[ad_1]

Attackers hack poorly secured Microsoft SQL (MS-SQL) servers exposed to Interned to deploy Trigona ransomware payloads and encrypt all files.
MS-SQL servers are hacked via brute force or dictionary attacks that take advantage of easily guessed account credentials.
After connecting to a server, the threat actors deploy malware dubbed CLR Shell by security researchers from South Korean cybersecurity firm AhnLab who spotted the attacks.
This malware is used to collect system information, modify compromised account configuration and elevate privileges to LocalSystem by exploiting a vulnerability in the secondary Windows login service (which will be needed to run the ransomware as a service).
“CLR Shell is a type of CLR assembly malware that receives commands from malicious actors and performs malicious behaviors, similar to WebShells of web servers”, AhnLab says.
In the next step, attackers install and launch a malware dropper as a svcservice.exe service, which they use to launch the Trigona ransomware as svchost.exe.
They also configure the ransomware binary to automatically launch on every system reboot via a Windows AutoRun key to ensure systems will be encrypted even after a reboot.
Before encrypting the system and deploying ransom notes, the malware disables system recovery and deletes all shadow copies of Windows volumes, making recovery impossible without the decryption key.
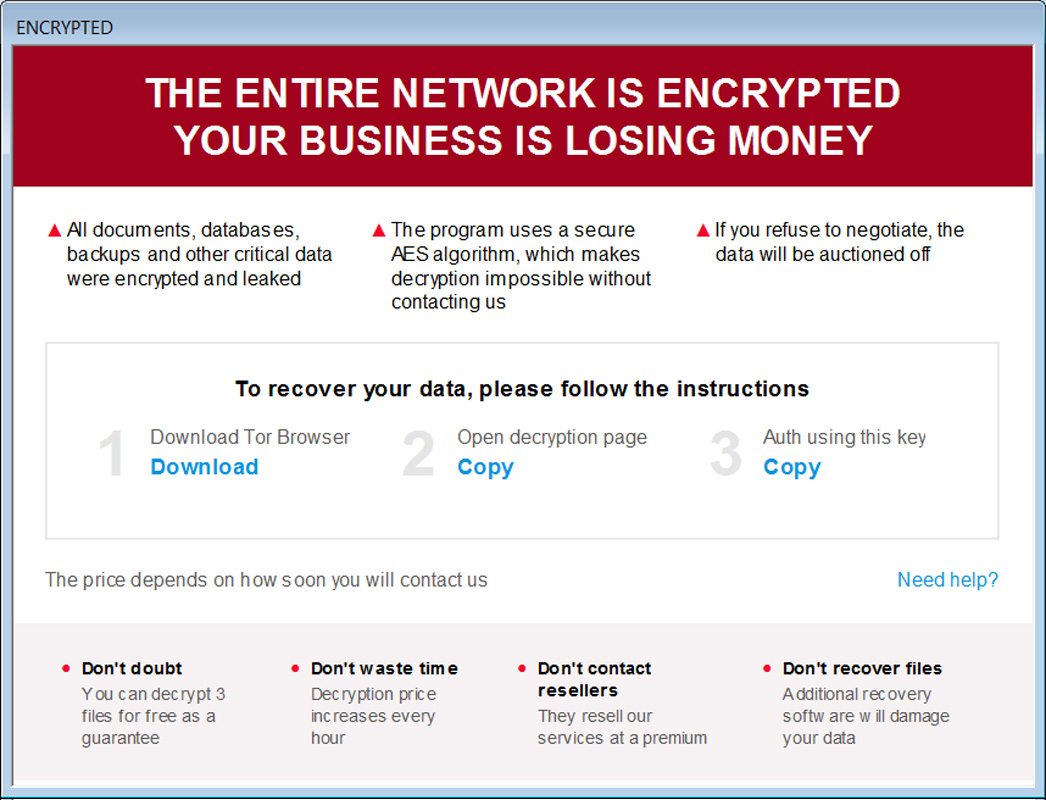
First spotted in October 2022 by MalwareHunterTeam And analyzed by BleepingComputerthe Trigona ransomware operation is known to only accept ransom payments in Monero cryptocurrency from victims around the world.
Trigona encrypts all files on victim devices, except those located in specific folders, including the Windows and Program Files directories. Prior to encryption, the gang also claims to steal sensitive documents which will be added to their dark web leak site.
Moreover, the ransomware renames encrypted files by appending ._locked extension and embeds encrypted decryption key, campaign ID and victim ID (company name) in each locked file.
It also creates ransom notes named “how_to_decrypt.hta” in each folder with attack information, link to Trigona Tor trading website and link containing authorization key needed to login to the trading site. negotiation.
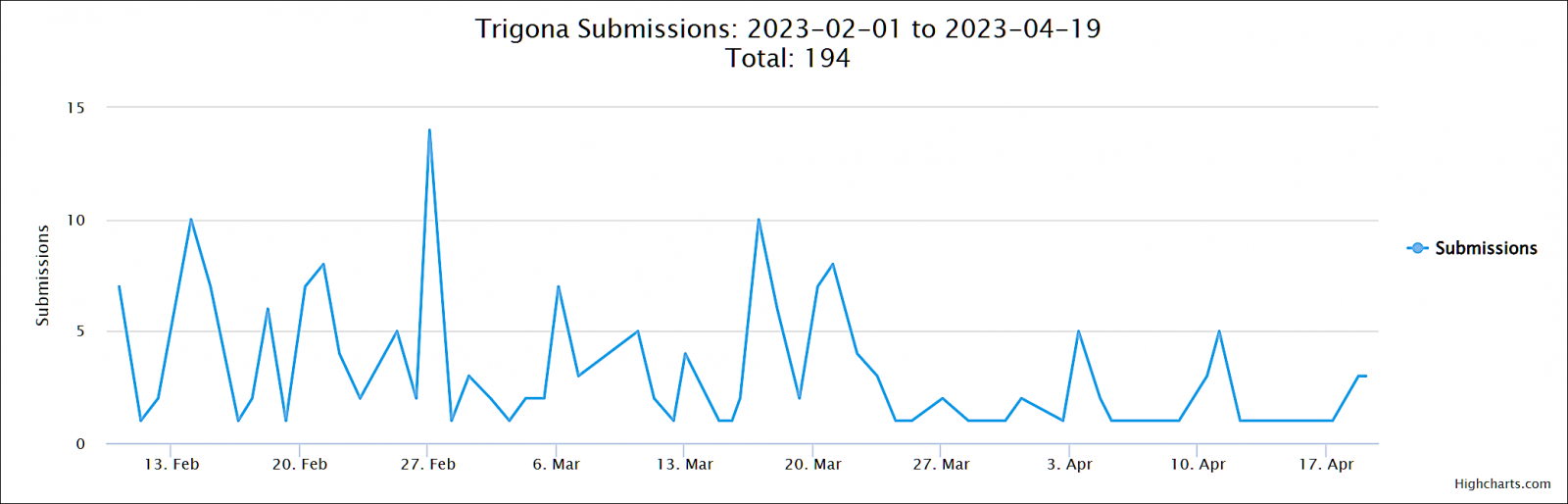
The Trigona ransomware gang has been behind a steady stream of attacks, with at least 190 submissions to the ID Ransomware platform so far this year.
[ad_2]
Source link
