[ad_1]

US software company Ivanti has patched an actively exploited zero-day vulnerability affecting its Endpoint Manager Mobile (EPMM) mobile device management software (formerly MobileIron Core).
Ivanti on Sunday released security patches for the unauthenticated remote API access vulnerability identified as CVE-2023-35078.
Patches can be installed by upgrade to EPMM 11.8.1.1, 11.9.1.1 and 11.10.0.2. They also target unsupported and end-of-life software versions below 11.8.1.0 (e.g. 11.7.0.0, 11.5.0.0)
Although Ivanti has published a security consulting to provide details of the security breach, the information is blocked by a login, as the article is only accessible with an account linked to Ivanti customer information.
“The article remains active behind our customers’ login credentials,” an Ivanti spokesperson told BleepingComputer when we asked for more details about the security flaw and confirmation that it was already being exploited in attacks.
“This vulnerability affects all supported versions 11.10, 11.9 and 11.8. Old versions/versions are also at risk,” says Ivanti in the security advisory seen by BleepingComputer.
“An unauthorized remote (internet-facing) actor can access users’ personally identifiable information and can allow limited server changes.”
Already exploited by attackers in the wild
After news of the vulnerability circulated among the cybersecurity community, security expert Kevin Beaumont warned that administrators should apply patches as soon as possible due to ease of exploitation.
Although the company has not publicly admitted that Day Zero is being actively exploited, the private bulletin says a “trusted source” has informed Ivanti that CVE-2023-35078 has been exploited in attacks against a limited number of customers.
“We have received information from a credible source indicating exploitation against a very small number of customers (e.g., less than 10). We have no more information to share at this time,” the private notice reads.
Ivanti added that the bug was not being exploited as part of a supply chain attack, saying it found “no indication that this vulnerability was maliciously introduced into our code development process.”
Some customers have also reported that Ivanti asked them sign non-disclosure agreements requesting more information regarding the CVE-2023-35078 vulnerability. However, BleepingComptuer was unable to independently confirm this.
“Ivanti has become aware of and has addressed a vulnerability affecting customers of Ivanti Endpoint Manager Mobile (formerly MobileIron Core),” Ivanti spokesperson BleepingComputer said after a second investigation asking to confirm the exploit in the attacks and whether the company will issue a public advisory.
“We immediately developed and released a fix and are actively engaging with customers to help them apply the fix.”
According to Shodan research shared by PwnDefend cybersecurity consultant Daniel Card, more than 2,900 MobileIron user portals are exhibited online, with three dozen linked to US local and state government agencies.
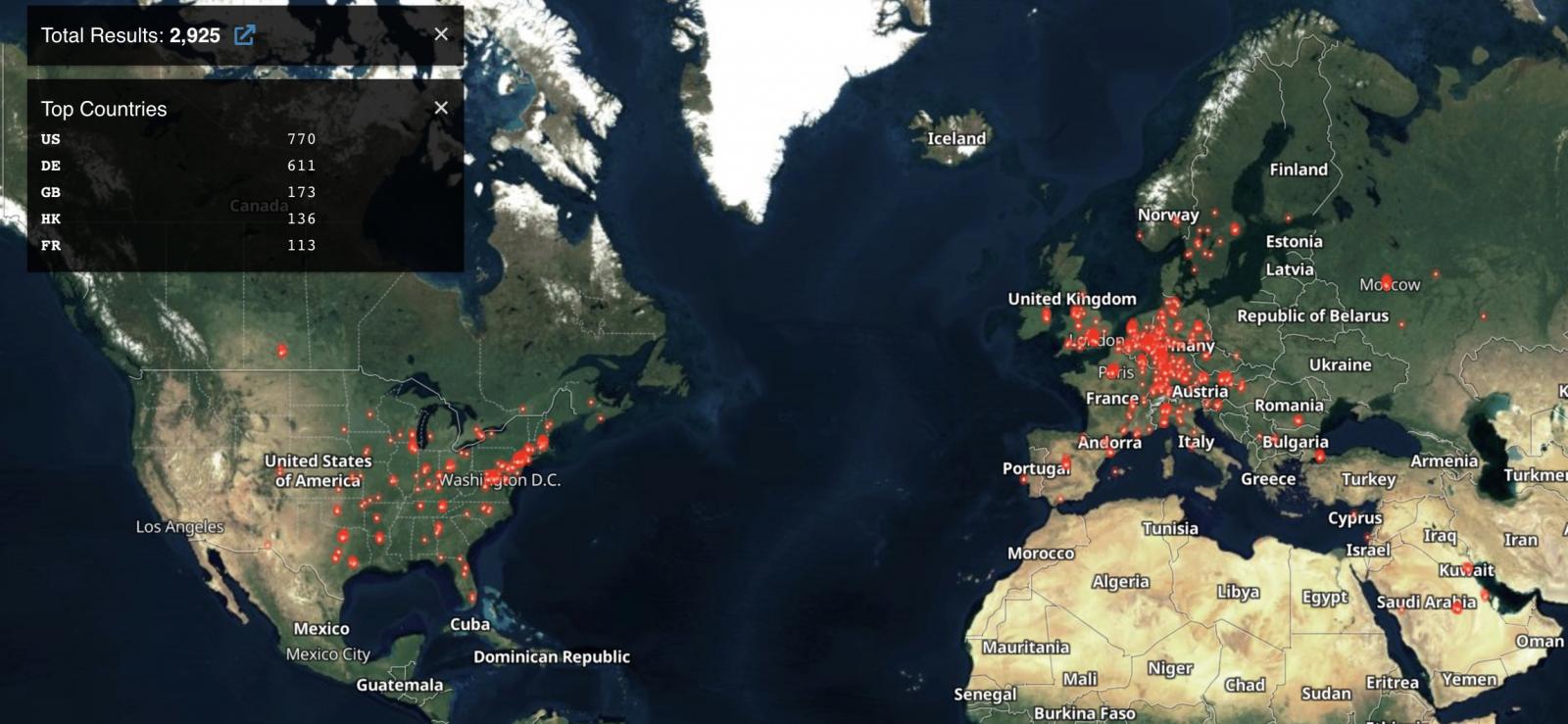
Most exposed servers are located in the United States, followed by Germany, the United Kingdom, and Hong Kong.
It is strongly recommended that all network administrators apply Ivanti Endpoint Manager Mobile (MobileIron) patches as soon as possible.
[ad_2]
Source link

