[ad_1]

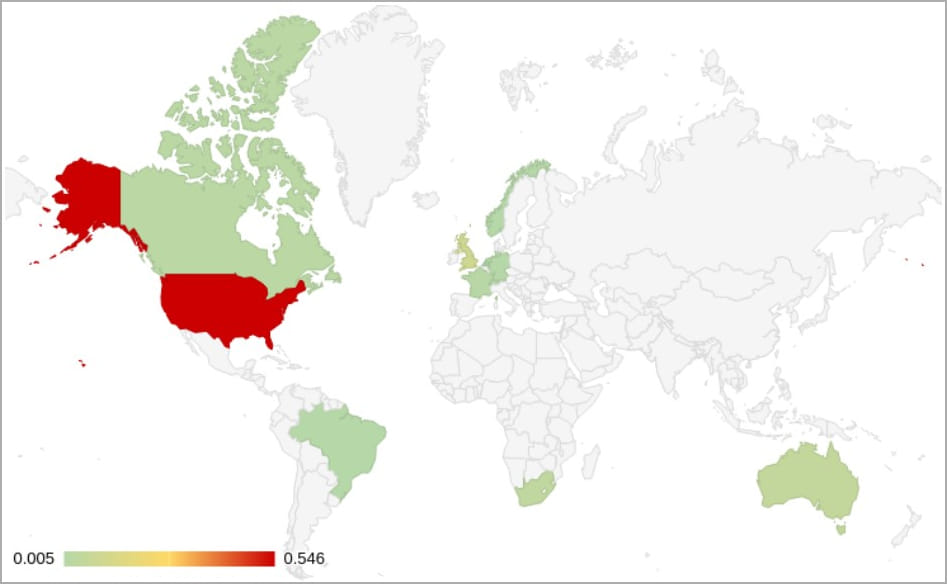
The Phishing-as-a-Service (PhaaS) platform codenamed “Greatness” has seen a spike in activity as it targets organizations using Microsoft 365 in the US, Canada, UK, Australia and South Africa.
The Microsoft 365 cloud-based productivity platform is used by many organizations around the world, making it a valuable target for cybercriminals trying to steal data or credentials for use in breaches network.
In a new report from Cisco Talos, researchers explain how the Greatness phishing platform launched in mid-2022, peaking in December 2022 and again in March 2023.
Most of the victims are in the United States, and many work in manufacturing, healthcare, technology, education, real estate, construction, finance and business services.
Attacks of “grandeur”
Greatness Phishing-as-a-Service contains everything a budding phishing actor needs to run a successful campaign.
To launch an attack, the Services user accesses the ‘Greatness’ admin panel using their API key and providing a list of target email addresses.
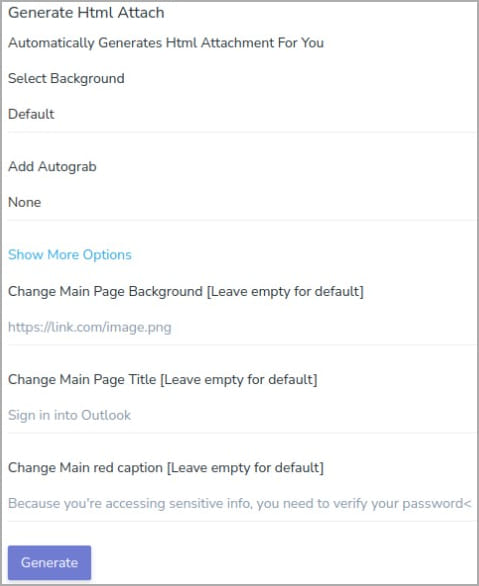
The PhaaS platform allocates the necessary infrastructure, such as the server that will host the phishing page, as well as to generate the HTML attachment.
The Affiliate then crafts the content of the email and provides any other materials or changes to the default settings as needed.
The service then sends an email to the victims, who receive a phishing email with an HTML attachment. When this attachment is opened, an obfuscated JavaScript code is executed in the browser to connect to the “Greatness” server to retrieve the phishing page that will be displayed to the user.
The phishing service will automatically inject the target’s company logo and background image from the employer’s actual Microsoft 365 login page.
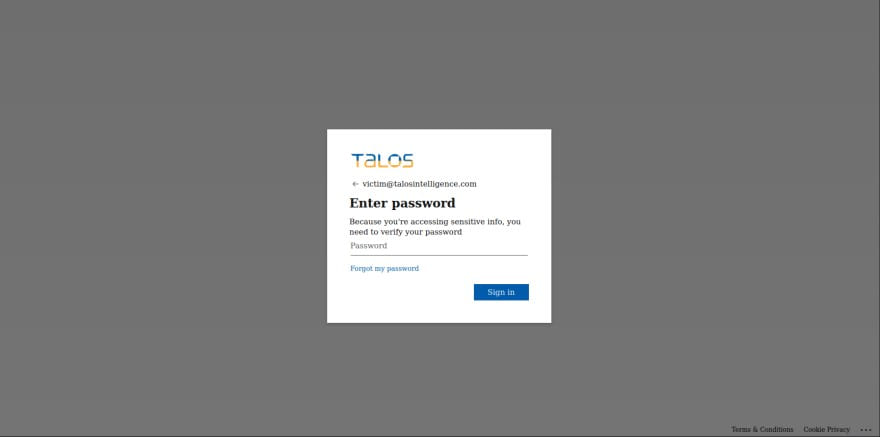
The victim only enters their password on the convincing phishing page because Greatness pre-fills the correct email to create a sense of legitimacy.
At this point, the phishing platform acts as a proxy between the victim’s browser and the actual Microsoft 365 login page, handling the authentication flow to obtain a valid session cookie for the target account.
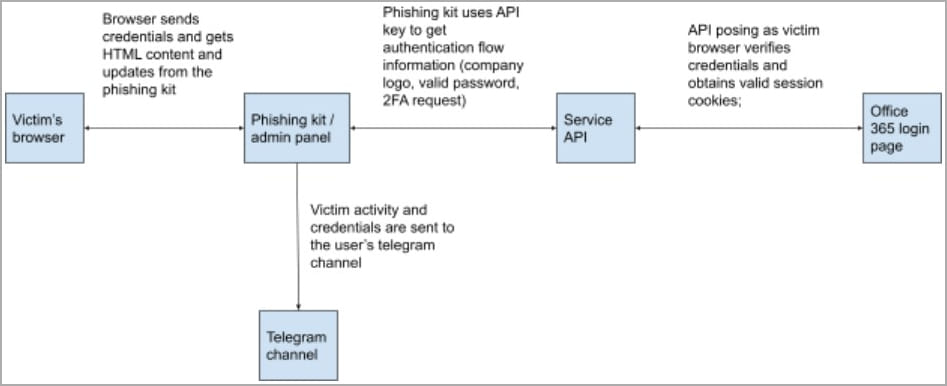
If the account is protected by two-factor authentication, Greatness will prompt the victim to provide it while triggering a request on the real Microsoft service, so that the one-time code is sent to the target’s device.
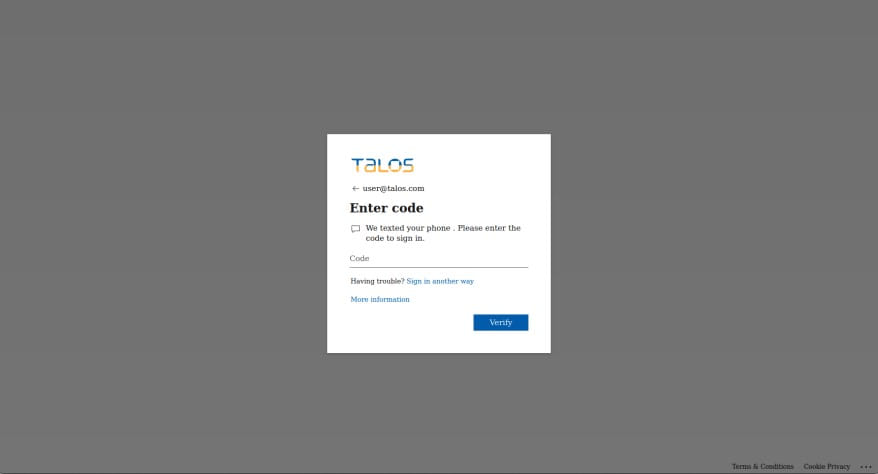
Once the MFA code is provided, Greatness will authenticate itself as a victim on the real Microsoft platform and send the authenticated session cookie to the affiliate via a Telegram channel or on the web panel of the service.
“Authenticated sessions usually time out after some time, which may be one of the reasons the telegram bot is used – it notifies the attacker of valid cookies as soon as possible to ensure they can reach quickly if the target is interesting”, explains Cisco.
From there, attackers can use this session cookie to gain access to a victim’s emails, files, and data in Microsoft 365 services.
In many cases, stolen credentials are also used to breach corporate networks, leading to even more dangerous attacks, such as the deployment of ransomware.
[ad_2]
Source link
