[ad_1]
A variant of the Mirai botnet targets nearly two dozen vulnerabilities aimed at taking control of D-Link, Arris, Zyxel, TP-Link, Tenda, Netgear and MediaTek devices to use them for Distributed Denial of Service (DDoS) attacks .
The malware was identified by Palo Alto Networks Unit 42 researchers during two ongoing campaigns that began March 14 and peaked in April and June.
In a report released today, researchers warn that botnet developers continue to add code for exploitable vulnerabilities.
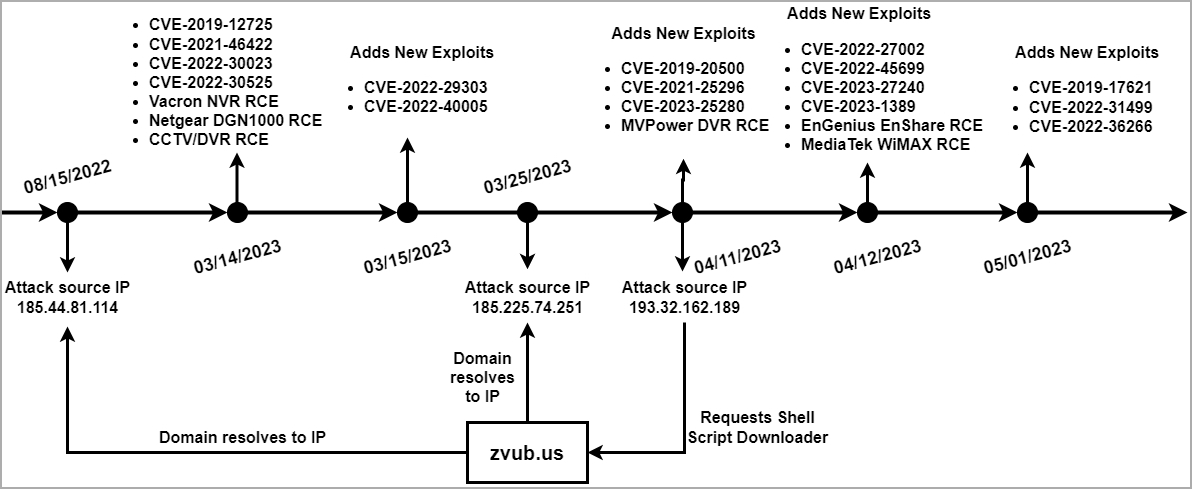
In total, the malware targets no less than 22 known security issues in various connected products, including routers, DVRs, NVRs, WiFi communication dongles, thermal monitoring systems, access control systems and solar power generation monitors.
Below is the full list of vulnerabilities and products targeted by the malware in the latest version identified by Unit 42 researchers:
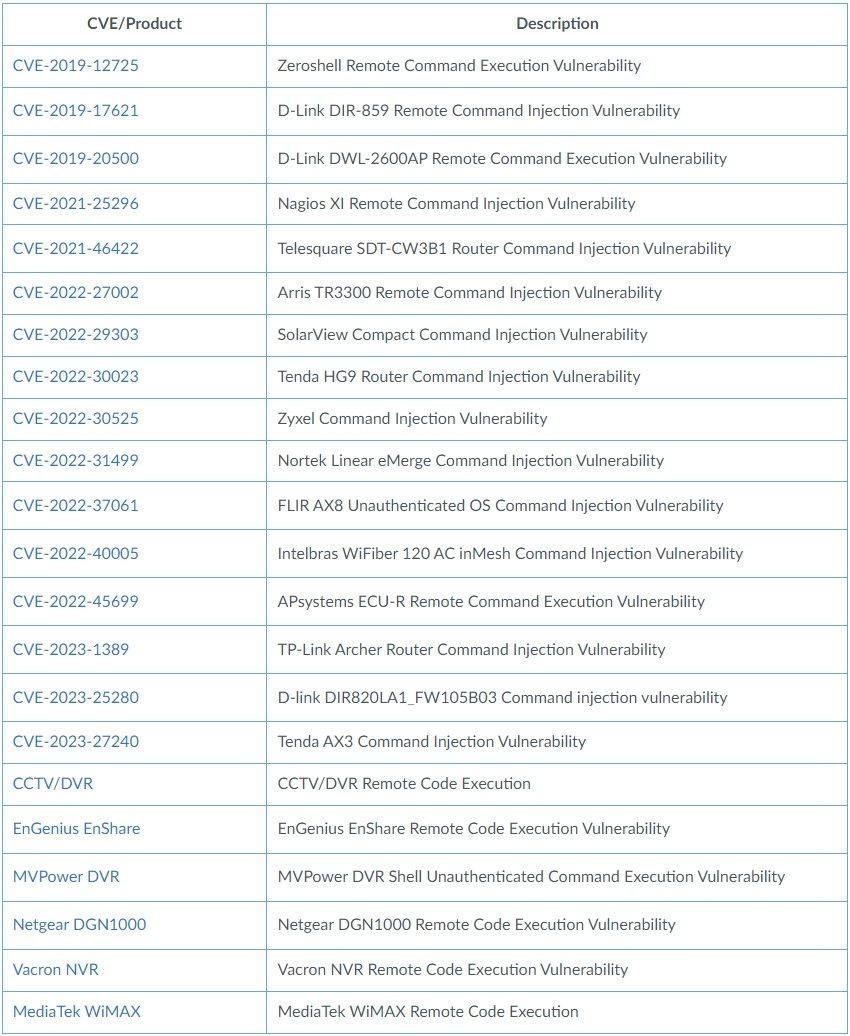
One of these flaws, CVE-2023-1389, affects the TP-Link Archer A21 (AX1800) WiFi router and has been reported by ZDI to be exploited by the Mirai malware. since the end of April. However, it is unclear whether the two refer to the same activity.
Attack Details
The attack begins by exploiting one of the mentioned flaws, setting the stage for the execution of a shell script from an external resource.
This script will download the botnet client that matches the architecture of the compromised device, covering armv4l, arm5l, arm6l, arm7l, mips, mipsel, sh4, x86_64, i686, i586, arc, m68k, and sparc.
After running the bot client, the shell script downloader deletes the client file to sweep away traces of infection and reduce the probability of detection.
Compared to the standard Mirai variants in circulation, this one directly accesses the encrypted strings in the .rodata section via an index instead of setting up a string table to get the configuration of the botnet client.
This approach bypasses the initialization of the cipher string table, giving the malware speed and stealth and making it less likely to be detected by security tools.
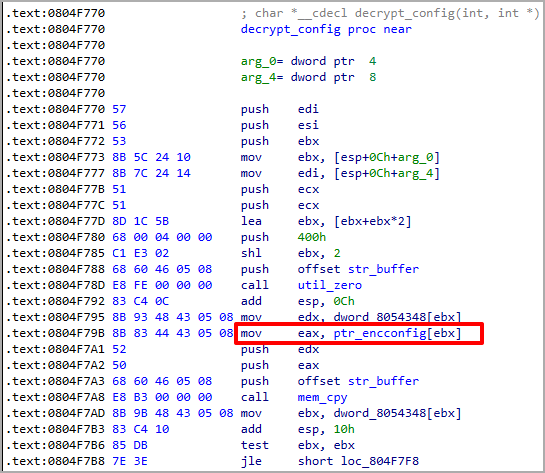
Unit 42 also notes that this Mirai variant lacks the ability to brute force telnet/SSH login credentials, so its distribution relies entirely on operators manually exploiting the vulnerabilities.
It is possible to reduce the risk of infection by applying the latest firmware update available from the device vendor or manufacturer, changing from the default access credentials to something strong and unique , and removing the accessibility of the remote administration panel if it is not needed.
Signs of botnet malware infection on an IoT device may include excessive overheating, change of settings/configuration, frequent disconnections, and overall drop in performance.
[ad_2]
Source link
