[ad_1]
A misconfigured Microsoft application allowed anyone to log in and modify Bing.com search results in real time, as well as inject XSS attacks to potentially breach Office 365 user accounts.
The security issue was discovered by Wiz Research, which named the attack “BingBang”.
Wiz analysts reported the issue to Microsoft on January 31, 2023, and the tech giant confirmed it was resolved on March 28, 2023.
A bad configuration
Wiz researchers discovered that when building an app in Azure App Services and Azure Functions, the app can be mistakenly configured to allow users in any Microsoft tenant, including public users, to login to the app.
This configuration setting is called “Support Account Types” and allows developers to specify whether a specific tenant, personal accounts, or a combination of multiple and personal accounts should be allowed to access the application.
This configuration option is offered for legitimate cases where developers need to make their applications available across organizational boundaries.
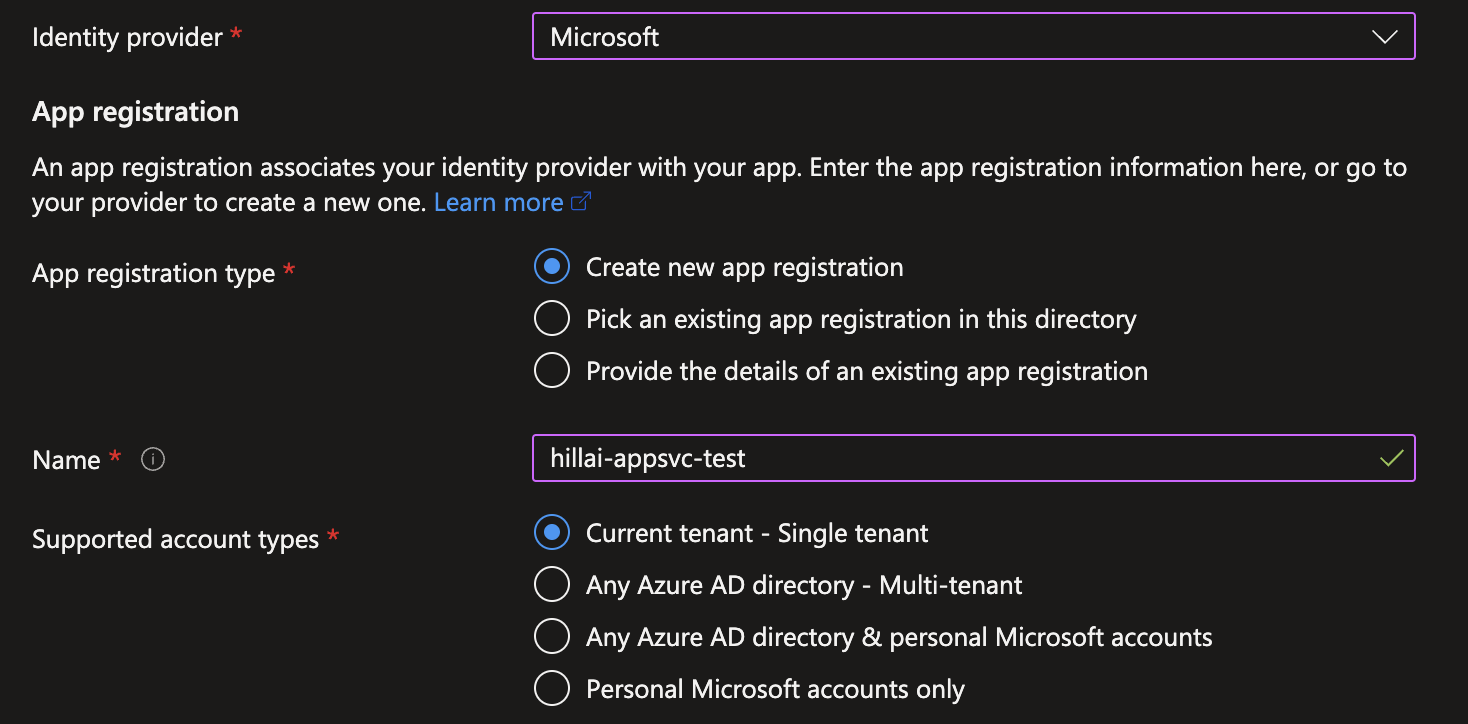
However, if a developer mistakenly assigns looser permissions, it could lead to unwanted access to the app and its features.
“This shared responsibility architecture is not always clear to developers, and as a result, validation and configuration errors are quite common,” comments Wiz in his report.
The magnitude of the misconfiguration problem is such that approximately 25% of multi-tenant applications analyzed by Wiz are misconfigured, allowing unconditional access without proper user validation.
In some cases, the misconfigured apps belonged to Microsoft, which shows how easy it is for administrators to make mistakes in configuring Azure AD.
BingBang and XSS attacks
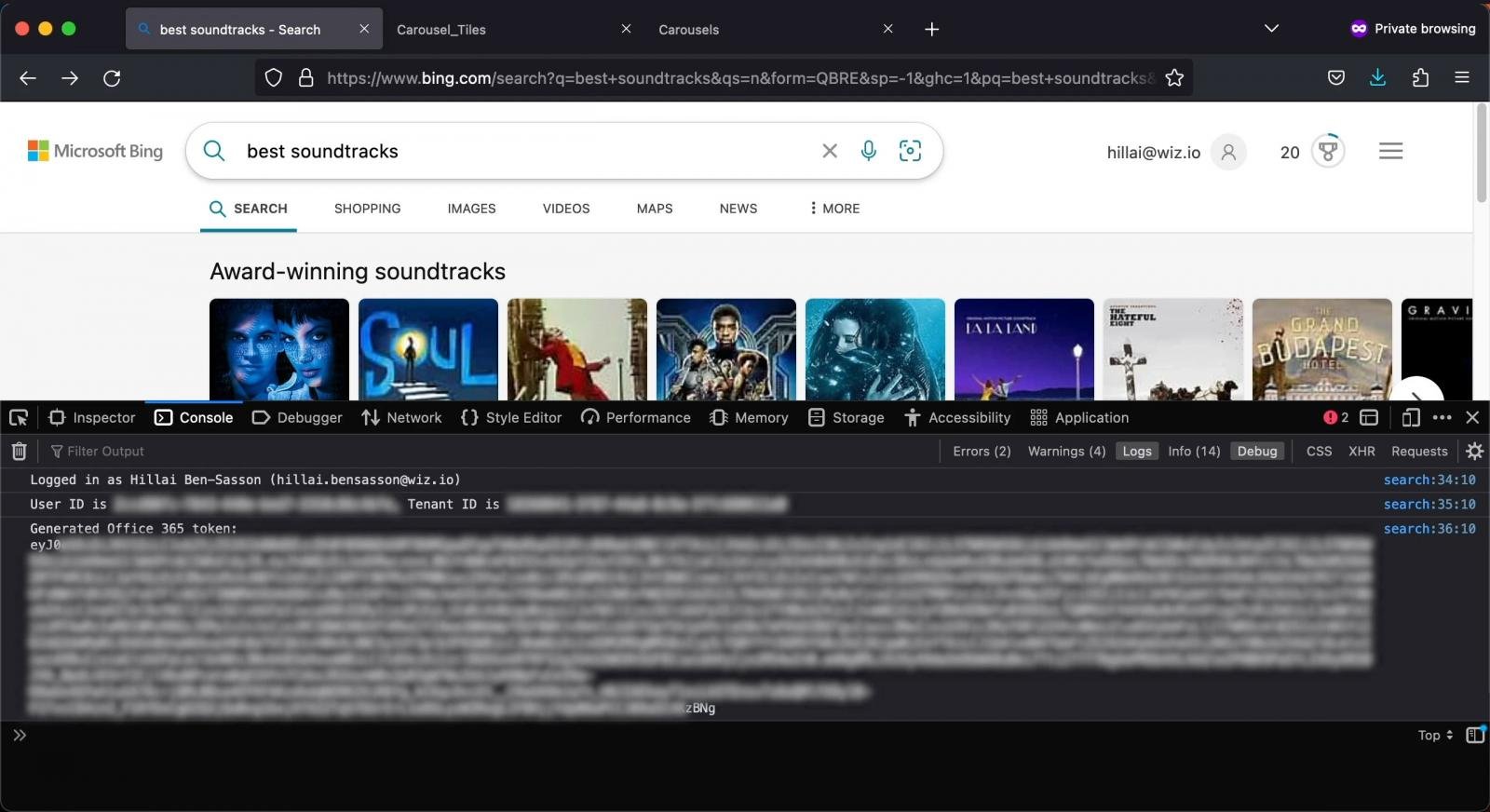
Wiz analysts found a misconfigured “Bing Trivia” app that allowed anyone to log into the app and access its CMS (Content Management System).
However, they soon discovered that the app tied directly to Bing.com, allowing them to edit live content displayed in Bing search results.
To verify that they had full control, the researchers attempted and succeeded in modifying the search results for the search term “best soundtracks”, adding arbitrary results to the top carousel.
Next, analysts checked if they could inject a payload into Bing search results using that same CMS and found they could execute a cross-site scripting (XSS) attack on Bing.com.
After confirming that XSS was possible, Wiz reported his findings to Microsoft and worked with the software company to determine the exact impact of this second attack.
An XSS test showed it was possible to compromise the Office 365 token of any Bing user who saw the carousel in search results, giving them full access to searcher accounts.
This includes access to Outlook emails, calendar data, messages on Teams, SharePoint documents and OneDrive files.
Microsoft’s fix
Microsoft played down the issue, saying the misconfiguration that allowed external parties read and write access only affected a small number of internal applications and was fixed immediately.
Additionally, Microsoft claims to have introduced security enhancements that will prevent Azure AD misconfiguration issues from becoming a problem again.
Most notably, Microsoft has stopped issuing access tokens to unregistered clients in resource tenants, limiting access to only properly registered clients.
“This feature has been disabled for over 99% of client applications,” it reads. Microsoft Notice.
“For the rest of the multi-tenant applications that rely on client access without a service principal, we have provided instructions in a Azure Service Health Security Advisory to global administrators (Azure portal and email) and in Microsoft 365 Message center.”
Additionally, additional security checks have been added for multi-tenant applications, checking for tenant IDs matching against a defined allowlist and for the presence of a customer (service principal) record.
It is recommended that developers and administrators controlling multi-tenant applications review Updated guidance from Microsoft securing them properly.
For more details, Wiz published a separate article, more detailed report which also includes remedial advice.
Wiz Research received a $40,000 bug bounty for responsibly disclosing its findings to Microsoft.
[ad_2]
Source link
