[ad_1]

KeePass has released version 2.54, fixing the CVE-2023-32784 vulnerability that allows extraction of the plaintext master password from application memory.
When creating a new KeePass password manager database, users must create a master password, which is used to encrypt the database. When opening the database in the future, users must enter this master key to decrypt it and access the credentials stored there.
However, in May 2023, security researcher ‘vdohney’ disclosed a vulnerability and proof-of-concept exploit which allowed you to partially extract the main KeepPass password in plain text from an application core dump.
“The problem is with SecureTextBoxEx. Due to the way it handles input, when the user types the password, there will be leftover strings,” vdohney explained in a KeePass bug report.
“For example, when “Password” is typed, it will result in these remaining strings: •a, ••s, •••s, ••••w, •••••o, ••••• • r, •••••••d.”
This dumper allows users to recover almost all master password characters except the first one or two, even if the KeePass workspace is locked or the program was recently closed.
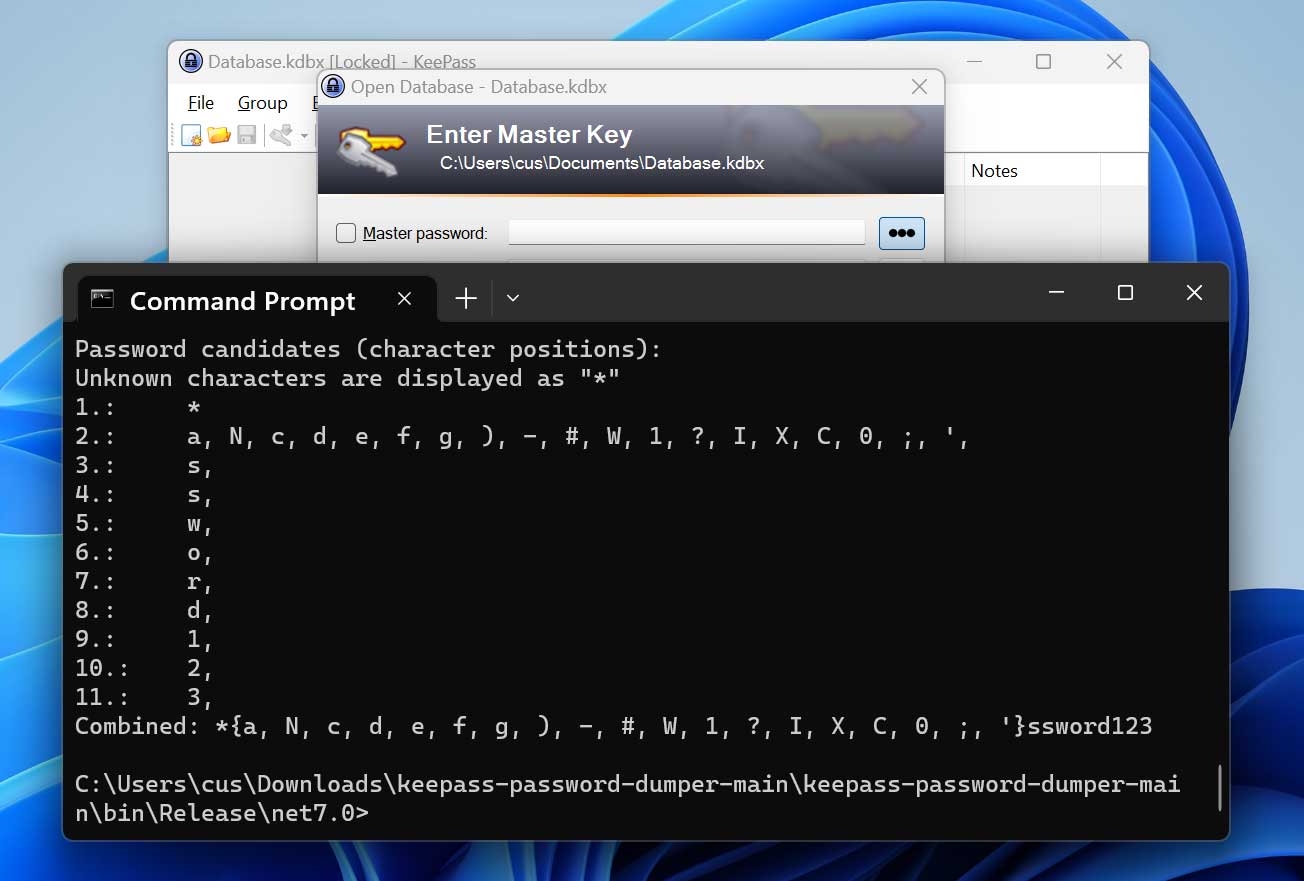
Source: BleepingComputer
Information-stealing malware or threat actors could use this technique to dump the program’s memory and send it and the KeePass database back to a remote server for offline plaintext password recovery. from memory dump. Once the password is retrieved, they can open the KeePass password database and access all saved account credentials.
KeePass creator and lead developer Dominik Reichl acknowledged the flaw and promised to release a patch soon, having already implemented an effective solution tested in beta versions.
KeePass 2.5.4 fixes a vulnerability
Over the weekend, Reichl posted Kee Pass 2.54 sooner than expected, and all users of the 2.x branch are strongly recommended to upgrade to the new version.
KeePass 1.x, Strongbox or KeePassXC users are not impacted by CVE-2023-32784 and therefore do not need to migrate to a newer version.
To address the vulnerability, KeePass now uses a Windows API to set or retrieve data from text boxes, preventing the creation of managed strings that can potentially be removed from memory.
Reichl also introduced “dummy strings” with random characters into the memory of the KeePass process to make it harder to retrieve fragments of the password from memory and combine them into a valid master password.
KeePass 2.5.4 also introduces other security enhancements, such as moving ‘Triggers,’ ‘Global URL Overrides,’ And ‘Password generator profiles‘ in the imposed configuration filewhich provides additional security attacks that modify the KeePass configuration file.
If triggers, overrides and profiles are not stored in the applied configuration because they were created using a previous version, they will be automatically disabled in version 2.54 and users will need to manually enable them at from the “Tools” settings menu.
Users who cannot upgrade to KeePass 2.54 are recommended to reset their master password, delete crash dumps, hibernate files, and swap files that may contain fragments of their password main, or to perform a fresh installation of the operating system.
Keep in mind that the issue only affects passwords entered into the program’s input forms, so if credentials are copied and pasted into the boxes, no data leak string is created. in memory.
[ad_2]
Source link
