[ad_1]

Popular password manager KeePass is vulnerable to extracting the master password from application memory, allowing attackers who compromise a device to recover the password even if the database is locked.
The problem was discovered by a security researcher known as “vdohney”, who published a proof of concept tool allowing attackers to extract the KeePass master password from memory as a proof of concept (PoC).
Password managers allow users to create unique passwords for each online account and store credentials in an easy-to-search database, or password vault, so that you don’t have to remember each one. However, to properly secure this password vault, users must remember the master password used to unlock it and access stored credentials.
This master password encrypts the KeePass password database, preventing it from being opened or read without first entering the password. However, once this master password is compromised, a malicious actor can access all credentials stored in the database.
Therefore, for a password manager to be properly secure, it is essential that users keep the master password and not share it with anyone else.
A new KeePass vulnerability tracked as CVE-2023-3278 allows to recover the main KeePass password, except for the first one or two characters, in plain text, whether the KeePass workspace is locked or possibly even if the program is closed.
“KeePass Master Password Dumper is a simple proof-of-concept tool used to dump the master password from KeePass memory. Apart from the first character of the password, it is mostly capable of recovering the plaintext password” , warns the security researcher on GitHub. exploit tool page.
“No code execution on the target system is required, just a memory dump. It doesn’t matter where the memory comes from – maybe the process dump, swap file (pagefile.sys), hibernation file (hiberfil.sys), or RAM dump of the whole system. It doesn’t matter if the workspace is locked or not.”
The flaw exists because the software uses a custom password entry box named “SecureTextBoxEx”, which leaves traces of every character typed by the user in memory.
“KeePass 2.X uses a custom-developed text box for entering the password, SecureTextBoxEx. This text box is not only used for entering the master password, but also in other places in KeePass, such as password edit boxes (so that the attack can also be used to retrieve their contents),” vdohney explains.
The vulnerability affects the latest version of KeePass, 2.53.1, and since the program is open-source, all project forks are likely affected.
KeePass 1.X, KeePassXC and Strongbox do not appear to be affected by CVE-2023-32784, according to the password dump tool developer.
Additionally, while the PoC has been tested on Windows, the exploit should also work for Linux and macOS, with some modifications, as the issue is not specific to the operating system but to how KeePass handles entries. of the user.

Source: vdohney
Easy to operate
Since core dumps must be retrieved for the KeePass master password to be recovered, exploiting CVE-2023-32784 requires physical access or malware infection on the target machine.
However, information-stealing malware could quickly check whether KeePass exists on a computer or is running, and if so, dump the program’s memory and resend it and the KeePass database to the attacker for an offline recovery of the plaintext password from the memory dump.
BleepingComputer tested vdohney’s “keepass-password-dumper” tool by installing KeePass on a test device and creating a new database with the master password “password123” as shown below.
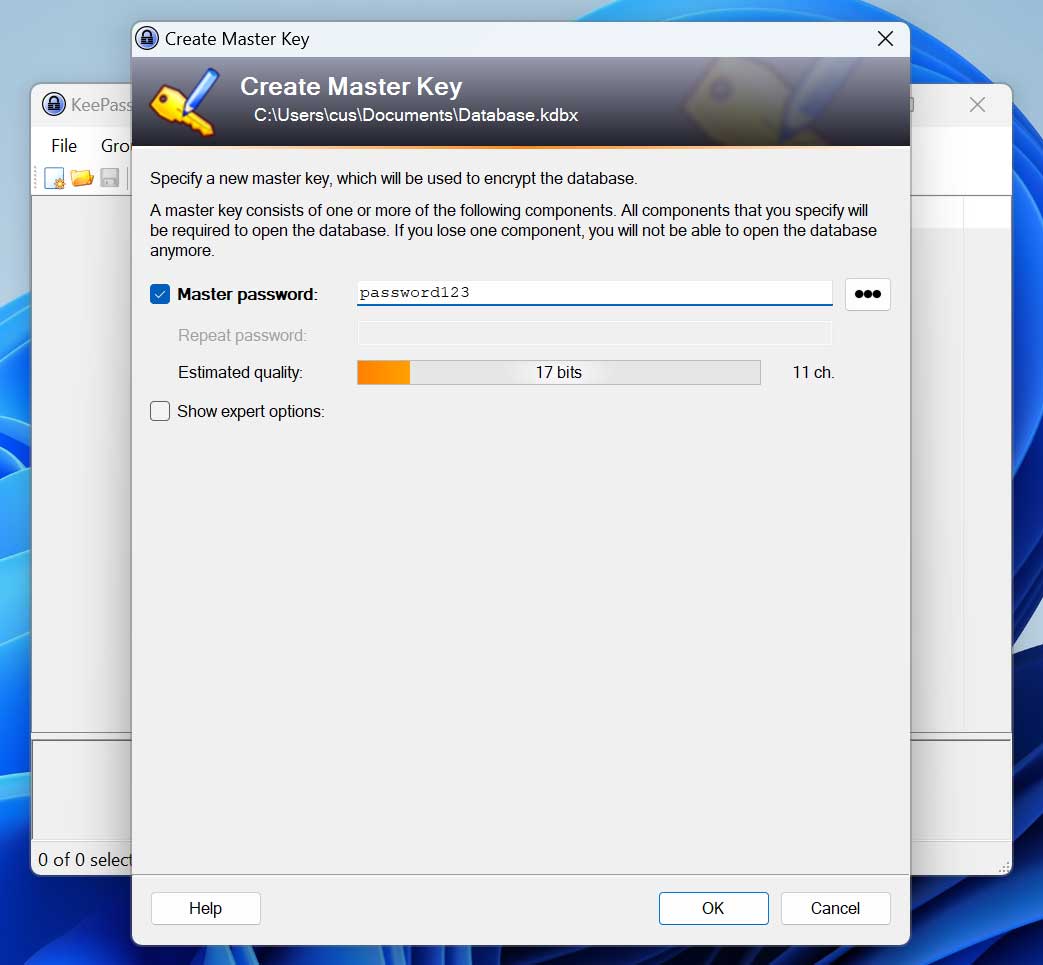
Source: BleepingComputer
We then locked our KeePass workspace, which prevents access unless you re-enter the master password.
In our tests, you can use Process Explorer to dump the KeePass project memory, but this requires a full memory dump, not a minidump, to work properly. No elevated privileges are required to dump process memory.
After compiling vdohney’s tool using Visual Studio, we ran it against our core dump, and it quickly recovered most of our password in plaintext, with only the first two letters missing. .
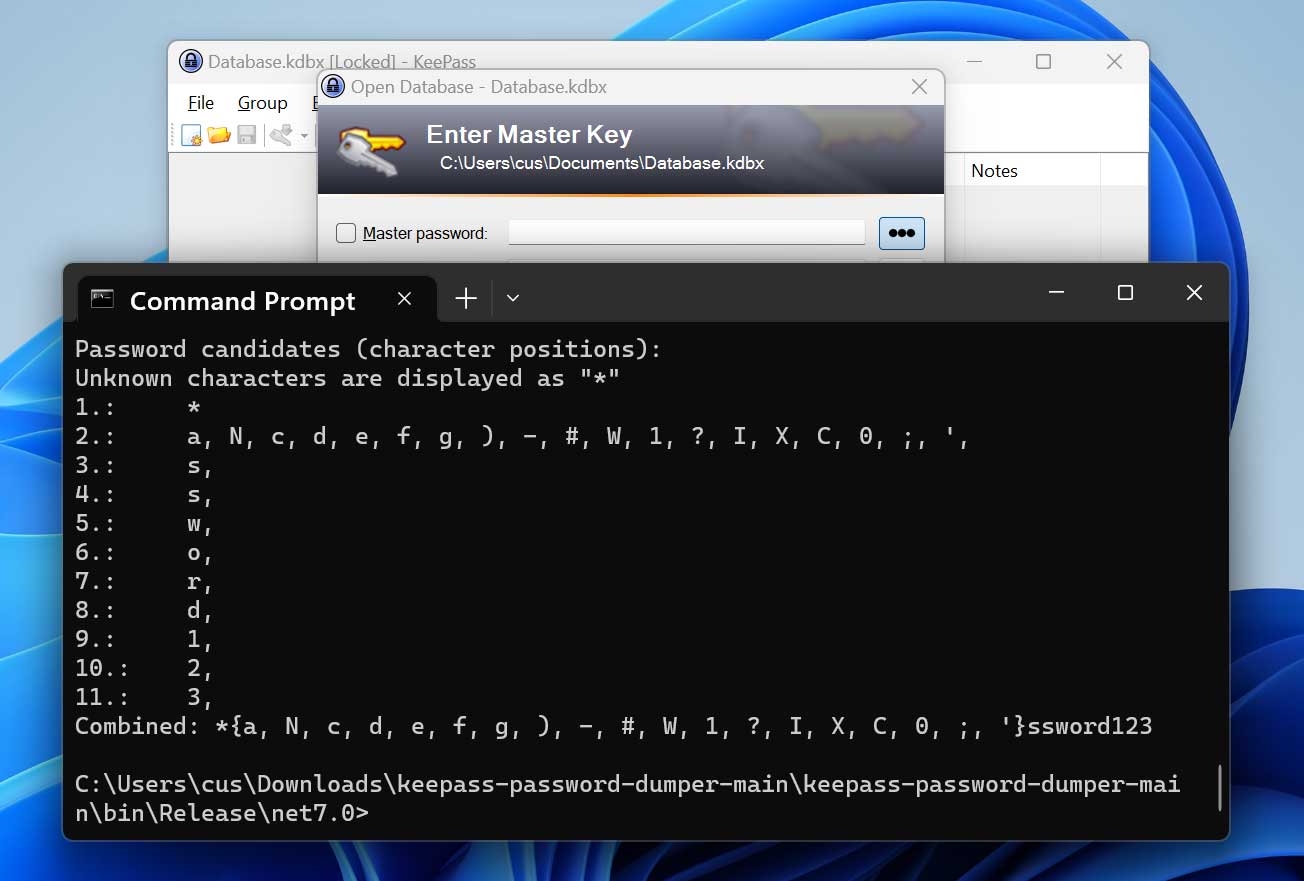
Source: BleepingComputer
Although this is not the full password, it would be fairly easy to determine which characters are missing.
The researcher also warns that master passwords used in the past may remain in memory, so they can be recovered even if KeePass no longer works on the hacked computer.
Fix to come
KeePass developer Dominik Reichl received the bug report and promised to deploy a fix for CVE-2023-32784 on version 2.54, due July 2023.
However, Reichl told BleepingComputer that KeePass version 2.54 is more likely to be released for users in about two weeks, so it should be available in early June.
Based on a discussion where Reichl expanded on his thoughts on the security flaw and potential mitigation strategies, two security enhancements are mentioned for the next version of KeePass:
- Make direct API calls to get/set the text box text, avoiding the creation of memory-managed strings that can leak secrets.
- Create dummy fragments containing random characters in process memory that will be approximately the same length as the user’s master password, obfuscating the real key.
KeePass 2.54 for Windows will have both, while macOS and Linux versions will only get the second improvement.
The developer has released a test build with the new security enhancements that mitigate the issue, so those who can accept unstable behavior can source it from here.
The PoC creator has confirmed that he can no longer replicate the attack with both security enhancements in place, so the fix appears to be effective.
Even after the release of the new version, the master password can still be stored in memory files. The researcher warns that to be 100% sure that it is not hiding on the system, you need to delete swap and hibernation files from your system, format your hard drive using “overwrite data” mode to prevent data recovery, and do a new OS installation.
For the most part, however, restarting the computer, clearing your swap file and hibernation files, and not using KeePass until the new version is released are reasonable security measures at this time.
Even then, for the best protection, be extremely careful not to download programs from untrusted sites and beware of phishing attacks that may infect your devices, giving malicious actors remote access to your device and your KeePass database.
[ad_2]
Source link
