[ad_1]

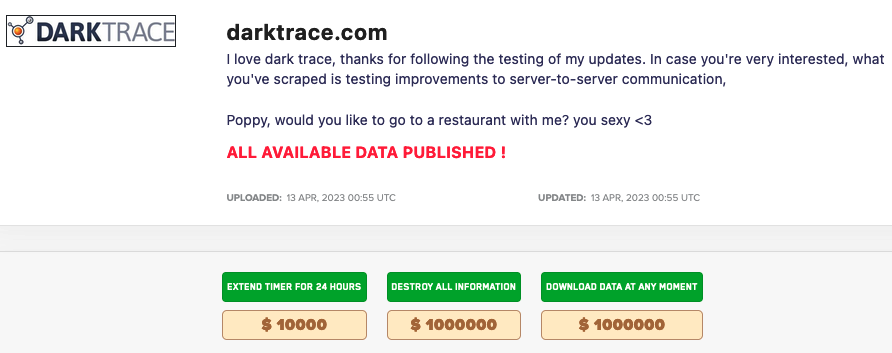
Cybersecurity firm Darktrace says it has found no evidence that the LockBit ransomware gang breached its network after the group added an entry to its dark web leak platform, implying that they stole data from company systems.
Hours after the gang claimed DarkTrace as a victim on their data leak site, the company conducted an investigation and found no evidence of a breach in their systems.
“Our security teams have performed a full review of our internal systems and see no evidence of a compromise,” Darktrace said.
On Friday, the company’s chief information security officer, Mike Beck, reiterated the same conclusion after a thorough investigation of their systems.
“We have completed a thorough security investigation into yesterday’s tweets from LockBit claiming they compromised Darktrace’s internal systems,” said Beck.
“We can confirm that there has been no compromise to our systems or any of our affiliate systems. Our service to our customers remains uninterrupted and operating normally and no further action is required.”
It is now clear that LockBit screwed up, confusing Darktrace with threat intelligence firm DarkTracer which tweeted about the gang’s getaway site flooded with fake victims.
“The reliability of the RaaS service operated by the LockBit ransomware gang appears to have diminished,” DarkTracer said.
“They seem to have become careless in running the service as fake victims and meaningless data started populating the list, which is left unattended.”
This isn’t the first time LockBit has claimed to have breached a cybersecurity firm’s systems by mistake or intentionally.
Last year in June, the ransomware gang also added Mandiant to their leaked website, claiming that over 350,000 files they allegedly stole would be released.
However, as happened with Darktrace, Mandiant told BleepingComputer that he had found no evidence of infringement.
In the end, LockBit’s claims that they hacked Mandiant turned out to be nothing more than a weak attempt to keep cybercriminal gang operation Evil Corp away following a Mandiant report linking the two after Evil Corp switched to deploying LockBit ransomware in their attacks to evade US sanctions.
Unlike this week, when Darktrace was listed as a victim due to confusion, Mandiant being tagged as a victim was prompted by LockBit fears of losing revenue if victims stopped paying ransoms since then. the US government sanctioned Evil Corp in December 2019.
[ad_2]
Source link
