[ad_1]

Hackers believed to be working for Russia have started using a new code execution technique that relies on mouse movement in Microsoft PowerPoint presentations to trigger a malicious PowerShell script.
No malicious macros are needed for the malicious code to run and download the payload, for a more insidious attack.
A report by threat intelligence firm Cluster25 states that APT28 (aka “Fancy Bear”), a threat group attributed to Russian GRU (Russian General Staff Main Intelligence Directorate), used the new technique to deliver the Graphite malware as recently as September 9.
The threat actor lures targets with a PowerPoint (.PPT) file allegedly linked to the Organization for Economic Co-operation and Development (OECD), an intergovernmental organization that works to drive economic progress and trade around the world .
Inside the PPT file, there are two slides, both containing instructions in English and French for using the interpretation option in the Zoom video conferencing application.

source: Cluster25
The PPT file contains a hyperlink that acts as a trigger to launch a malicious PowerShell script using the SyncAppvPublishingServer utility. This technique has been documented since June 2017. Several researchers at the time explained how the infection works without a malicious macro nested in an Office document (1, 2, 3, 4).
Based on the found metadata, Cluster25 says that the hackers prepared the campaign between January and February, although the URLs used in the attacks appeared to be active in August and September.
The source: Cluster25
Researchers say the threat actor is targeting entities in the defense and government sectors of European Union and Eastern European countries and believe the espionage campaign is ongoing.
Chain of infection
When the decoy document is opened in presentation mode and the victim hovers the mouse over a hypertext link, a malicious PowerShell script is activated to download a JPEG file (“DSC0002.jpeg”) from a Microsoft OneDrive account.
The JPEG is an encrypted DLL file (lmapi2.dll), which is decrypted and dropped into the ‘C:\ProgramData\’ directory, later run via rundll32.exe. A registry key for persistence is also created for the DLL.
.png)
Next, lmapi2.dll retrieves and decrypts a second JPEG file and loads it into memory, on a new thread previously created by the DLL.
Cluster25 specifies that each of the strings in the newly retrieved file requires a different XOR key for deobfuscation. The resulting payload is Graphite malware in portable executable (PE) form.
Graphite abuses the Microsoft Graph API and OneDrive to communicate with the command and control (C2) server. The threat actor accesses the service using a fixed client ID to obtain a valid OAuth2 token.
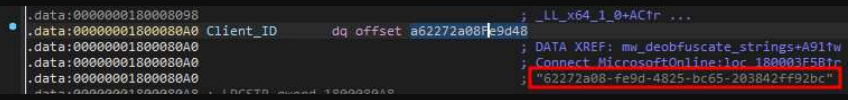
With the new OAuth2 token, Graphite queries Microsoft GraphAPIs for new commands by listing child files in the check OneDrive subdirectory, the researchers explain.
“If a new file is found, the content is downloaded and decrypted using an AES-256-CBC decryption algorithm,” explains Cluster25, adding that “the malware enables remote command execution by allocating a new region of memory and executing received shellcode by calling a new dedicated thread.
The purpose of Graphite malware is to allow the attacker to load other malware into system memory. It was documented in January by researchers at Trellix, a merger from McAfee Enterprise and FireEye, who named it so specifically because it leverages the Microsoft Graph API to use OneDrive as C2.
The campaign that Trellix investigated used Excel documents titled “parliament_rew.xlsx” and “Missions Budget.xlsx” that appeared to target government employees and individuals in the defense industry.
Based on code similarities to 2018 malware samples, targeting, and the infrastructure used in the attacks, Trellix assigned Graphite to APT28 with low to moderate confidence.
[ad_2]
Source link
