[ad_1]

A new Go-based malware botnet named “GoTrim” scans the web for self-hosted WordPress websites and attempts to brute force the admin password and take over the site.
This compromise can lead to the deployment of malware, the injection of credit card stealing scripts, the hosting of phishing pages and other attack scenarios, potentially affecting millions of people depending on the popularity of hacked websites.
The botnet is notorious in the cybercrime community, but Fortinet became the first cybersecurity company to analyze it, reporting that although the malware is still under development, it already has powerful capabilities.
GoTrim botnet targets WordPress sites
The GoTrim malware campaign spotted by Fortinet began in September 2022 and is still ongoing.
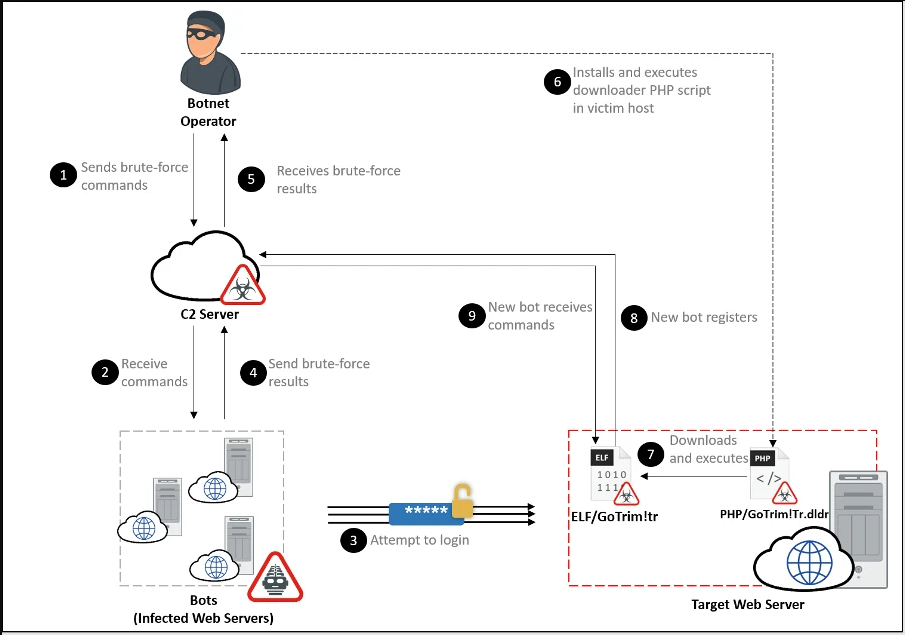
Malware operators provide a long list of target websites and a set of credentials to the botnet network. The malware then logs into each site and attempts to brute force administrator accounts using the entered credentials.
If successful, GoTrim connects to the hacked site and reports the new infection to the command and control (C2) server, including a bot ID in the form of a newly generated MD5 hash.
Then the malware uses PHP scripts to fetch GoTrim bot clients from a hard-coded URL and removes both the script and the brute force component from the infected system, as these are no longer needed.
The botnet can operate in two modes: “client” and “server”.
In client mode, the malware initiates the connection to the botnet’s C2, while in server mode, it starts an HTTP server and waits for incoming requests from C2.
If the hacked endpoint is directly connected to the internet, GoTrim defaults to server mode.
GoTrim sends beacon requests to C2 every two minutes, and if it doesn’t receive a response after 100 attempts, it terminates.
The C2 can send encrypted commands to the GoTrim bot, which supports the following:
- Validate Provided Credentials Against WordPress Domains
- Validate the provided credentials against Joomla! domains (not implemented)
- Validate provided credentials against OpenCart domains
- Validate provided credentials against Data Life Engine domains (not implemented)
- Detect the installation of WordPress, Joomla!, OpenCart or Data Life Engine CMS on the domain
- End the malware

Avoid detection
To evade detection by the WordPress security team, GoTrim will not target sites hosted on WordPress.com and will only target self-hosted sites.
This is done by checking the “Referer” HTTP header for “wordpress.com” and, if detected, stop targeting the site.
“As managed WordPress hosting providers, such as wordpress.com, typically implement more security measures to monitor, detect, and block brute force attempts than self-hosted WordPress websites, the chances of success are not are not worth the risk of being discovered,” the researchers explain.
Additionally, GoTrim mimics legitimate Firefox on 64-bit Windows requests to bypass anti-bot protections.
Finally, if the targeted WordPress site uses a CAPTCHA plugin to stop bots, the malware detects it and loads the corresponding solver. Currently, it supports seven popular plugins.
Fortinet also said that the GoTrim botnet avoids sites hosted on “1gb.ru”, but could not determine the exact reasons for this decision.
To mitigate the GoTrim threat, WordPress site owners should use strong administrator account passwords that are difficult to brute force or use a 2FA plugin.
Finally, WordPress admins should upgrade the core CMS software and all plugins active on the site to the latest available version, which fixes known vulnerabilities that hackers can exploit for an initial compromise.
[ad_2]
Source link
