[ad_1]

New variants of IcedID have been found without the usual online banking fraud functionality and instead focus on installing new malware on compromised systems.
According point of proofthese new variants have been used by three separate threat actors in seven campaigns since the end of last year, focusing on delivering additional payloads, including ransomware.
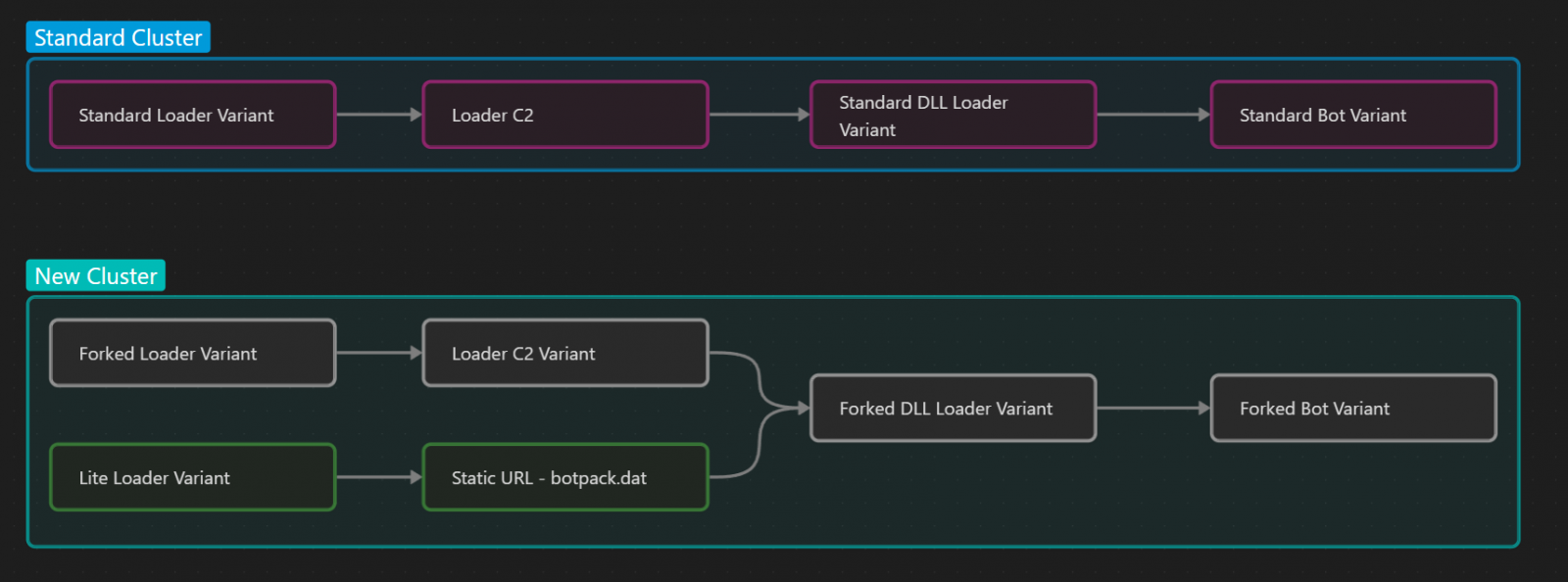
Proofpoint has identified two new variants of the IcedID loader, namely “Lite” (first seen in November 2022) and “Forked” (first seen in February 2023), both providing the same IcedID bot with a set more targeted features.
Removing unnecessary functions on IcedID, which has been deployed in numerous malicious campaigns without many code changes since 2017, makes it more stealthy and lightweight, which can help threat actors evade detection.
New IcedID campaigns
From November 2022, the “Light” variant of the IcedID loader was delivered as a second stage payload on systems infected with the Emotet malware recently returned.
The “forked” version of the malware loader first appeared in February 2023, distributed directly via thousands of personalized invoice-themed phishing emails.
These messages used Microsoft OneNote attachments (.one) to execute a malicious HTA file which in turn executes a PowerShell command that retrieves IcedID from a remote resource. At the same time, the victim receives a decoy PDF.

In late February, Proofpoint researchers observed a low-volume campaign distributing “Forked” IcedID via bogus National Traffic and Motor Vehicle Safety Act and U.S. Food and Drug Administration (FDA) notices.
It is important to note that while some threat actors use new IcedID malware variants, others still choose to deploy the “Standard” variant, with one of the most recent campaigns dating from March 10, 2023.
The new variants
The “Forked” IcedID loader is quite similar to the “Standard” version in terms of role, sending basic host information to C2 and then retrieving the IcedID bot.
However, “Forked” uses a different file type (COM server) and has an additional domain and string decryption code, which makes the payload 12KB larger than the “Standard” version.
On the other hand, the “Lite” loader variant is lighter, at 20 KB, and does not exfiltrate information from the host to the C2. This change makes sense since it was rolled out alongside Emotet, which had already profiled the hacked system.
The “Forked” version of the IcedID bot is 64 KB smaller than the “Standard” bot, and is basically the same malware minus the web injection system, AiTM (adversary in the middle) functions, and backconnect capabilities that give remote threat actors access to infected devices.
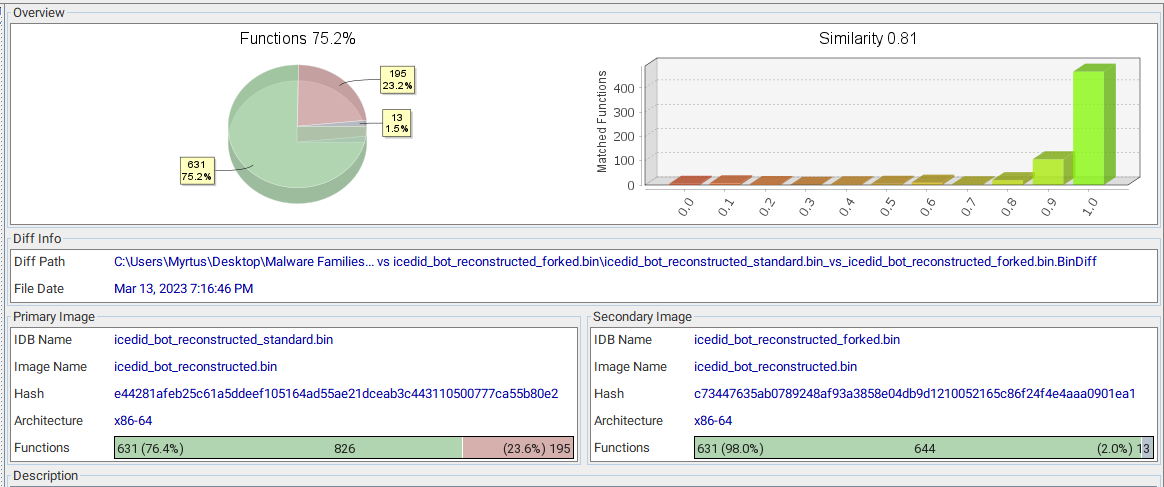
IcedID is typically used for initial access by threat actors, so the development of new variants is a worrying sign, signifying a move towards bot specialization for payload delivery.
Proofpoint predicts that most threat actors will continue to use the “Standard” variant, but the deployment of new versions of IcedID will likely increase, and other variants may appear later in 2023.
[ad_2]
Source link
