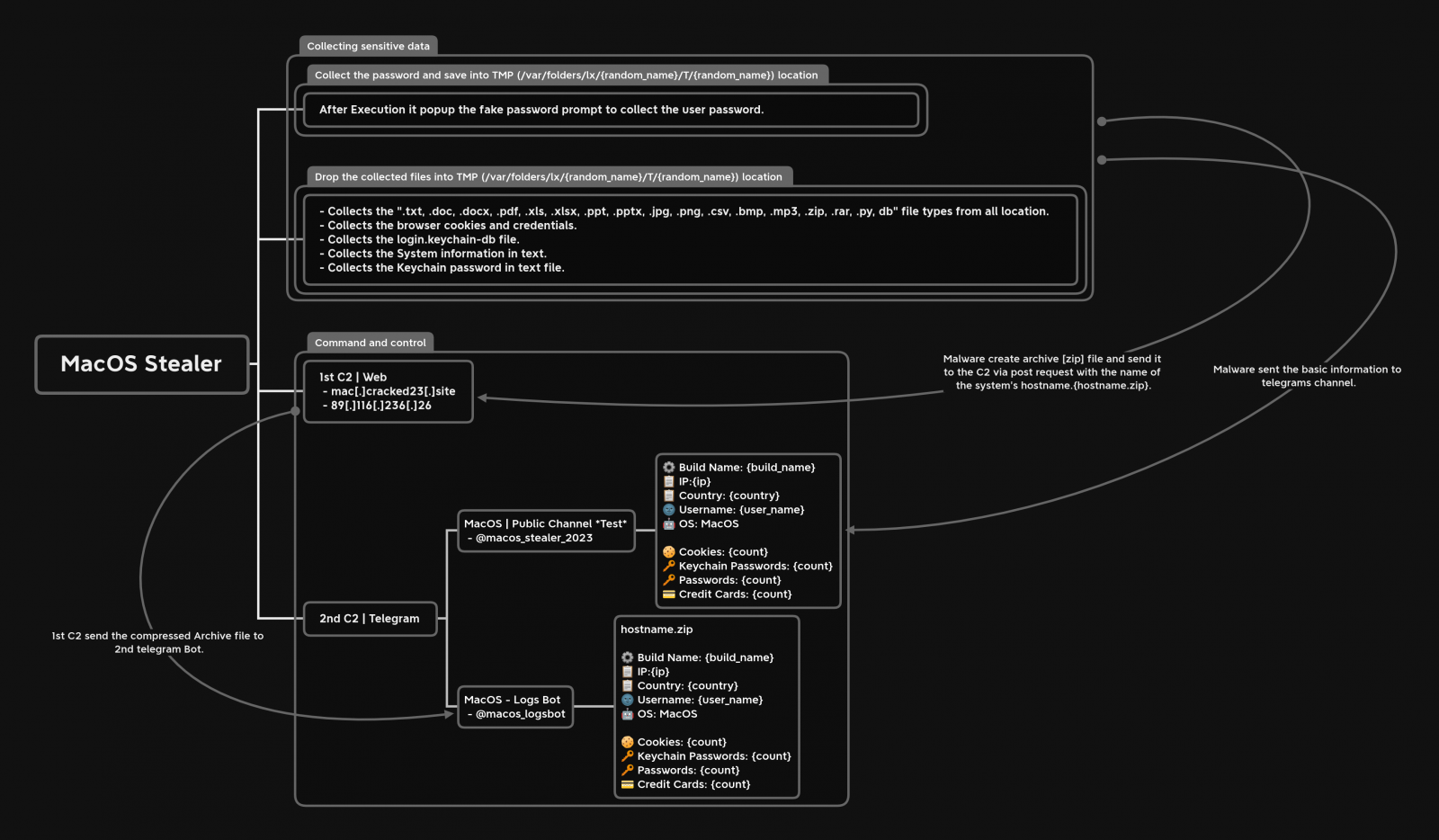
The malware then collects all the data mentioned in the previous section, stores it in a ZIP file and sends the stolen data to remote command and control servers for later collection by the threat actor.
At the same time, MacStealer sends basic information to a pre-configured Telegram channel, allowing the operator to be quickly notified when new data is stolen and to download the ZIP file.
While most MaaS operations target Windows users, macOS is not immune to these threats. So its users must stay alert and avoid downloading files from untrustworthy websites.
Last month, security researcher iamdeadlyz also discovered new Mac information-stealing malware distributed in a phishing campaign targeting ‘The Sandbox’ players block chain game.
This infostealer also targeted credentials saved in browsers and cryptocurrency wallets, including Exodus, Phantom, Atomic, Electrum, and MetaMask.
With cryptocurrency wallets being highly targeted by threat actors, we are likely to see other malware developers targeting macOS in their search for cryptocurrency wallets to steal.
[ad_2]
Source link
