[ad_1]

Hybrid phishing attacks continue to pose a clear and present danger to all organizations. How can these threats be mitigated to reduce their impact? A combination of targeted security tools and a strong cybersecurity culture are the two-pronged approach organizations can use to protect their network from attack.
According to the cyber-intelligence report of Agar, hybrid phishing attacks increased by 625%. One of the most damaging is callback phishing, also known as TOAD (Telephone-Oriented Attack delivery).
First appeared in the wild in March 2021 as BazarCallthe attacks were mounted to install ransomware on corporate networks.
These attacks use two vectors, usually starting with an email and later followed by one or more voice calls. First, the threat actor sends what appears to be a legitimate, high-value invoice for a service. Next, the recipient is prompted to call a number to investigate the current charge.
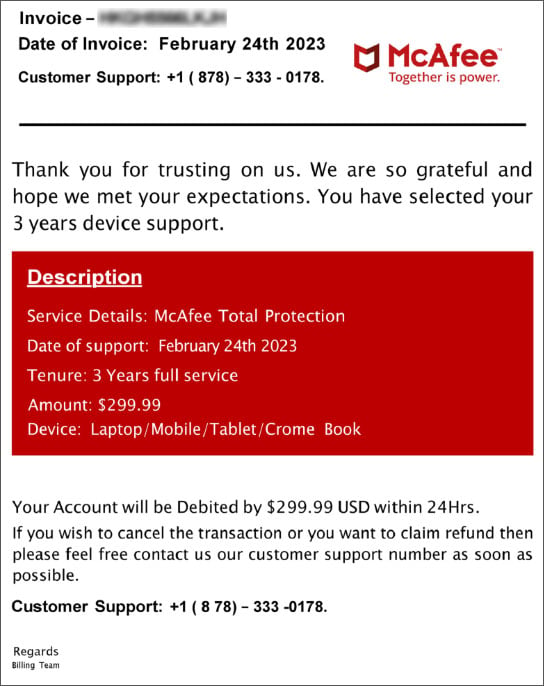
At this point, the attacker will use more social engineering tactics to obtain network access information or install remote access software.
Used as bait, the initial email is often linked to older subscriptions that the recipient may know about but thought they had canceled. Connecting these messages to live verification voice calls makes callback phishing so dangerous. Attackers have a direct connection to their target, often using fake tech support calls that convince their victims to install a ClickOnce executable named “support.Client.exe”.
As organizations look to their post-pandemic future, it is imperative to secure the networks and remote workers who now represent a significant percentage of their workforce.
What is clear, and as ProofPoint illustrated in their report, is that developing a strong cybersecurity culture is the most effective defense against personalized attacks, such as callback phishing.
The future of cyberattacks will see phishing attacks proliferate. Additionally, hybrid attacks are becoming more common as they use multiple approaches that are often more effective than single attack vectors.
Culture of safety
It is often said that end users are the weakest link in an organization’s security. Low levels of cybersecurity awareness can be the source of successful cyberattacks, especially attacks such as callback phishing.
Organizations need to have a strong security culture and a first step to building cybersecurity awareness is to implement training programs specifically for phishing messages that instill fear or a sense of urgency, unexpected bills and requests to initiate a phone call or install software.
Additionally, increase investments in tools designed to detect and prevent anomalous activity, such as the installation of unrecognized software or the exfiltration of sensitive data.
Companies must, of course, have robust and comprehensive security systems in place to protect against phishing attacks. Services such as Mimecast and the range of Microsoft Defender options available allow organizations to enhance their protection against cyber threats.
Practice Zero Trust
The adoption of a Zero Trust approach to cybersecurity has grown. It’s essential to appreciate this because cybersecurity has become as perimeter-less as remote working.
Focusing on data, hosted services and identities becomes paramount in a Zero Trust environment. Identities are key here. Recall phishing is not an attack on the physical infrastructure of the network, but on the end users who access these resources, often remotely.
Callback phishing attacks can also be used against service desks. Almost half of organizations have not implemented secure user verification for help desk calls, opening vulnerabilities for targeted attacks.
THE Specops Secure Service Desk is a practical example of how a Zero Trust security environment can be effectively managed. Specops Secure Service Desk increases security by applying strong authentication methods to verify callers, minimizing the risk of identity theft.
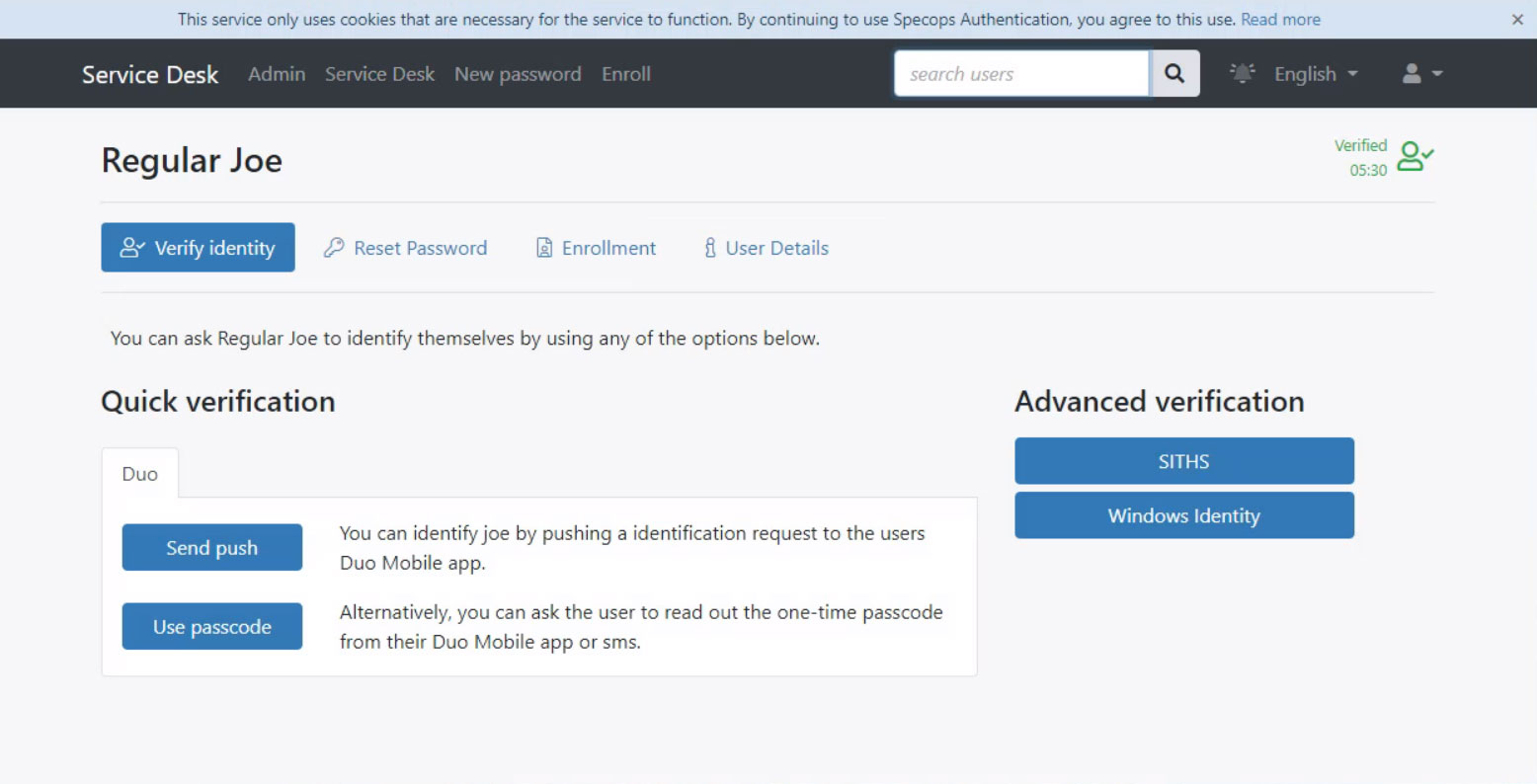
Service desks should have robust and comprehensive security with access to reset passwords, verify users, and unlock accounts. Desktop operators must also have high levels of cybersecurity awareness and make conscious decisions that protect the network and user access.
The work environment has completely changed, which cybercriminals are only too aware of. Therefore, protecting critical systems against cyberattacks requires a multidimensional approach to security.
Taking a Zero Trust stance is a robust approach, but with attacks like callback phishing using multiple attack channels, protection must also be multi-functional. And never forget that often with these attacks, a strong and resilient security culture will always be the most effective first line of defense.
Sponsored and written by Specops software
[ad_2]
Source link
