[ad_1]

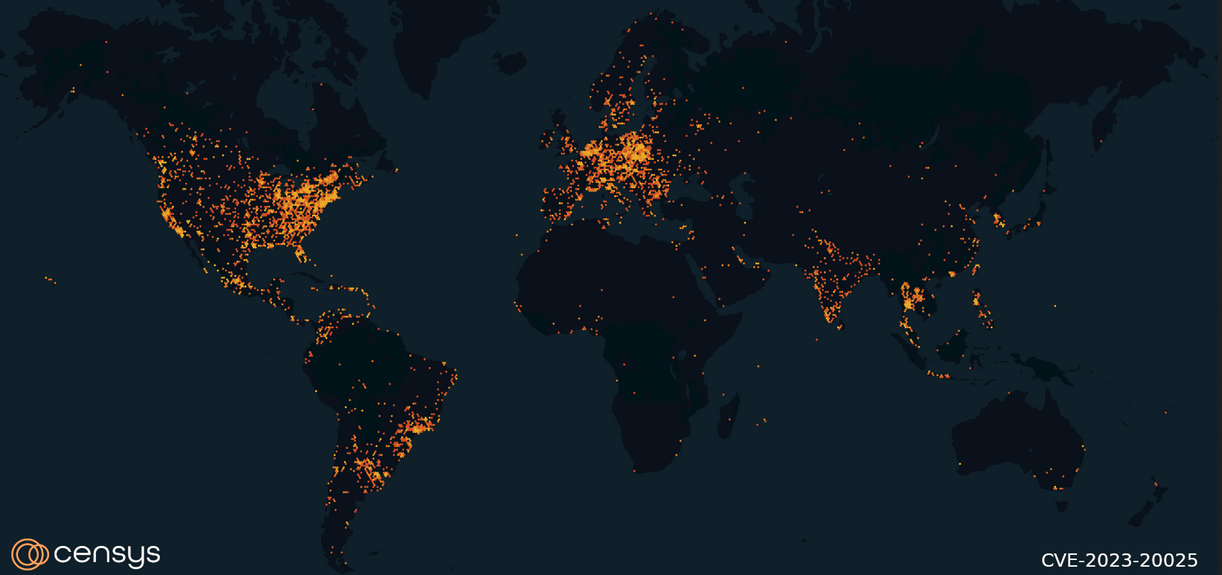
More than 19,000 end-of-life Cisco VPN routers on the Internet are exposed to attacks targeting a remote command execution exploit chain.
By linking two security vulnerabilities revealed last weekattackers can bypass authentication (CVE-2023-20025) and execute arbitrary commands (CVE-2023-2002) on the underlying Cisco Small Business operating system RV016, RV042, RV042Gand RV082 routers.
Unauthenticated attackers can remotely exploit the critical-severity authentication bypass flaw via specially crafted HTTP requests sent to the vulnerable routers’ web management interface to gain root access.
Cisco has classified CVE-2023-20025 as critical and has stated that its Product Security Incident Response Team (PSIRT) is aware of proof-of-concept exploit code available in the wild.
Despite this, the company also stated that it “has not released and will not release software updates that address this vulnerability.”
At this time, Cisco has not found any evidence to suggest that this exploit chain is being misused in attacks.
Thousands of routers vulnerable to attacks
After a Computer Beep reported that these routers would be left unpatched and by examining how many of them are accessible on the Internet, Censys discovered nearly 20,000 Cisco RV016, RV042, RV042G and RV082 routers online.
“Looking only at HTTP services that include pattern numbers in the “WWW-Authenticate” response header or an HTTPS service with a matching TLS organizational unit, Censys search results show that approximately 20,000 hosts have indicators that they are potentially vulnerable to this attack” Censys said.
“Of the four vulnerable models, RV042 dominates the landscape, with over 12,000 hosts exposed to the Internet.
“The RV082 and RV042 with 3.5,000 hosts, while the RV016 lags behind with just 784 assets exposed to the internet.”
Although they do not receive security updates and Cisco has stated that “there is no workaround to address these vulnerabilities”, users can still protect their devices from attacks by disabling the web-based management interface and blocking access to ports 443 and 60443 to thwart exploit attempts.
To do this, log into the web management interface of each vulnerable router, go to Firewall > General and uncheck the Remote Management box. Cisco also provides step-by-step instructions on blocking access to ports 443 and 60443.
Affected routers will still be accessible and configurable through the LAN interface after the above mitigation is implemented.
Cisco also said so would not resolve a critical authentication bypass flaw affecting multiple EoL routers in September and advised users to upgrade to RV132W, RV160, or RV160W routers still under support.
Three months earlier, in June, Cisco again encouraged owners to migrate to new router models after leaking a critical remote code execution (RCE) vulnerability in another series of end-of-life VPN routers that also haven’t been patched.
[ad_2]
Source link
