[ad_1]

Microsoft disabled several fraudulent and verified Microsoft Partner Network accounts for creating malicious OAuth apps that hacked into organizations’ cloud environments to steal email.
In a joint announcement between Microsoft and Proofpoint, Microsoft says threat actors are posing as legitimate businesses to successfully register and be verified as that business in the Microsoft Cloud Partner Program (MCPP).
Threat actors have used these accounts to register verified OAuth applications in Azure AD for consent phishing attacks targeting business users in the UK and Ireland.
Microsoft says malicious OAuth apps were used to steal customer emails. However, Proofpoint warned that the app’s permissions could have allowed them to access calendars and meeting information and change user permissions.
Typically, this information is used for cyber espionage, business email compromise (BEC) attacks, or to gain additional access to internal networks.
Proofpoint disclosed the malicious campaign on December 15, 2022, with Microsoft soon shutting down all fraudulent accounts and OAuth apps.
“Microsoft has disabled applications and accounts belonging to the threat actor to protect customers and has engaged our Digital Crimes Unit to identify further actions that may be taken with this particular threat actor,” read the ad.
“We have implemented several additional security measures to improve MCPP’s verification process and reduce the risk of similar fraudulent behavior in the future.”
Microsoft has contacted all affected organizations and warned them that they should conduct a thorough internal investigation to verify that the suspicious apps have been disabled from their environment.
BleepingComputer contacted Microsoft to learn more about the attacks and how they improve the MCPP verification process, but no response was immediately available.
Impersonate legitimate businesses
OAuth apps allow third-party apps to gain permission to access a user’s cloud account data to perform a specific action, such as generating calendar events or scanning emails at the time. search for malware.
Instead of logging into an OAuth application with a user’s credentials, they are registered with Azure AD and can be granted requested permissions on a user’s account. These permissions can be easily revoked without changing a user’s credentials if necessary.
In recent years, malicious threat actors have used OAuth applications in “consent phishing” attacks to gain access to Office 365 and Microsoft 365 cloud data of targeted organizations.
To further protect customers, Microsoft allows developers to become verified publishers, which means Microsoft has verified their identity.
OAuth applications created by a verified partner have a blue check mark in the Azure Active Directory (Azure AD) consent prompt, indicating that this application is more trusted.
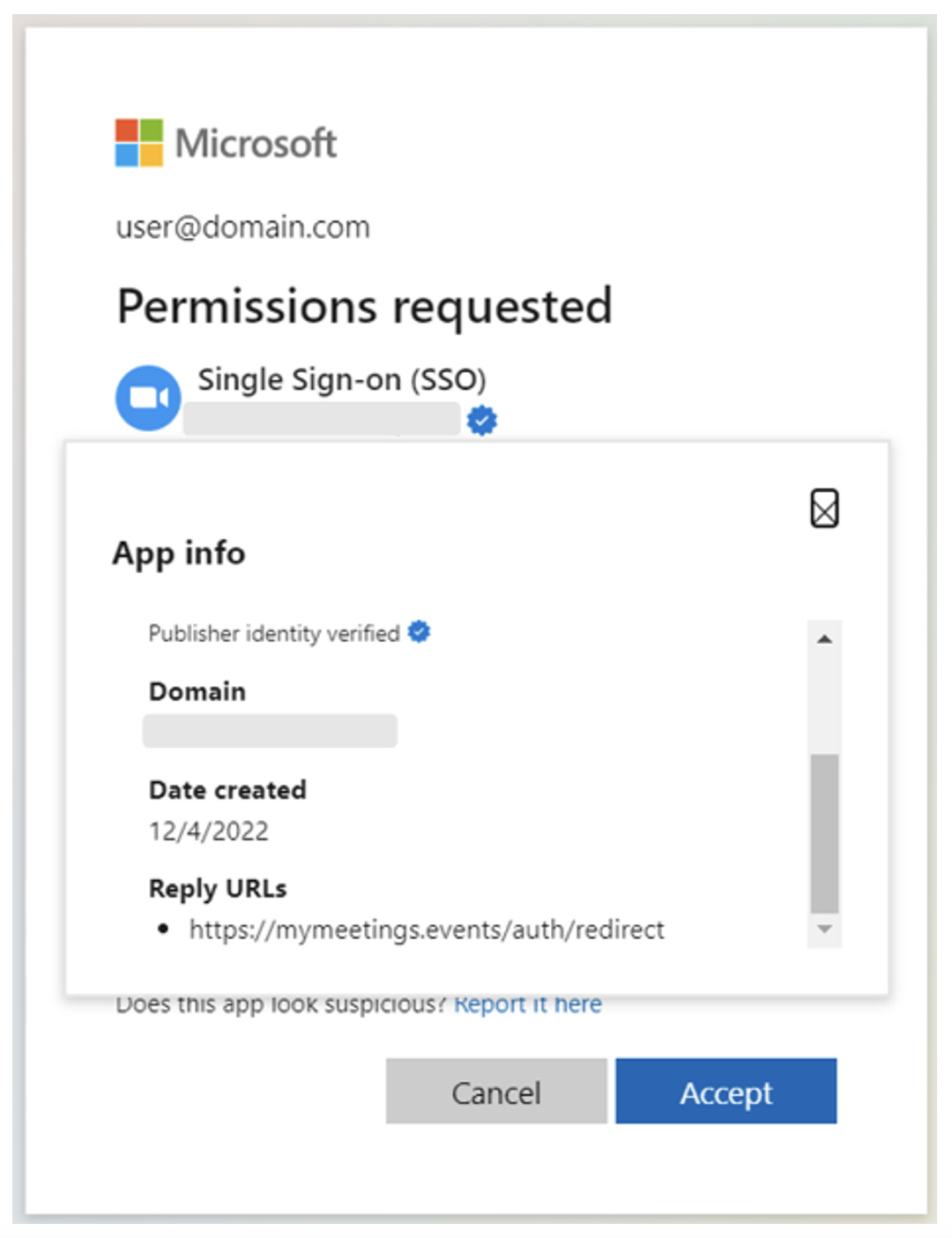
According to a Proofpoint report published today, the researchers explained that the threat actors had stopped trying to compromise existing Microsoft-verified publisher accounts and instead posed as credible publishers to verify themselves.
Threat actors impersonated other companies using a display name similar to an existing verified publisher, but obscured the “verified publisher” name, which was different because a change that would require re-verification with Microsoft.
They also linked the legitimate company’s “Terms of Service” and “Policy Statement” web pages to boost the legitimacy of their apps and identity.
Proofpoint has identified three malicious OAuth applications from three verified vendors, all targeting the same organizations and communicating with the same hacker-controlled infrastructure.
“Based on our analysis, this campaign appeared to be primarily targeting UK-based organizations and users. Affected users included finance and marketing staff, as well as high-level users such as managers and executives,” says Proofpoint. .
Two of the apps were called “Single Sign On (SSO)” and the third was called “Meeting”, requesting access to the following permissions:
- Read your mail
- Retain access to the data to which you have granted access
- Read your mailbox settings
- Log in and read your profile
- Send mail like you
- Read your diaries
- Read your online meetings
Unfortunately, Proofpoint has seen evidence of multiple users being impacted by the attacks, leading to the compromise of their organizations.
The campaign ran from December 6, 2022 to December 27, 2022, when Microsoft disabled all malicious apps. The investigation into the attack is continuing.
In January 2022, we covered a similar campaign discovered by Proofpoint, where threat actors abused previously compromised verified publisher accounts to create trusted OAuth applications with which they targeted company executives.
Microsoft released a detailed guide about how users can protect themselves against these attacks and best practices for preventing them in the first place.
[ad_2]
Source link
