[ad_1]

Royal Ransomware is the latest ransomware operation to add Linux device encryption support to its most recent malware variants, specifically targeting VMware ESXi virtual machines.
BleepingComputer reported similar Linux ransomware encryptors released by several other gangs, including basta black, LockBit, BlackMatter, AvosLocker, REvil, Hello Kitty, RansomEXXAnd Hive.
New Royal Ransomware Linux Variant Has Been Discovered By Will Thomas from the Equinix Threat Analysis Center (ETAC) and is run using the command line.
It also supports several flags that will give ransomware operators some control over the encryption process:
- -stopvm > stop all running VMs so they can be encrypted
- -vmony – Encrypt only virtual machines
- -fork – unknown
- -logs – unknown
- -id: the identifier must be 32 characters long
While encrypting files, the ransomware will append .royal_u extension to all encrypted files on the virtual machine.
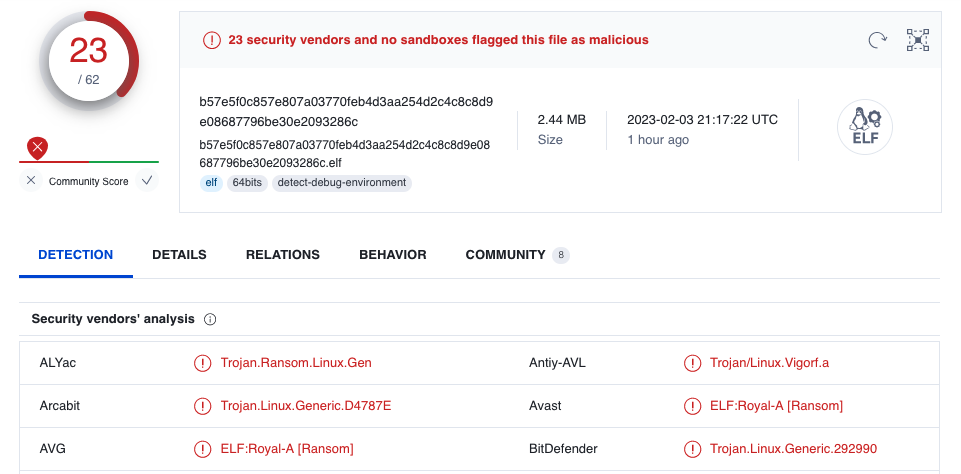
While anti-malware solutions had problems detecting the Royal Ransomware samples that bundle the new targeting capabilities, they are now detected by 23 of the 62 malware scanning engines on VirusTotal.
Who is Royal Ransomware?
Royal Ransomware is a private operation made up of seasoned threat actors who have previously worked with Operation Conti ransomware
From September, Royal rise in power malicious activity months after it was first spotted in January 2022.
While they initially used encryptors from other operations, such as BlackCat, they moved on to using their own, starting with Zeon which dropped ransom notes similar to those generated by Conti.
In mid-September, the group was rebranded as “Royal” and began deploying a new cipher in attacks that produce ransom notes with the same name.
The gang demands ransoms ranging from $250,000 to tens of millions after encrypting their targets’ corporate network systems.
In December, the US Department of Health and Human Services (HHS) warned Royal ransomware attacks targeting healthcare and public health (HPH) organizations.
Most ransomware strains now also target Linux
The evolution of ransomware groups towards targeting ESXi virtual machines aligns with a trend that enterprises have switched to virtual machines because they offer improved device management and much more efficient resource management.
After deploying their payloads to ESXi hosts, ransomware operators use a single command to encrypt multiple servers.
“The reason most ransomware groups have implemented a Linux version of their ransomware is to specifically target ESXi,” Wosar told BleepingComputer last year.
You can find more information about Royal Ransomware and what to do if you are affected in this support topic on the BleepingComputer forum.
Tens of Thousands of VMware ESXi Servers Exposed to the Internet have reached their end of life in October, according to a report by Lansweeper.
These systems will now only receive technical support but no security updates, leaving them vulnerable to ransomware attacks.
To put things in perspective and show how vulnerable these servers are to attack, a new strain of ransomware known as ESXiArgs has been used to find and encrypt unpatched servers in a massive campaign targeting ESXi devices in the world this Friday.
In just a few hours, more than 100 servers worldwide were compromised by these attacks, according to a Shodan Research.
[ad_2]
Source link
