[ad_1]

A previously undocumented data wiper named CryWiper poses as ransomware, extorting victims to pay for a decryptor, but in reality it simply destroys data beyond recovery.
CryWiper was first discovered by Kaspersky this fall, during attacks against organizations in the Russian Federation.
“In the fall of 2022, our solutions detected attempts by a previously unknown Trojan, which we named CryWiper, to attack the network of an organization in the Russian Federation,” explains the new report by Kaspersky.
As code analysis reveals, CryWiper’s data wipe function is not an error but a deliberate tactic to destroy target data.
Delete victim data
CryWiper is a 64-bit Windows executable named “browserupdate.exe” written in C++, configured to abuse many WinAPI function calls.
While running, it creates scheduled tasks to run every five minutes on the compromised machine.
.png)
Then it contacts a command and control server (C2) with the name of the victim’s machine. The C2 responds with a “run” or “don’t run” command, determining whether the wiper will activate or remain inactive.
Kaspersky reports seeing execution delays of 4 days (345,600 seconds) in some cases, likely added in the code to help confuse the victim as to the cause of the infection.
CryWiper will stop critical processes related to MySQL, MS SQL database servers, MS Exchange mail servers and MS Active Directory web services to release locked data for destruction.
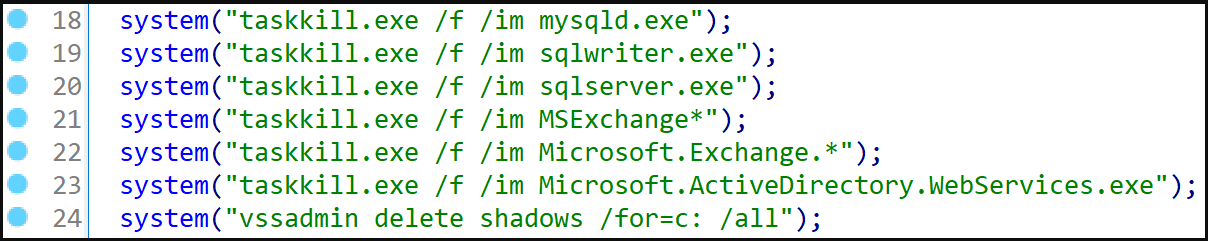
Then the malware deletes shadow copies on the compromised machine to prevent easy restoration of erased files.
CryWiper also modifies the Windows registry to prevent RDP connections, which can hamper remote IT specialists’ intervention and incident response.
Finally, the wiper will corrupt all listed files except “.exe”, “.dll”, “lnk”, “.sys”, “.msi” and its own “.CRY”, while also skipping System, Windows, and startup directories to avoid rendering the computer completely unusable.
The file corruption algorithm is based on “Mersenne Twister”, a pseudo-random number generator. This is the same algorithm used by IsaacWiper, but researchers have not established any other connection between the two families.
After this step, CryWiper will generate ransom note named “README.txt”, demanding 0.5 Bitcoin (about $8,000) in exchange for a decryptor. Unfortunately, this is a false promise, as corrupted data cannot be restored.
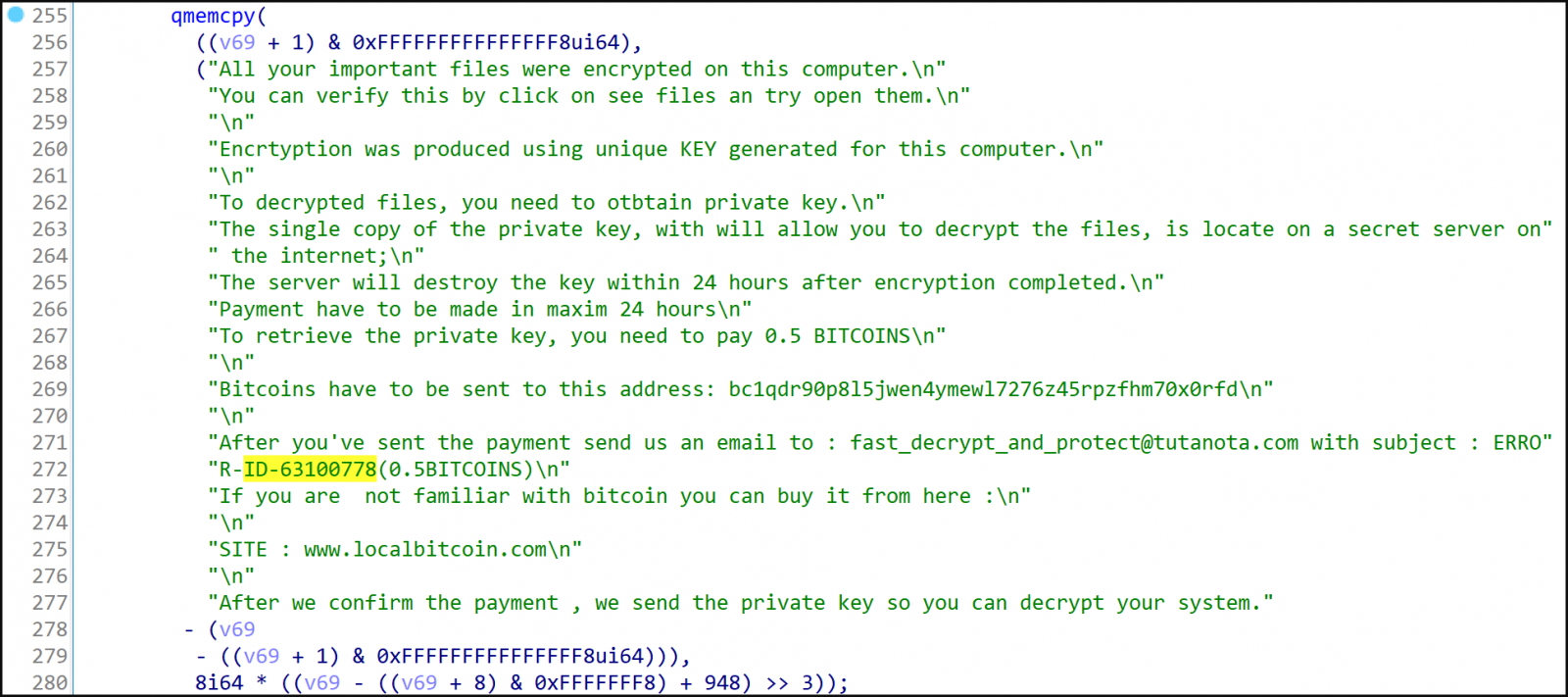
Even though CryWiper is not ransomware in the typical sense, it can still cause severe data destruction and business interruption.
Kaspersky says CryWiper does not appear to be associated with wiper families emerging in 2022, such as DoubleZero, IsaacWiper, Hermetic, CaddyWindscreen wiper, WhisperGate, Acid rainand Industry2.
[ad_2]
Source link
