[ad_1]

Microsoft, Fortra and the Health Information Sharing and Analysis Center (Health-ISAC) have announced a broad legal crackdown on servers hosting pirated copies of Cobalt Strike, one of the main hacking tools used by cybercriminals.
“We will need to be persistent as we work to remove old, cracked copies of Cobalt Strike hosted around the world,” said Amy Hogan-Burney, head of Microsoft’s Digital Crimes Unit (DCU).
“This is an important action by Fortra to protect the lawful use of its security tools. Microsoft is also committed to the lawful use of its products and services.”
Last Friday, March 31, the US District Court for the Eastern District of New York issued a court order allowing the coalition to seize domain names and remove IP addresses from servers hosting pirated versions of Cobalt Strike.
This will happen with the help of Computer Emergency Preparedness Teams (CERTs) and relevant Internet Service Providers (ISPs), with the ultimate goal of taking the malicious infrastructure offline.
Takedowns related to this action already began earlier this week, Tuesday, and the court order also allows Microsoft and Fortra to disrupt new infrastructure that threat actors will use in future attacks.
“Disrupting old pirated copies of Cobalt Strike will significantly impede the monetization of these illegal copies and slow their use in cyberattacks, forcing criminals to re-evaluate and change their tactics,” Hogan Burney said.
“Today’s action also includes copyright claims against the malicious use of software code from Microsoft and Fortra that is modified and abused to harm.”
Used by ransomware gangs and state hackers
Fortra, formerly known as Help Systems, has released Cobalt Strike over a decade ago, in 2012, as a legitimate commercial penetration testing tool for red teams to scan organizational infrastructure for vulnerabilities.
Although the developer carefully selects customers and only grants licenses for legal use, malicious actors have obtained and distributed pirated copies of the software over time, making Cobalt Strike one of the most widely used tools in cyberattacks involving data theft and ransomware.
Threat actors use it for post-exploitation tasks after deploying beacons designed to provide them with persistent remote access to compromised devices to harvest sensitive data or drop additional malicious payloads.
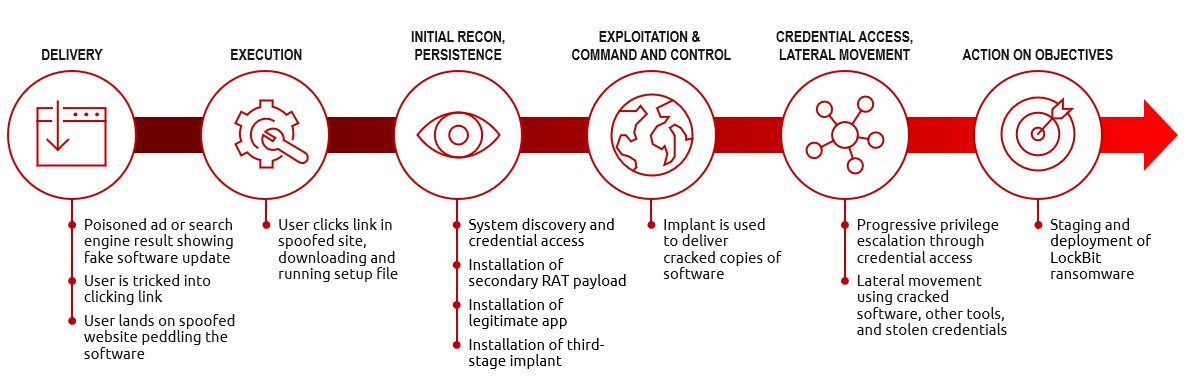
Microsoft has detected malicious infrastructure hosting Cobalt Strike around the world, including in China, the United States, and Russia, although the identities of those behind the criminal operations remain unknown.
The company has also observed several state-backed threat actors and hacking groups using cracked versions of Cobalt Strike while acting on behalf of foreign governments, including Russia, China, Vietnam and Iran.
“Ransomware families associated with or deployed by pirated copies of Cobalt Strike have been linked to more than 68 ransomware attacks affecting healthcare organizations in more than 19 countries around the world,” Hogan-Burney said.
“These attacks cost hospital systems millions of dollars in recovery and repair costs, as well as disruptions to critical patient care services, including delays in diagnosis, imaging and lab results, medical procedures cancellations and delays in the delivery of chemotherapy treatments, to name a few.”
In November 2022, the Google Cloud Threat Intelligence team also opened 165 YARA rules and a set of Indicators of Compromise (IOC) for help network defenders detect Cobalt Strike components in their networks.
[ad_2]
Source link