[ad_1]

The seemingly harmless Microsoft OneNote file has become a popular file format used by hackers to spread malware and breach corporate networks. Here’s how to prevent malicious OneNote phishing attachments from infecting Windows.
To explain a bit about how we got Microsoft OneNote files to become the tool of choice for phishing attacks distributing malware, we first need to explain how we got here.
Threat actors have been abusing macros in Microsoft Word and Excel documents for years to download and install malware on Windows devices.
After Microsoft has finally disabled macros by default in Word and Excel Office documents, threat actors began to turn to other less commonly used file formats to distribute malware, such as ISO files and password-protected ZIP archives.
These were popular file formats, as a Windows bug allowed ISO image files to bypass Mark-of-the-Web (MoTW) security warnings, and the popular 7-Zip archive utility did not spread MoTW flags to files extracted from ZIP archives.
However, after the two 7-Zip And Fixed Windows these bugs, Windows again started displaying creepy security warnings when a user tried to open files in downloaded ISO and ZIP files, forcing threat actors to find another file format to use in the attacks.
Source: BleepingComputer
Since mid-December, threat actors have turned to another file format to distribute malware: Microsoft OneNote attachments.
Why Microsoft OneNote?
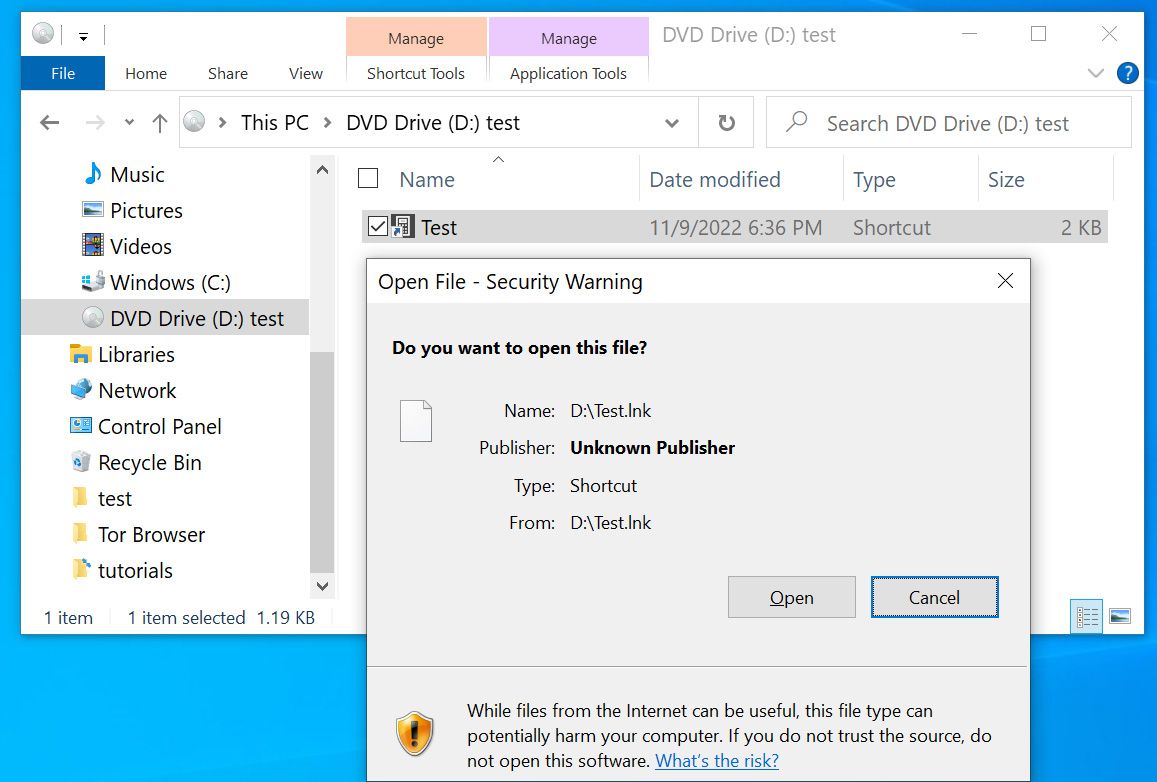
Microsoft OneNote attachments use the ‘.A‘ and are an attractive choice, as they do not distribute malware via macros or vulnerabilities.
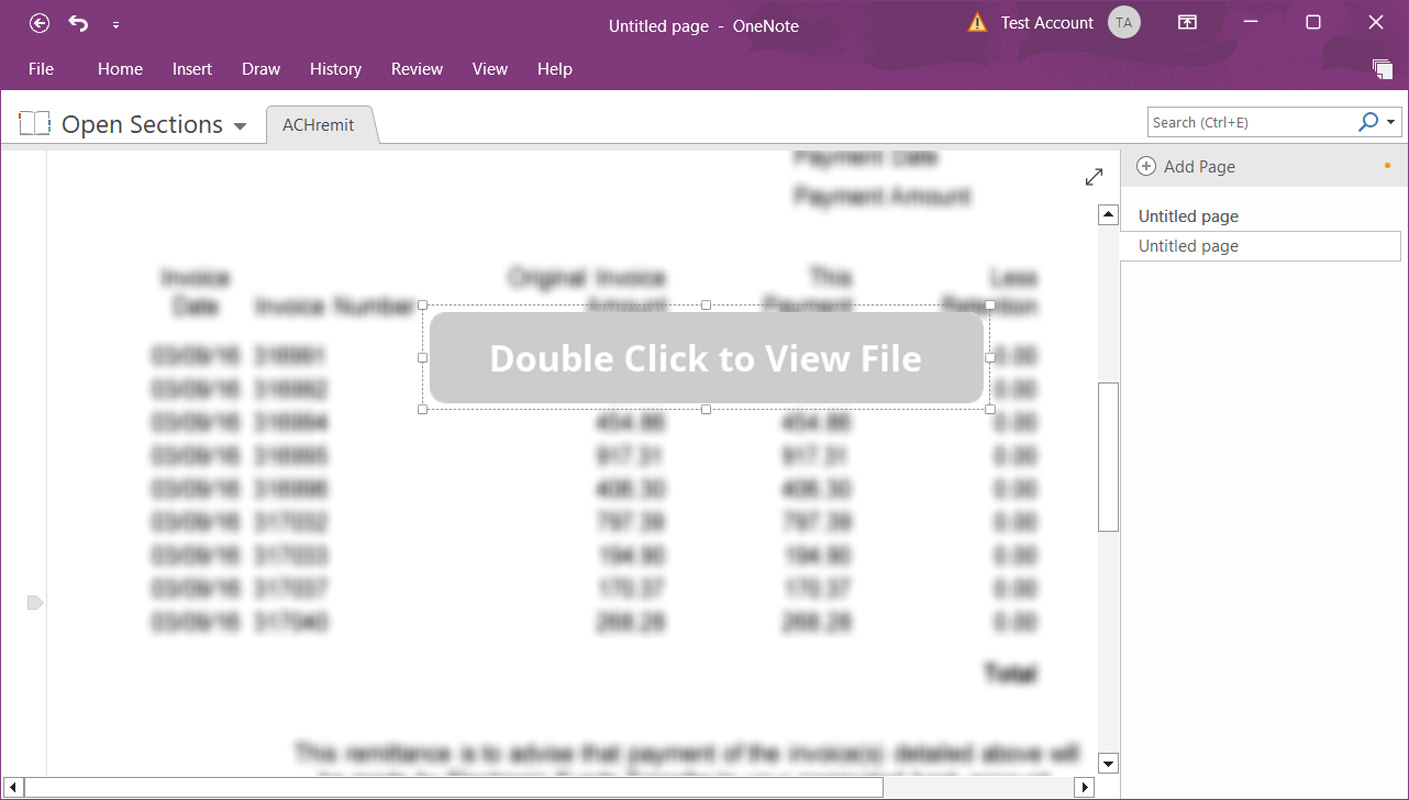
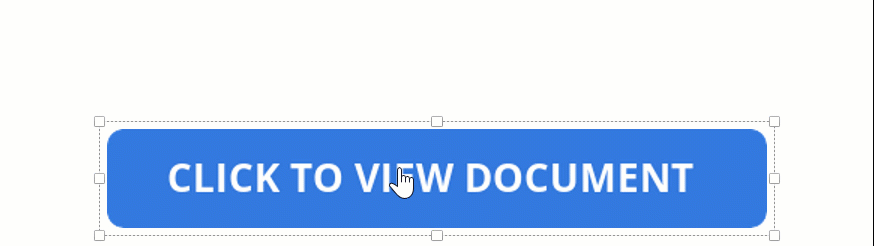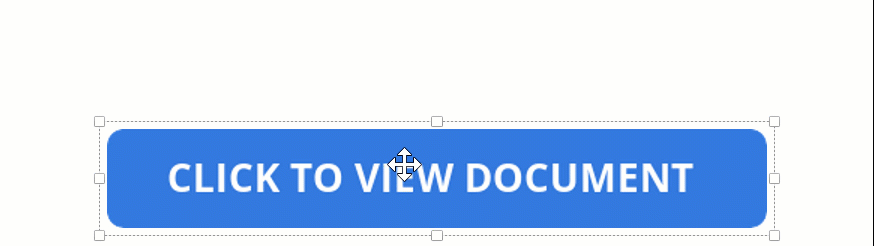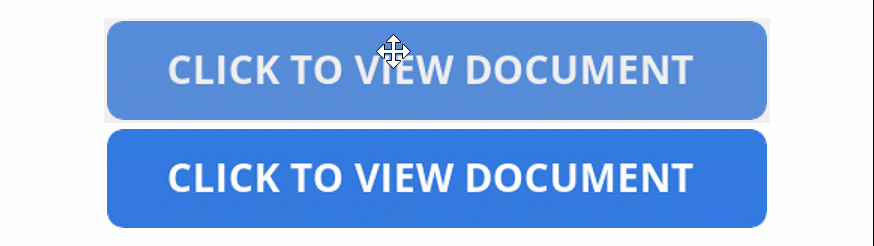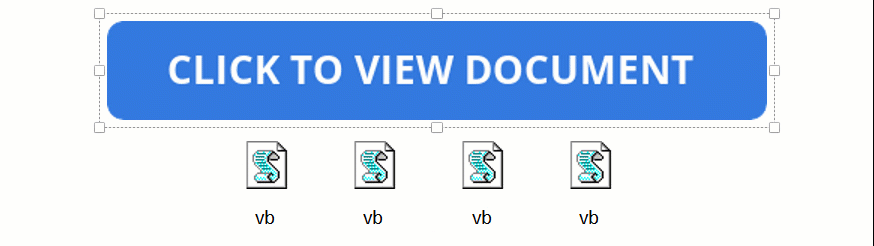
Instead, threat actors create complex templates that appear to be a protected document with a message to “double-click” a design element to view the file, as shown below.
Source: BleepingComputer
What you don’t see in the attachment above, however, is that the “double click to show file” actually hides a series of embedded files that sit below the button layer, as shown below below.
Source: BleepingComputer
When you double-click the button, you double-click the embedded file and cause the file to launch.
Although double-clicking an embedded file displays a security warning, as we know from previous phishing attacks abusing Microsoft Office macros, users usually ignore the warnings and allow the file to run anyway.
Unfortunately, it only takes one user to accidentally allow a malicious file to run across an entire corporate network to be compromised by a large-scale ransomware attack.
And it’s not theoretical, because in some Microsoft OneNote QakBot campaigns, security researchers found that they ultimately lead to a ransomware attack, like BlackBastaon a compromised network.
How to Block Malicious Microsoft OneNote Files
The best way to prevent malicious Microsoft OneNote attachments from infecting Windows is to block the ‘.A‘ on your secure mail gateways or mail servers.
However, if this is not possible for your environment, you can also use Microsoft Office Group Policies to restrict the launch of inline attachments in Microsoft OneNote files.
First, install the Microsoft 365/Microsoft Office Group Policy Templates to get started with Microsoft OneNote policies.
Now that the policies are installed, you will find new Microsoft OneNote policies named “Disable Embedded Files” and “Blocked Embedded File Extensions” as shown below.
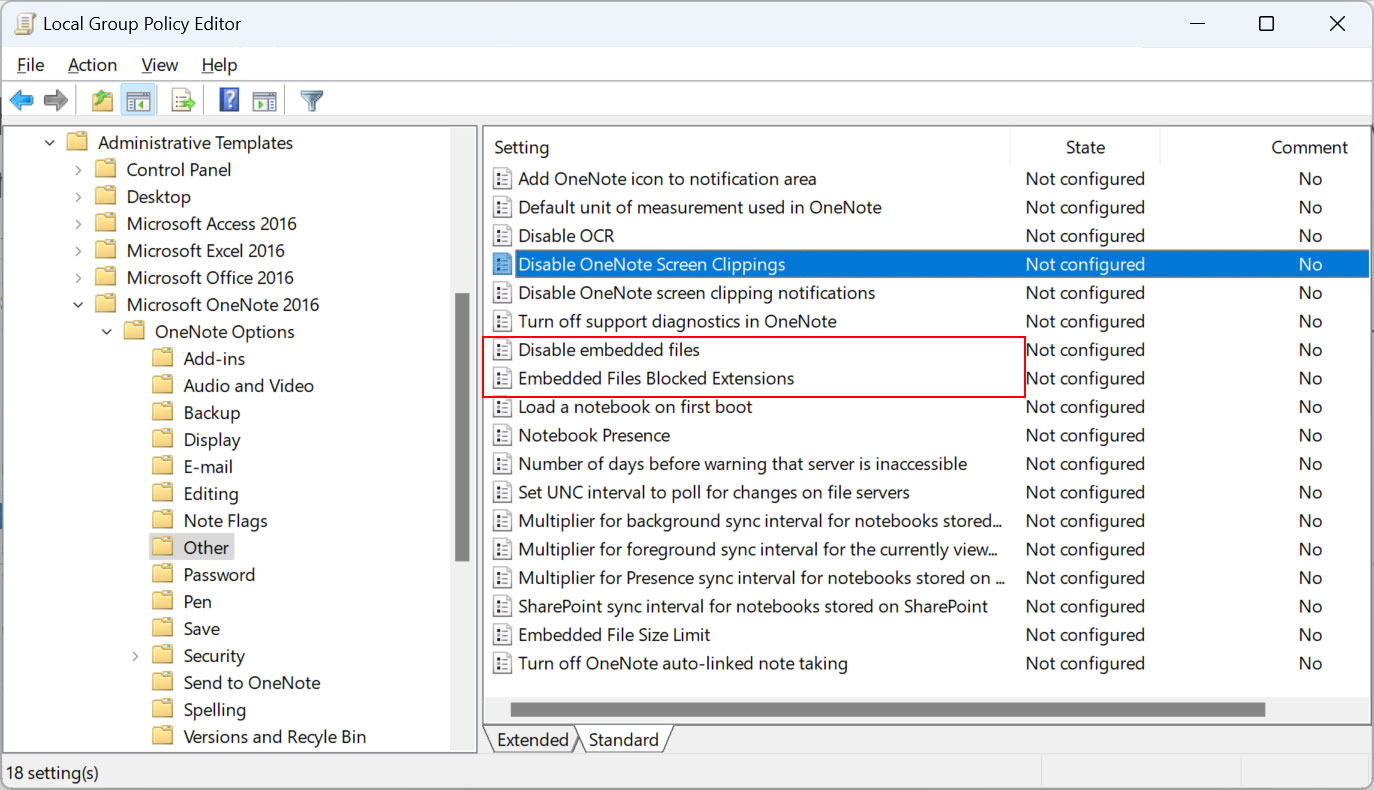
Source: BleepingComputer
THE ‘Disable embedded files‘ Group Policy is the most restrictive as it prevents all embedded OneNote files from launching. You should enable this option if you don’t have any use cases for using embedded OneNote attachments.
“To disable the ability to embed files on a OneNote page, so that users cannot transmit files that may not be detected by anti-virus software, etc.,” reads the description of the policy. band.
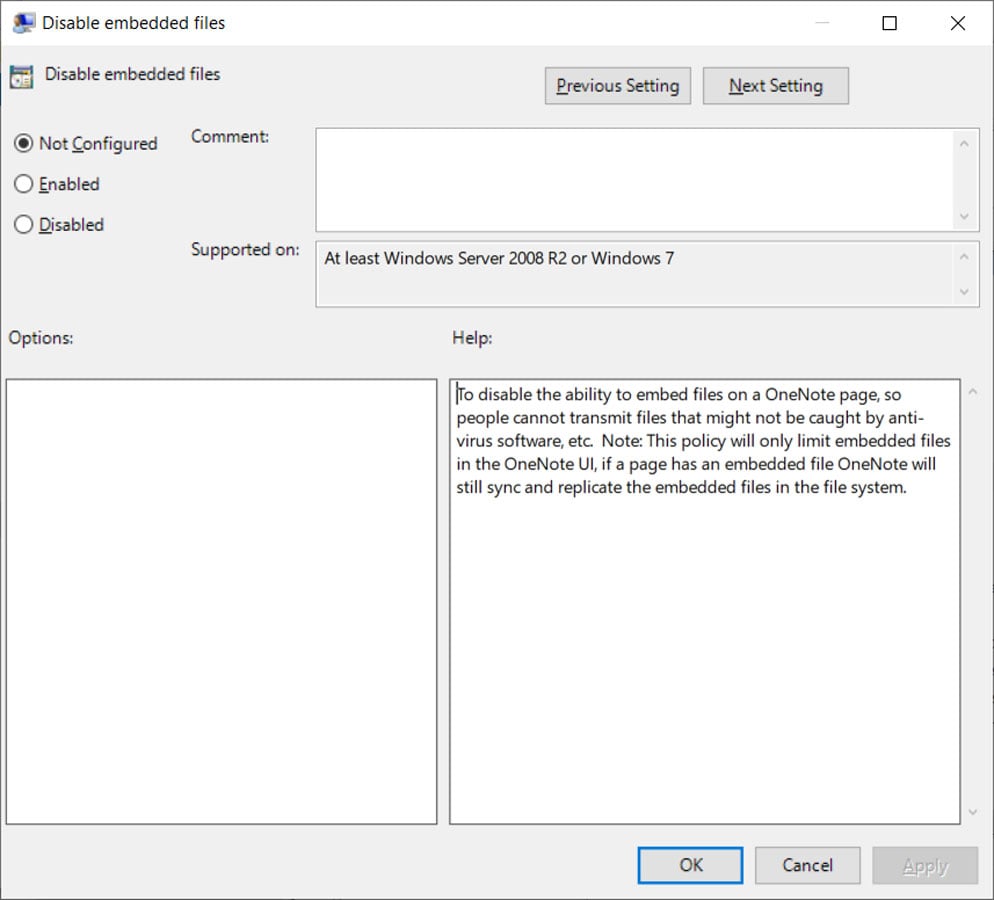
Source: BleepingComputer
When enabled, the following Windows registry key will be created. Note that the paths may differ depending on your version of Microsoft Office.
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\office\16.0\onenote\options]
“disableembeddedfiles”=dword:00000001
Now, when a user attempts to open attachments embedded in a Microsoft OneNote document, they receive the following error.
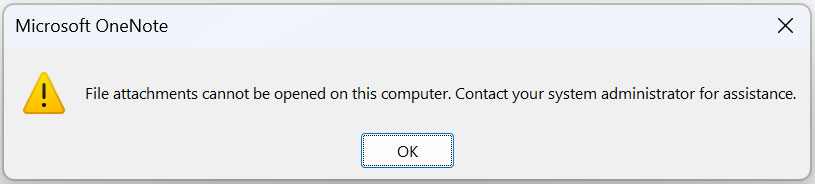
Source: BleepingComputer
A less restrictive, but potentially more dangerous option is the ‘Blocked extensions of embedded files‘ Group Policy, which allows you to enter a list of embedded file extensions that will be blocked from opening in a Microsoft OneNote document.
“To prevent users in your organization from opening an attachment of a specific file type from a Microsoft OneNote page, add the extensions you want to disable using this format: ‘.ext1;.ext2;’ ,” reads the description of the policy.
“If you want to disable opening any attachments from a OneNote page, see the Disable Embedded Files policy. You cannot block embedded audio and video recordings (WMA and WMV) with this policy, see you instead to the Disable Embedded Files policy.”
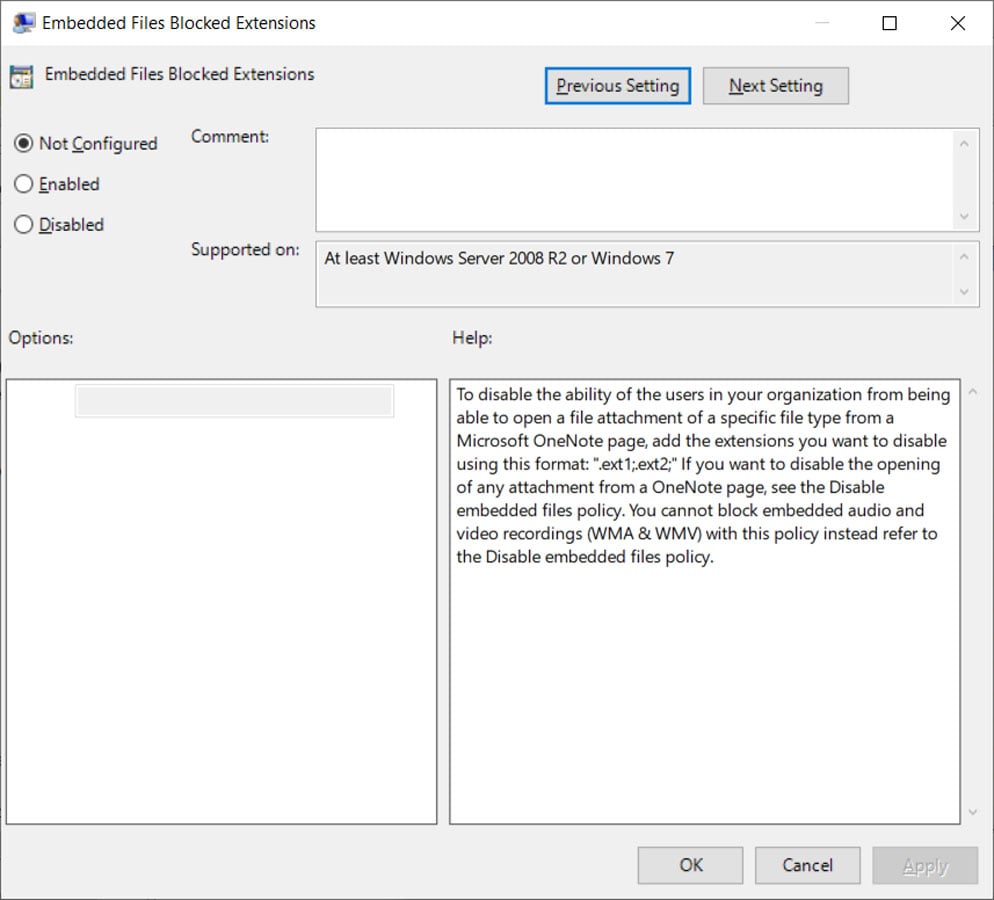
Source: BleepingComputer
When enabled, the following Windows registry key will be created with the list of blocked extensions you entered.
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\office\16.0\onenote\options\embeddedfileopenoptions]
“blockedextensions”=”.js;.exe;.bat;.vbs;.com;.scr;.cmd;.ps1″
Now, when a user attempts to open a blocked file extension in a Microsoft OneNote document, they receive the following error.
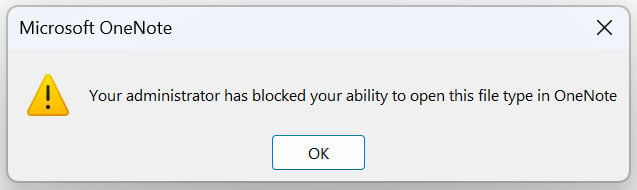
Source: BleepingComputer
Some suggested file extensions to block are .js, .exe, .com, .cmd, .scr, .ps1, .vbsAnd .lnk. However, as hackers discover new file extensions to abuse, this list can be bypassed by other types of malicious files.
While blocking any type of file isn’t always a perfect solution due to the demands of an environment, the results of doing nothing to limit the misuse of Microsoft OneNote files can be even worse.
Therefore, it is strongly advised to block OneNote attachments, or at least abuse of built-in file types, in your environment to prevent a cyberattack.
[ad_2]
Source link
