[ad_1]

Security researchers have dissected a recently emerged ransomware strain dubbed “Big Head” that may be spread through malicious advertisements promoting fake Windows updates and fake Microsoft Word installers.
Two samples of the malware have already been analyzed by a cybersecurity company Fortinetwho examined the infection vector and how the malware executes.
Today, Trend Micro released a Big Head technical report one claiming that both variants and a third one they sampled come from a single operator who is likely experimenting with different approaches to optimizing their attacks.
Simulate a Windows Update
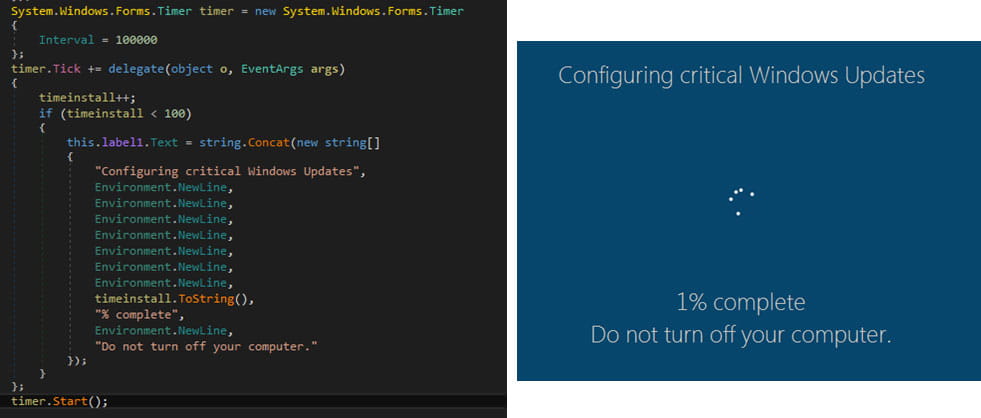
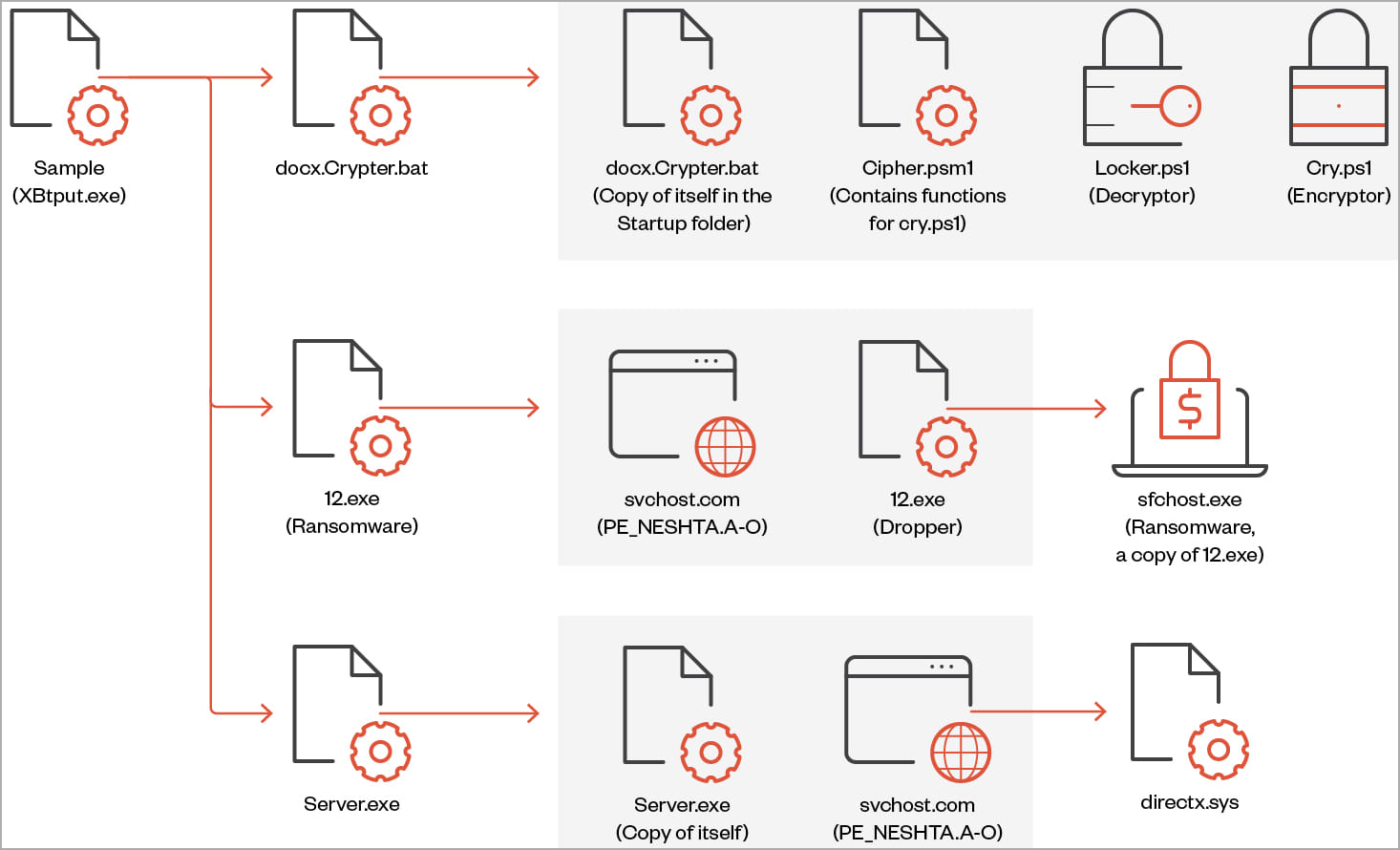
“Big Head” ransomware is a .NET binary that installs three AES-encrypted files on the target system: one is used to spread malware, another for Telegram bot communication, and the third encrypts files and can also show the user a fake Windows Update.
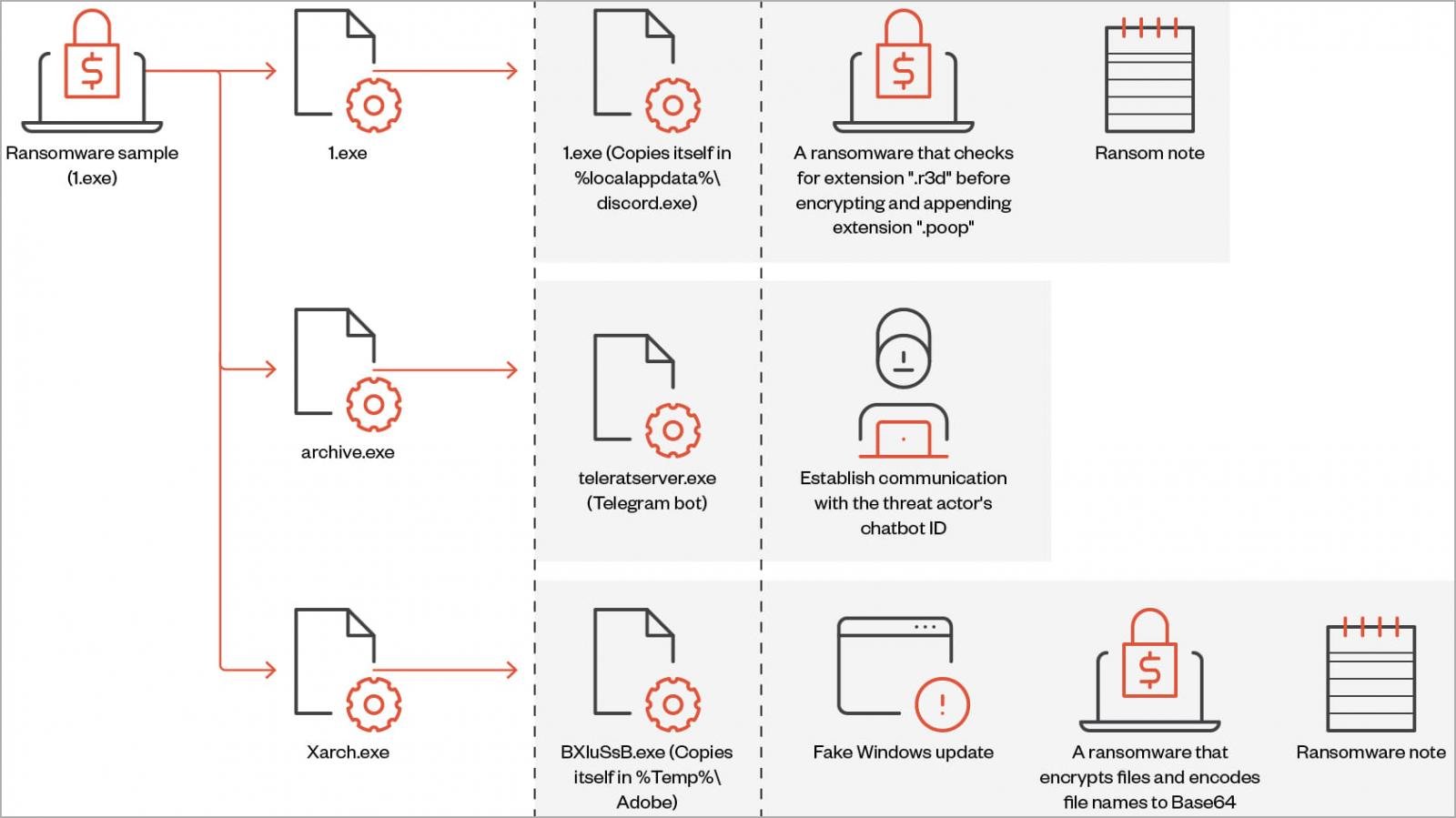
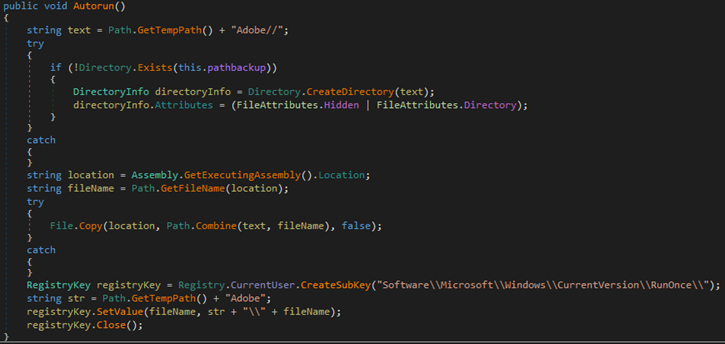
When executed, the ransomware also performs actions such as creating an autorun registry key, overwriting existing files if necessary, setting system file attributes, and disabling task manager.
Each victim is assigned a unique ID which is either taken from the %appdata%\ID directory or generated using a random string of 40 characters.
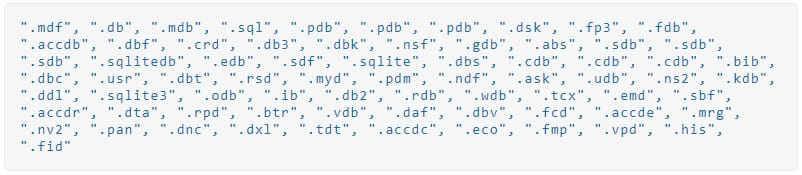
The ransomware deletes shadow copies to prevent easy system restore before encrypting targeted files and appending a “.poop” extension to their filenames.
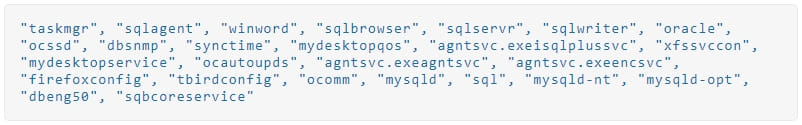
Additionally, Big Head will terminate the following processes to prevent tampering with the encryption process and to release data that the malware should lock.
The Windows, Recycle Bin, Program Files, Temp, Program Data, Microsoft and App Data directories are skipped from encryption to avoid rendering the system unusable.
Trend Micro found that the ransomware checks if it is running on a virtual box, checks the system language, and only performs encryption if it is not set to that of a Commonwealth of States member country. independent (former Soviet states).
During encryption, the ransomware displays a screen that pretends to be a legitimate Windows update.
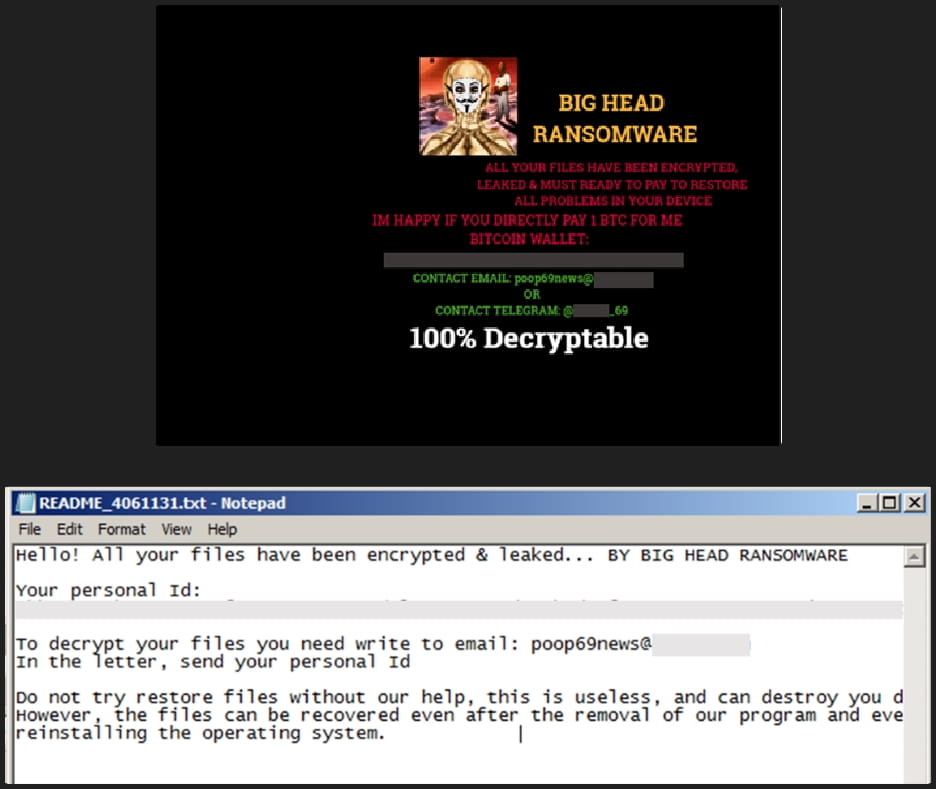
After the encryption process is completed, the following ransom is dropped on several directories and the victim’s desktop wallpaper is also changed to alert about the infection.
Other variants
Trend Micro has also analyzed two other variants of Big Head, highlighting some key differences from the standard ransomware version.
The second variant retains the capabilities of ransomware but also incorporates stealth behavior with functions to collect and exfiltrate sensitive data from the victim system.
The data this version of Big Head can steal includes browsing history, directory listing, installed drivers, running processes, product key and active networks, and it can also capture screenshots screen.
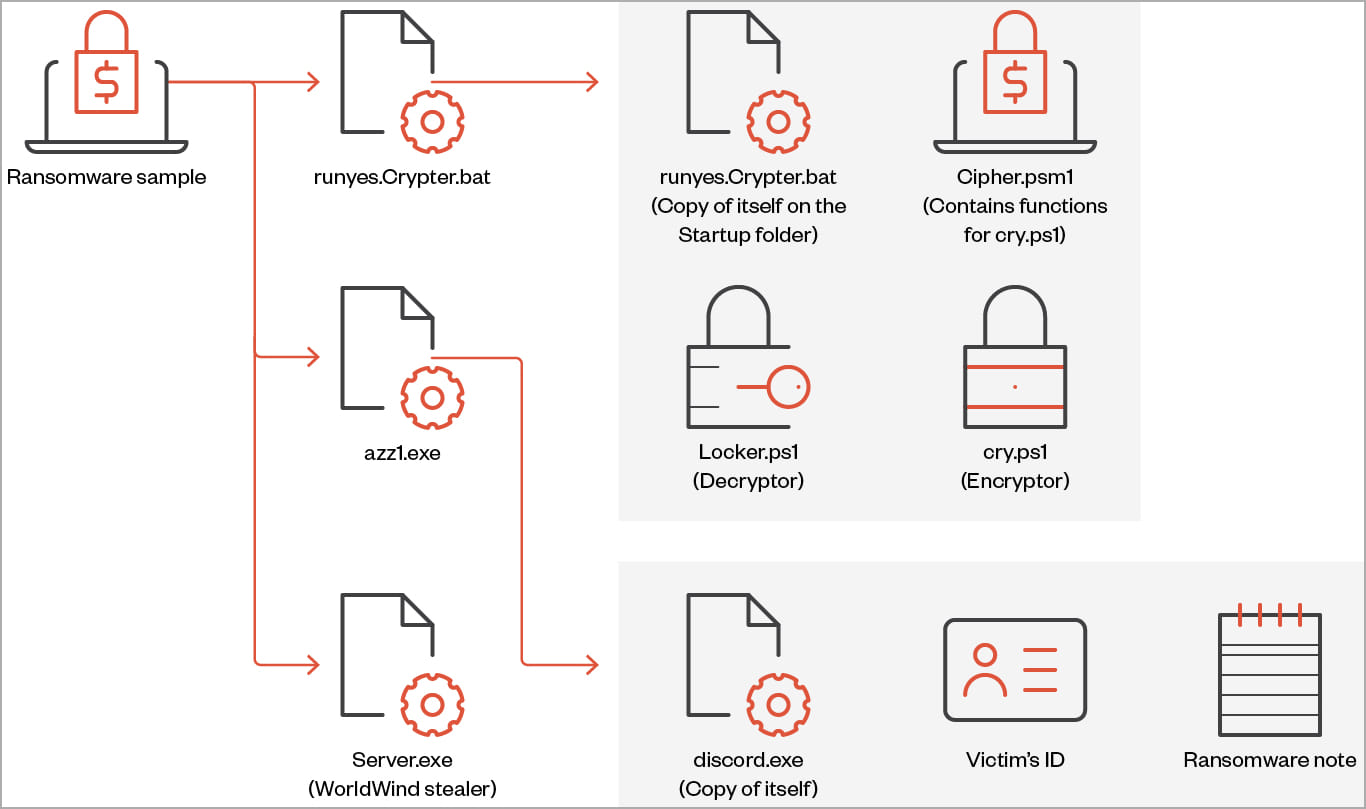
The third variant, discovered by Trend Micro, features a file infector identified as “Neshta”, which inserts malicious code into hacked system executables.
While the exact purpose of this operation is unclear, Trend Micro analysts believe it may be to evade detection that relies on signature-based mechanisms.
Notably, this variant uses a different ransom note and wallpaper than the other two, but it is still tied to the same threat actor.
Conclusion
Trend Micro comments that Big Head is not a sophisticated strain of ransomware, its encryption methods are fairly standard, and its evasion techniques are easy to detect.
Nonetheless, it seems to focus on consumers who may be tricked by simple tricks (e.g., a fake Windows update) or who find it difficult to understand safeguards needed to avoid cybersecurity risks.
The multiple variants in circulation suggest that the creators of Big Head are continually developing and refining the malware, experimenting with various approaches to see what works best.
[ad_2]
Source link
