[ad_1]
Security researchers discovered attacks from an advanced threat actor that used “a previously unknown malicious framework” called CommonMagic and a new backdoor called PowerMagic.
Both malware have been used since at least September 2021 in operations that continue to this day and target organizations in the government, agriculture, and transportation sectors for espionage purposes.
New Discontinued Malicious Toolkit
Researchers from cybersecurity firm Kaspersky say hackers are interested in collecting data from victims in Donetsk, Lugansk and Crimea.
Once inside the victim network, the attackers behind the CommonMagic spying campaign can use separate plugins to steal documents and files (DOC, DOCX, XLS, XLSX, RTF, ODT, ODS, ZIP, RAR, TXT, PDF) from USB devices.
The malware used can also take screenshots every three seconds using the Windows graphics device interface (GDI) APIs.
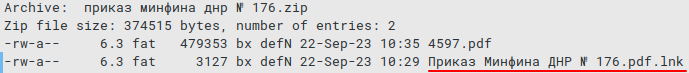
Researchers believe that the initial infection vector is spear phishing or a similar method to deliver a URL pointing to a ZIP archive with a malicious LNK file.
A decoy document (PDF, XLSX, DOCX) in the archive hijacked the target user from the malicious activity that started in the background when the LNK file disguised as a PDF was launched.
source: Kaspersky
Kaspersky says activating the malicious LNK would lead to infecting the system with a previously unknown PowerShell-based backdoor that the researcher named PowerMagic after a string in the malware’s code.
The backdoor communicates with the command and control (C2) server to receive instructions and upload results using OneDrive and Dropbox folders.
Following the PowerMagic infection, the targets were infected with CommonMagic, a collection of malicious tools that researchers had not seen prior to these attacks.
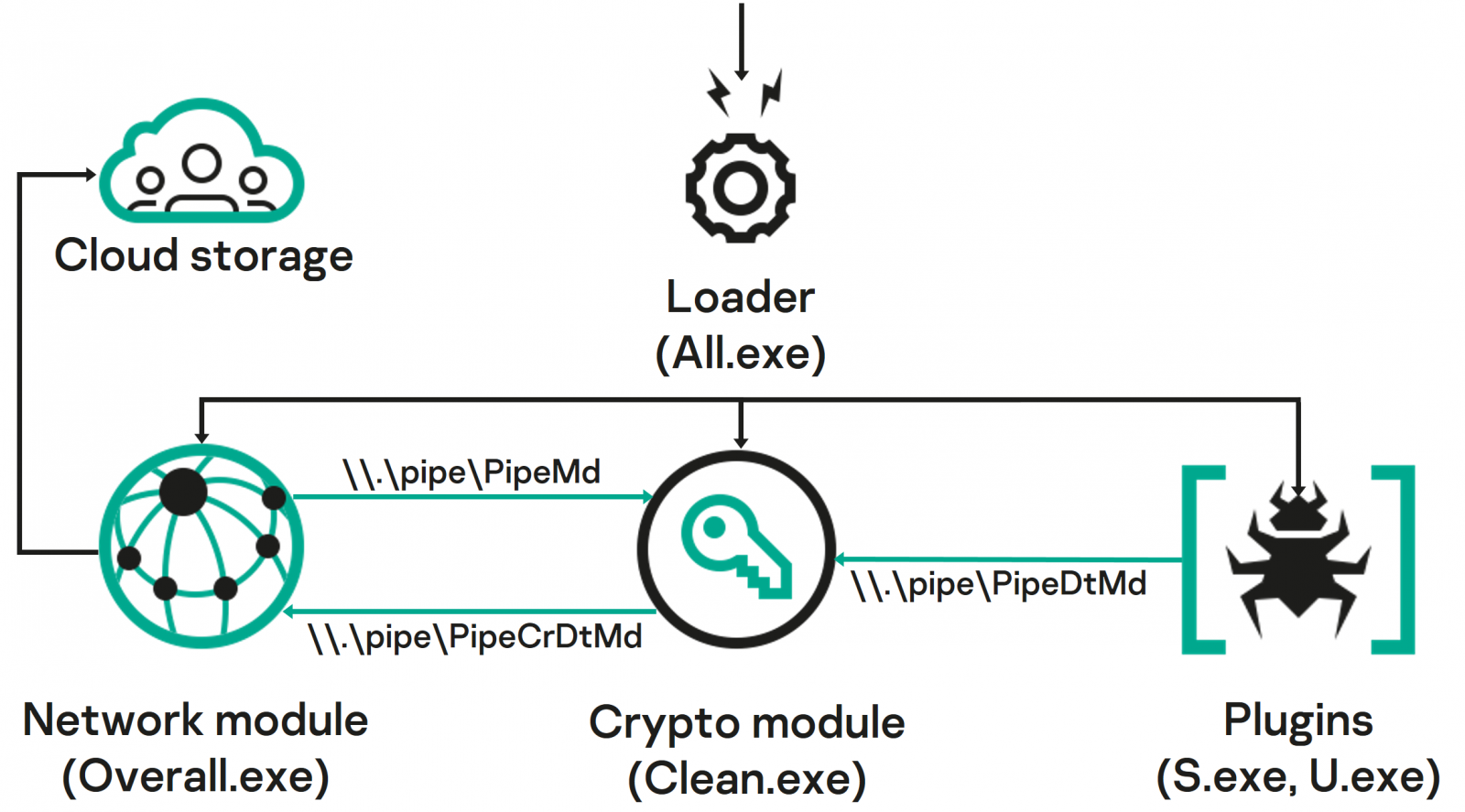
The CommonMagic framework has several modules that start as standalone executables and use named pipes to communicate.
by Kaspersky revealed analysis that hackers have created dedicated modules for various tasks, from interacting with the C2 to encrypting and decrypting command server traffic, stealing documents and taking screenshots.
source: Kaspersky
Data exchange with the C2 also takes place via a OneDrive folder and files are encrypted using the RC5Single open-source library with custom sequence – Hwo7X8p – at the start of encryption.
Hiding behind ordinary tactics
The malware or methods seen in CommonMagic attacks are neither complex nor innovative. A chain of infection involving malicious LNK files in ZIP archives has been observed with multiple threat actors.
Incident response company Security Joes announced last month the discovery of a new backdoor called IceBreaker which was delivered from a malicious LNK in a ZIP archive.
A similar method was observed in a ChromeLoader Campaign which relied on a malicious LNK to run a batch script and extract the contents of a ZIP container to retrieve the final payload.
However, the closest to CommonMagic’s technique is a threat actor that Cisco Talos tracks as Yoro Trooperwho engaged in cyber espionage activities by using phishing emails delivering malicious LNK files and decoy PDF documents locked in ZIP or RAR archive.
Despite the unconventional approach, however, CommonMagic’s method has proven effective, says Kaspersky.
Researchers found an active infection in October last year, but tracked a few attacks from this threat actor dating back to September 2021.
Leonid Besverzhenko, a security researcher with Kaspersky’s Global Research and Analytics team, told BleepingComputer that the PowerMagic backdoor and CommonMagic framework have been used in dozens of attacks.
Although CommonMagic’s activity appears to have started in 2021, Besverzhenko says the adversary intensified its efforts last year and continues to be active today.
By combining unsophisticated techniques that have been used by several actors and original malicious code, the hackers managed to make it impossible to connect to other campaigns at this time.
A Kaspersky spokesperson told BleepingComputer that “the limited victimology and the Russian-Ukrainian conflict-themed decoys suggest that the attackers likely have a specific interest in the geopolitical situation in that region.”
[ad_2]
Source link
