[ad_1]

A novel Android banking malware named MMRat utilizes a rarely used communication method, protobuf data serialization, to more efficiently steal data from compromised devices.
MMRat was spotted for the first time by Trend Micro in late June 2023, primarily targeting users in Southeast Asia and remaining undetected on antivirus scanning services like VirusTotal.
While the researchers do not know how the malware is initially promoted to victims, they found that MMRat is distributed via websites disguised as official app stores.
The victims download and install the malicious apps that carry MMRat, usually mimicking an official government or a dating app, and grant risky permissions like access to Android’s Accessibility service during installation.
The malware automatically abuses the Accessibility feature to grant itself additional permissions that will allow it to perform an extensive range of malicious actions on the infected device.
MMRat capabilities
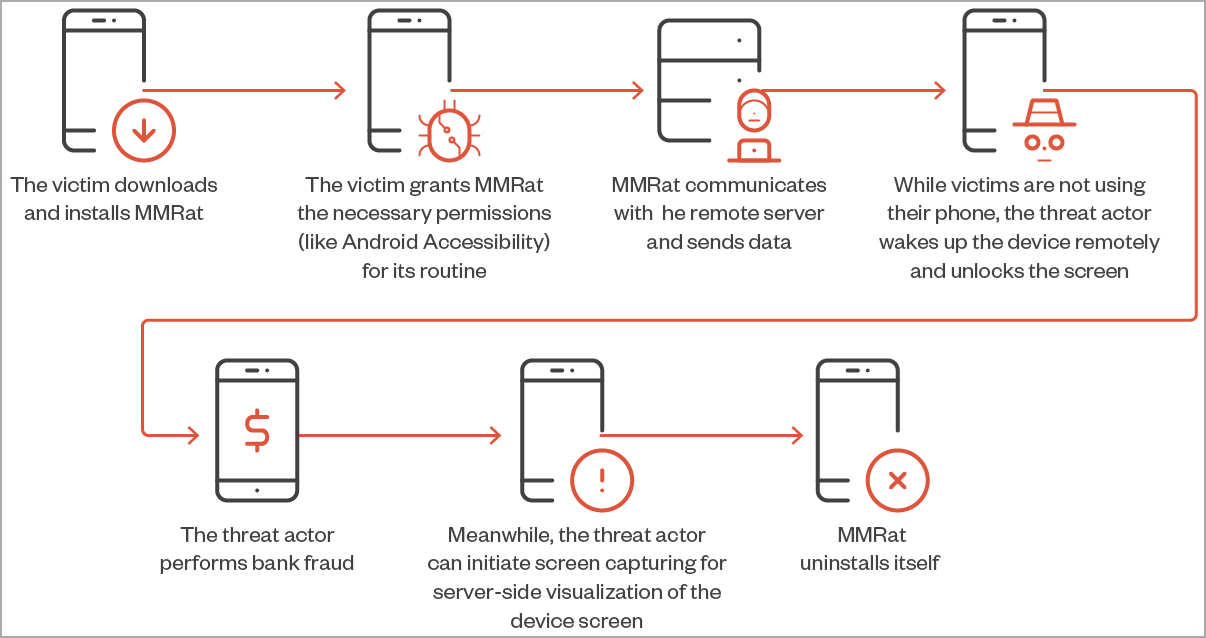
Once MMRat infects an Android device, it establishes a communication channel with the C2 server and monitors device activity to discover periods of idleness.
During that time, the threat actor abuses the Accessibility Service to wake up the device remotely, unlock the screen, and perform bank fraud in real-time.
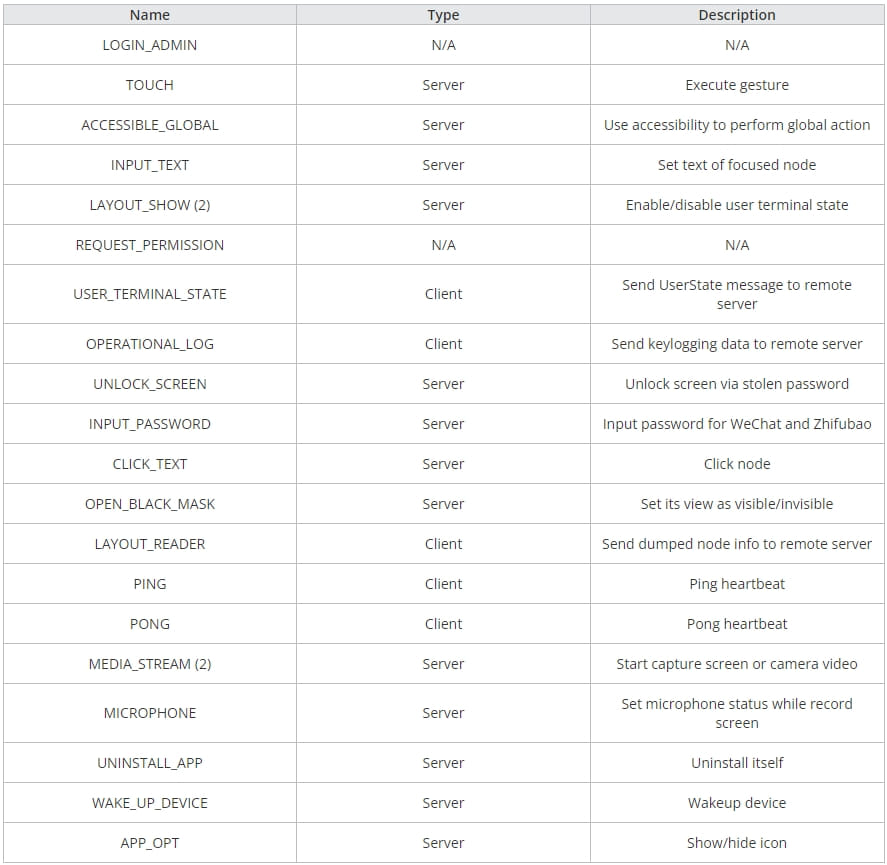
MMRat’s main functions can be summed up in the following:
- Collect network, screen, and battery information
- Exfiltrate the user’s contact list and list of installed apps
- Capture user input via keylogging
- Capture real-time screen content from the device by abusing the MediaProjection API
- Record and live-stream camera data
- Record and dump screen data in text form dumps that are exfiltrated to the C2
- Uninstall itself from the device to wipe all evidence of infection
MMRat’s ability to capture real-time screen content, and even its more rudimentary ‘user terminal state’ method that extracts text data requiring reconstruction, both demand efficient data transmission.
Without such efficiency, the performance would hinder threat actors from executing bank fraud effectively, which is why MMRat’s authors have opted to develop a custom Protobuf protocol for data exfiltration.
Protobuf advantage
MMRat uses a unique command and control (C2) server protocol based on protocol buffers (Protobuf) for efficient data transfer, which is uncommon among Android trojans.
Protobuf is a method for serializing structured data that Google developed, similar to XML and JSON, but smaller and faster.
MMRat uses different ports and protocols for exchanging data with the C2, like HTTP at port 8080 for data exfiltration, RTSP and port 8554 for video streaming, and custom Protobuf at 8887 for command and control.
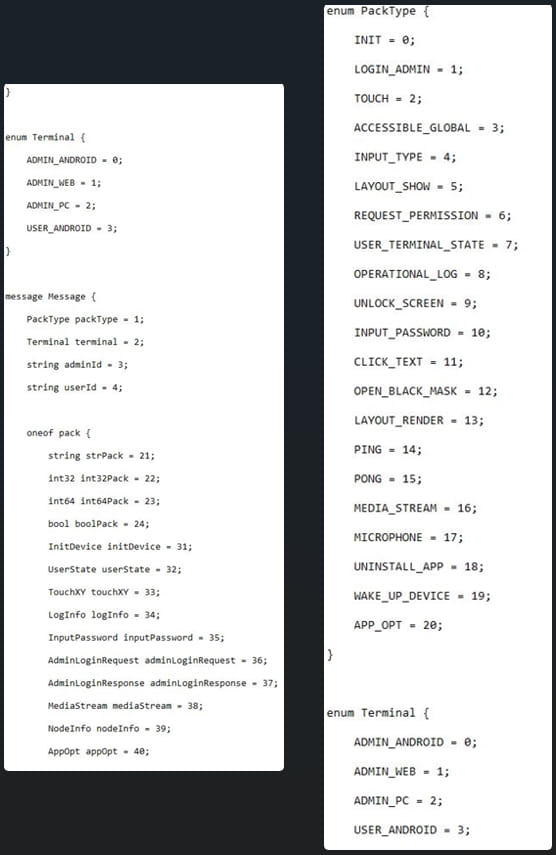
“The C&C protocol, in particular, is unique due to its customization based on Netty (a network application framework) and the previously-mentioned Protobuf, complete with well-designed message structures,” reads the Trend Micro report.
“For C&C communication, the threat actor uses an overarching structure to represent all message types and the “oneof” keyword to represent different data types.”
Apart from the efficiency of Protobuf, custom protocols also help threat actors evade detection by network security tools that look for common patterns of known anomalies.
Protobuf’s flexibility allows MMRat’s authors to define their message structures and organize how data is transmitted. At the same time, its structured nature ensures that sent data adhere to a predefined schema and are less likely to be corrupted at the recipient’s end.
In conclusion, MMRat shows the evolving sophistication of Android banking trojans, adeptly blending stealth with efficient data extraction.
Android users should only download apps from Google Play, check user reviews, only trust reputable publishers, and be cautious at the installation stage where they are requested to grant access permissions.
[ad_2]
Source link
