[ad_1]

Microsoft has released security updates to address a Zero Day Secure Boot vulnerability exploited by BlackLotus UEFI malware to infect fully patched Windows systems.
Secure Boot is a security feature that blocks non-OEM approved boot loaders on computers with Unified Extensible Firmware Interface (UEFI) firmware and a Trusted Platform Module (TPM) chip to prevent loading rootkits during the boot process.
According to a Microsoft Security Response Center blog postthe security breach (tracked as CVE-2023-24932) was used to circumvent patches released for CVE-2022-21894another abused secure boot bug in Attacks of BlackLotus Last year.
“To protect against this attack, a fix for Windows Boot Manager (CVE-2023-24932) is included in the May 9, 2023 security update, but is disabled by default and will not provide protections,” said said the company.
“This vulnerability allows an attacker to execute self-signed code at the Unified Extensible Firmware Interface (UEFI) while Secure Boot is enabled.
“This is used by threat actors primarily as a defense persistence and evasion mechanism. Successful exploitation relies on the attacker having physical access or local administrator privileges to the targeted device. “
All Windows systems with Secure Boot protections enabled are affected by this flaw, including on-premises, virtual machines, and cloud-based devices.
However, the CVE-2023-24932 security patches released today are only available for supported versions of Windows 10, Windows 11, and Windows Server.
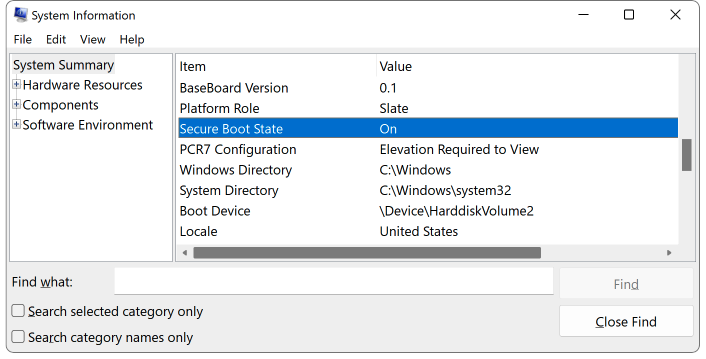
To determine if Secure Boot protections are enabled on your system, you can run the msinfo32 from a Windows command prompt to open the System Information application.
Secure Boot is enabled if you see a “Secure Boot State ON” message on the left side of the window after selecting “System Summary”.
Manual steps required to mitigate CVE-2023-24932
Although the security updates released today by Redmond contain a Windows Boot Manager fix, they are disabled by default and will not remove the attack vector exploited in BlackLotus attacks.
To defend their Windows devices, customers must follow a procedure requiring several manual steps “to update the bootable media and apply revocations before activating this update”.
To manually enable protections for Secure Boot bypass bug CVE-2023-24932, you must perform the following steps in this exact order (otherwise the system will no longer boot):
- INSTALL May 9, 2023, updates to all affected systems.
- UPDATE your bootable media with Windows Updates released on or after May 9, 2023. If you don’t create your own media, you’ll need to get official, updated media from Microsoft or your device manufacturer (OEM).
- APPLY revocations to protect against the vulnerability in CVE-2023-24932.
Microsoft is also taking a phased approach to applying protections addressing this security vulnerability to reduce the impact to customers due to the activation of CVE-2023-24932 protections.
The deployment schedule includes three phases:
- May 9, 2023: The initial patch for CVE-2023-24932 is released. In this release, this patch requires the Windows Security Update May 9, 2023 and additional customer action to fully implement the protections.
- July 11, 2023: A second release will provide additional update options to simplify the deployment of protections.
- Q1 2024: This final release will enable the fix for CVE-2023-24932 by default and enforce boot manager revocations on all Windows devices.
Microsoft also warned customers that there is no way to roll back the changes once the CVE-2023-24932 mitigations are fully deployed.
“Once mitigation for this issue is enabled on a device, which means revocations have been applied, it cannot be undone if you continue to use Secure Boot on that device,” Microsoft said.
“Even reformatting the disk will not remove revocations if they have already been applied.”
Update: Revised title to explain this is an optional fix.
[ad_2]
Source link
