[ad_1]

Taiwanese PC spare parts manufacturer MSI (Micro-Star International) has been listed on the extortion portal of a new ransomware gang known as “Money Message”, which claims to have stolen source code from the network of the company.
MSI is a global hardware giant that manufactures motherboards, graphics cards, desktops, laptops, servers, industrial systems, PC peripherals and infotainment products, with annual revenue over $6.5 billion.
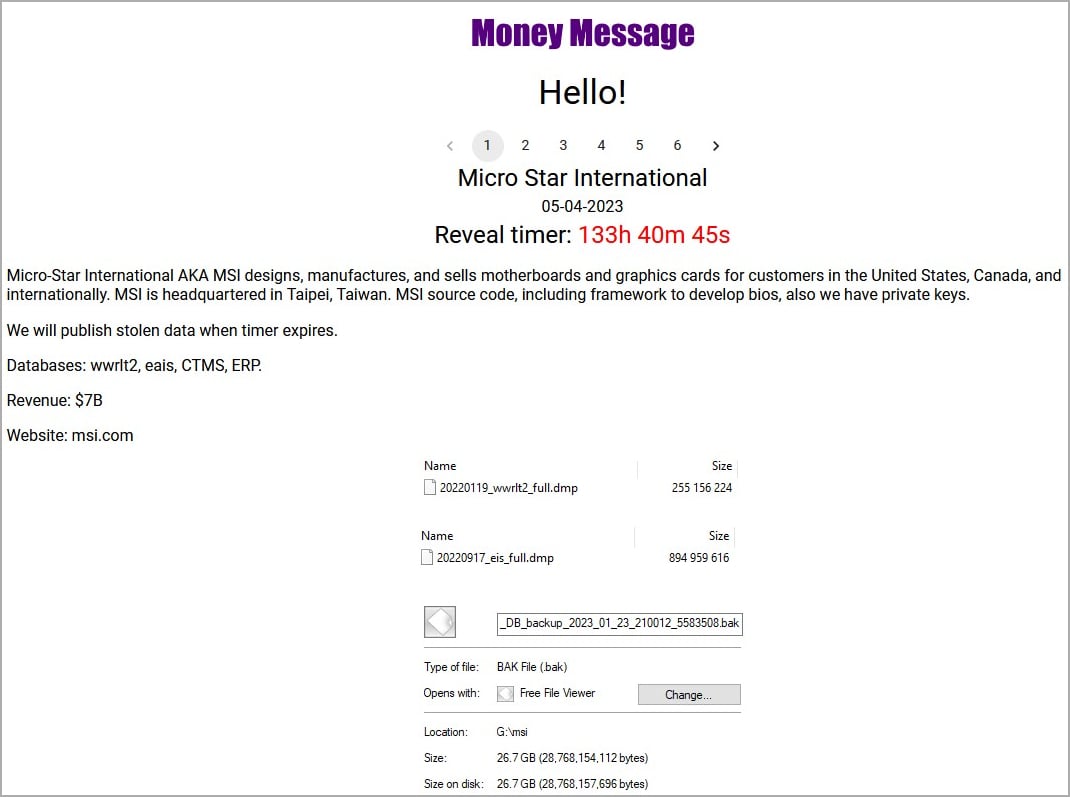
The threat actor listed MSI on its data leak website and posted screenshots of what it claims are the hardware vendor’s CTMS and ERP databases and files containing the software’s source code , private keys and BIOS firmware.
Money Message is now threatening to release all these allegedly stolen documents in about five days unless MSI meets its ransom demands.
BleepingComputer highlighted this new ransomware groupin a report released over the weekend describing the gang’s attack chain, hinting at the possibility that the threat actors breached a well-known hardware vendor.
According to threads seen by BleepingComputer at the time, the threat actors claimed to have stolen 1.5TB of data from MSI’s systems, including source code and databases, and demanded a ransom of 4,000 $000.
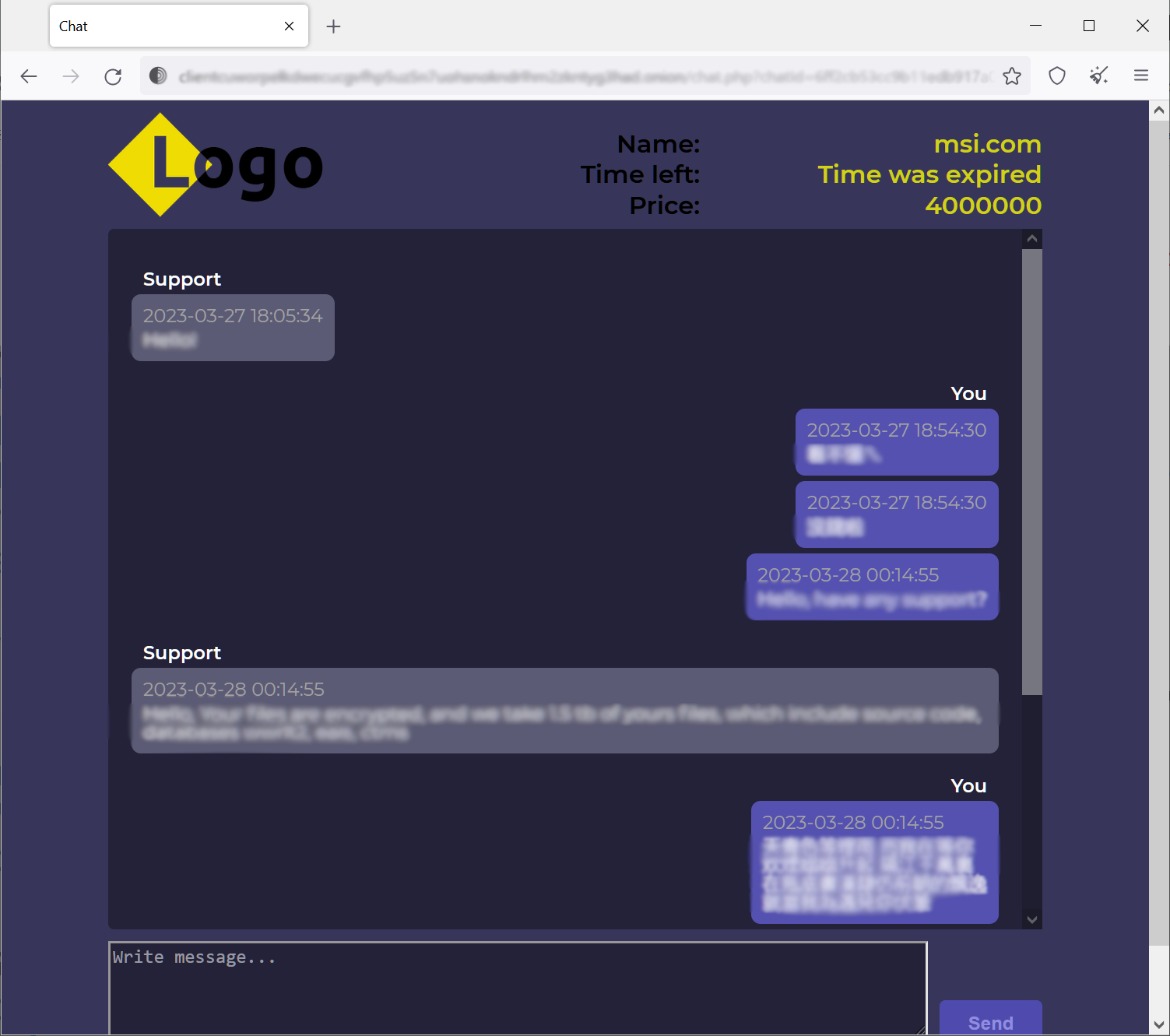
“Tell your manager that we have MSI source code including framework to develop bios, we also have private keys that can connect to any custom module of these BIOS and install it on PC with this bios,” a Money Message operator said in a chat with an MSI agent.
Since discovering this, BleepingComputer has contacted MSI several times, but we are still awaiting a response.
As such, we have not been able to verify whether Money Message’s data breach allegations are valid and whether the data they are threatening to leak belongs to MSI.
[ad_2]
Source link
