[ad_1]

Microsoft has discovered that an Iranian hacking group known as “Mint Sandstorm” was carrying out cyberattacks on US critical infrastructure in retaliation for recent attacks on Iranian infrastructure.
Mint Sandstorm is the new name for the Phosphorous Hacking Groupsuspected of working for the Iranian government and linked to the Islamic Revolutionary Guard Corps (IRGC).
In a new report, researchers from Microsoft’s Threat Intelligence team explain that a Mint Sandstorm subgroup went from surveillance in 2022 to direct attacks on US critical infrastructure.
The theory is that these intrusions are in retaliation for attacks on Iranian infrastructure that the country has attributed to the United States and Israel. These include destructive attacks on the Iranian railway system in June 2021 and a cyberattack causing outage at Iranian gas stations in October 2021.
Microsoft believes the Iranian government is now allowing state-sponsored threat actors more freedom when carrying out attacks, leading to an overall increase in cyberattacks.
“This targeting also coincided with a broader increase in the pace and scope of cyberattacks attributed to Iranian threat actors, including another Mint Sandstorm subgroup, which Microsoft observed beginning in September 2021,” warns Microsoft in its report today. report on Mint Sandstorm.
“The heightened aggression by Iranian threat actors appears to correlate with other moves by the Iranian regime as part of a new national security apparatus, suggest these groups are less restricted in their operations.”
Last year, the Treasury Department’s Office of Foreign Assets Control (OFAC) sanctioned ten individuals and two entities affiliated with Iran’s Islamic Revolutionary Guard Corps (IRGC), whose activities overlap with those attributed to Phosphorus.
Custom Malware Deployment
Microsoft says this new Mint Sandstorm subgroup routinely uses proof-of-concept exploits as they become public, as the company observed an attack using a Zoho ManageEngine PoC the same day it was released.
In addition to N-day exploits, which are code to take advantage of known vulnerabilities, threat actors have also used older vulnerabilities, such as Log4Shell, to breach unpatched devices.
Once they gain access to a network, hackers run a custom PowerShell script to gather information about the environment to determine if it is of high value.
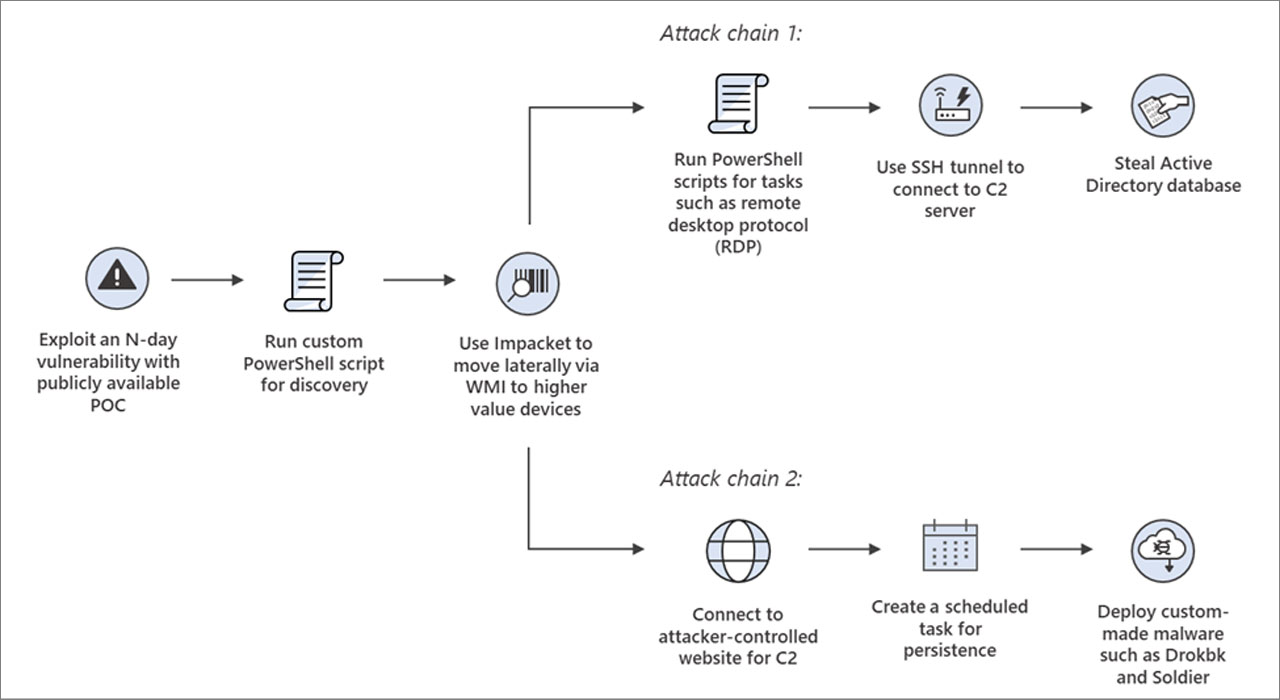
Hackers then use the Impacket framework to spread laterally across the network while conducting one of two attack chains.
The first attack chain leads to the theft of the target’s Windows Active Directory database, which can be used to obtain user credentials that can help hackers continue the intrusion or evade detection on the network.
Source: Microsoft
The second attack chain is to deploy custom backdoor malware called Drokbk and Soldier; both are used to maintain persistence on compromised networks and deploy additional payloads.
Microsoft says Drokbk (Drokbk.exe) [VirusTotal] is a .NET application that consists of an installer and a backdoor payload that retrieves a list of command and control server addresses from a README file on a controlled GitHub repository by the attacker.
The Soldier malware is also a .NET backdoor that can download and execute additional payloads and uninstall itself. Like Drokbk, it fetches a list of command and control servers from a GitHub repository.
In addition to using exploits to breach networks, Microsoft says attackers conducted low-volume phishing attacks against a small number of targeted victims.
These phishing attacks included links to OneDrive accounts hosting PDF files spoofed to contain Middle East security or political information. These PDFs also include links to a malicious Word template that used template injection to execute a payload on the device.
Source: BleepingComputer
These phishing attacks were used to deploy the CharmPower PowerShell Post-Operation Framework for persistence and execution of other commands.
“The capabilities seen in intrusions attributed to this Mint Sandstorm subgroup are concerning because they allow operators to conceal C2 communication, persist in a compromised system, and deploy a range of post-compromise tools with varying capabilities” , warns Microsoft.
“While the effects vary depending on operators’ post-intrusion activities, even initial access may allow unauthorized access and facilitate other behaviors that could harm the confidentiality, integrity, and availability of an environment.”
Microsoft recommends using attack surface reduction rules to block executables that do not meet certain criteria:
- Block executable files from running unless they meet a prevalence, age, or trustlist criteria
- Prevent Office apps from creating executable content
- Block process creations from PSExec and WMI commands
Because threat actors rely heavily on vulnerabilities for initial access to corporate networks, Microsoft recommends organizations apply security updates as soon as possible.
Particular attention should be paid to IBM Aspera Faspex, Zoho ManageEngine and Apache Log4j2 patches as they are known targets for threat actors.
[ad_2]
Source link
