[ad_1]

Hackers hijack online stores to display modern and realistic fake payment forms to steal credit cards from unsuspecting customers.
These payment forms are displayed as modal HTML content overlaid on top of the main web page, allowing the user to interact with the login forms or notification content without leaving the page.
When modals are active, background content is sometimes dimmed or blurred to draw attention to the modal content.
In a new report from MalwarebytesMageCart skimmers are now hijacking legit online store checkout pages to show their own fake checkout forms as modals to steal customers’ credit cards.
These modals stand out because they sometimes look even better than the original, having no visual signs that could lead one to suspect that they are not real.
Better than the real thing
One case highlighted in Malwarebytes’ report involves a Parisian PrestaShop-based travel accessories store compromised by the new Kritec campaign.
Kritec is a JavaScript credit card skimmer that Malwarebytes first detected on Magento stores in March 2022so the same threat actor is probably behind it.
Malwarebytes reports that the skimmer that infected the page is rather complex and its code is heavily obfuscated with base64 encoding.
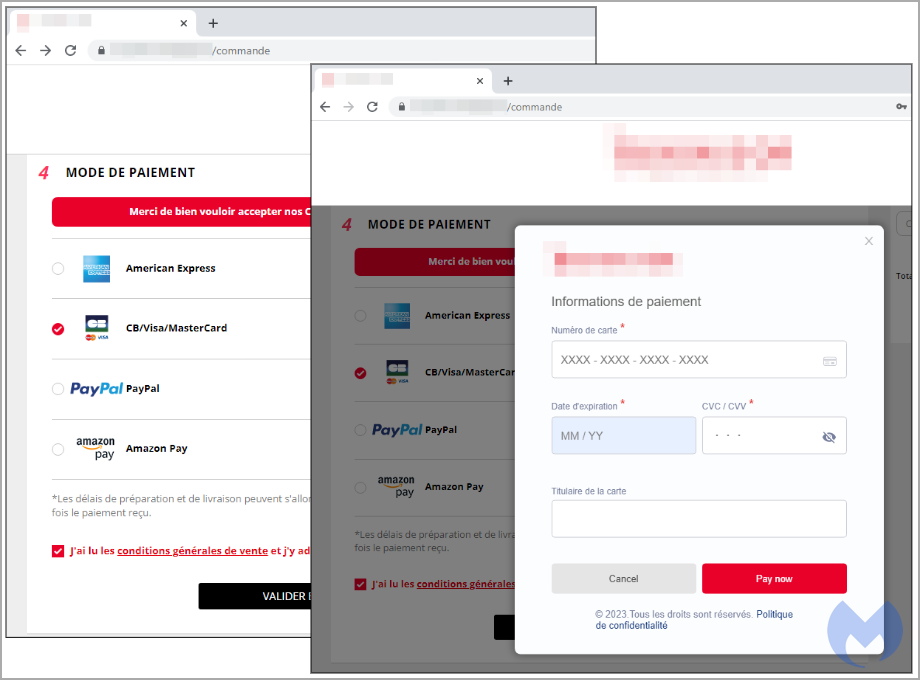
Upon reaching the infected site’s checkout page, instead of seeing the site’s checkout form, the malicious script displays a modal that features the brand’s logo, the correct language (English), and sleek interface elements.
However, this fake payment form is designed to steal customers’ credit card details and send them back to hackers.
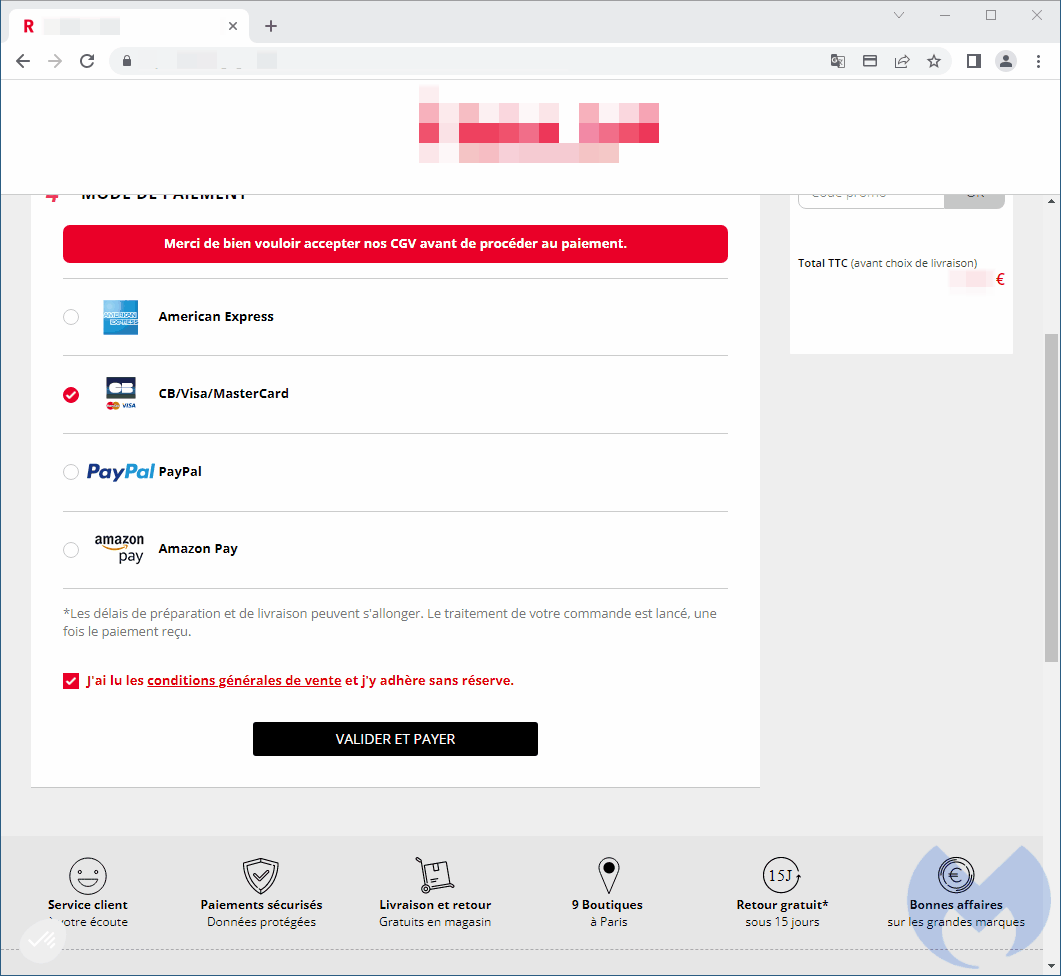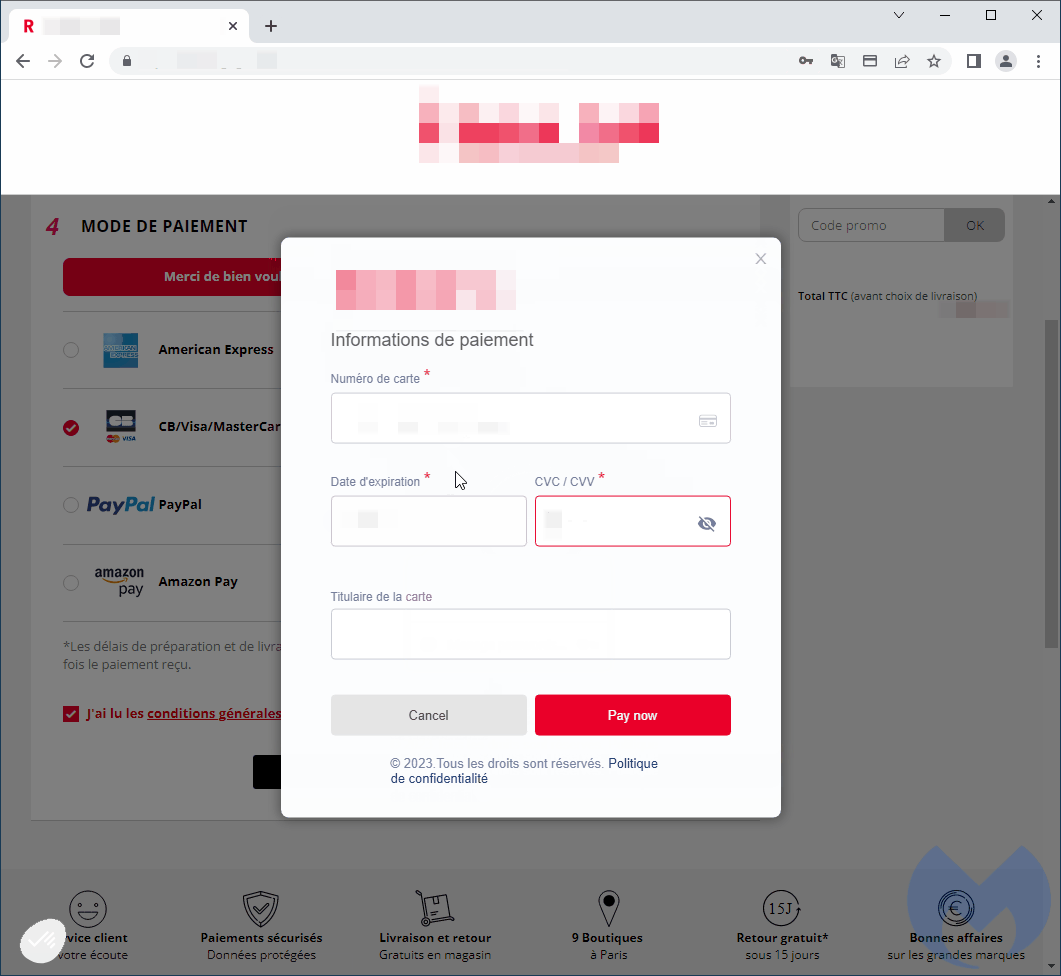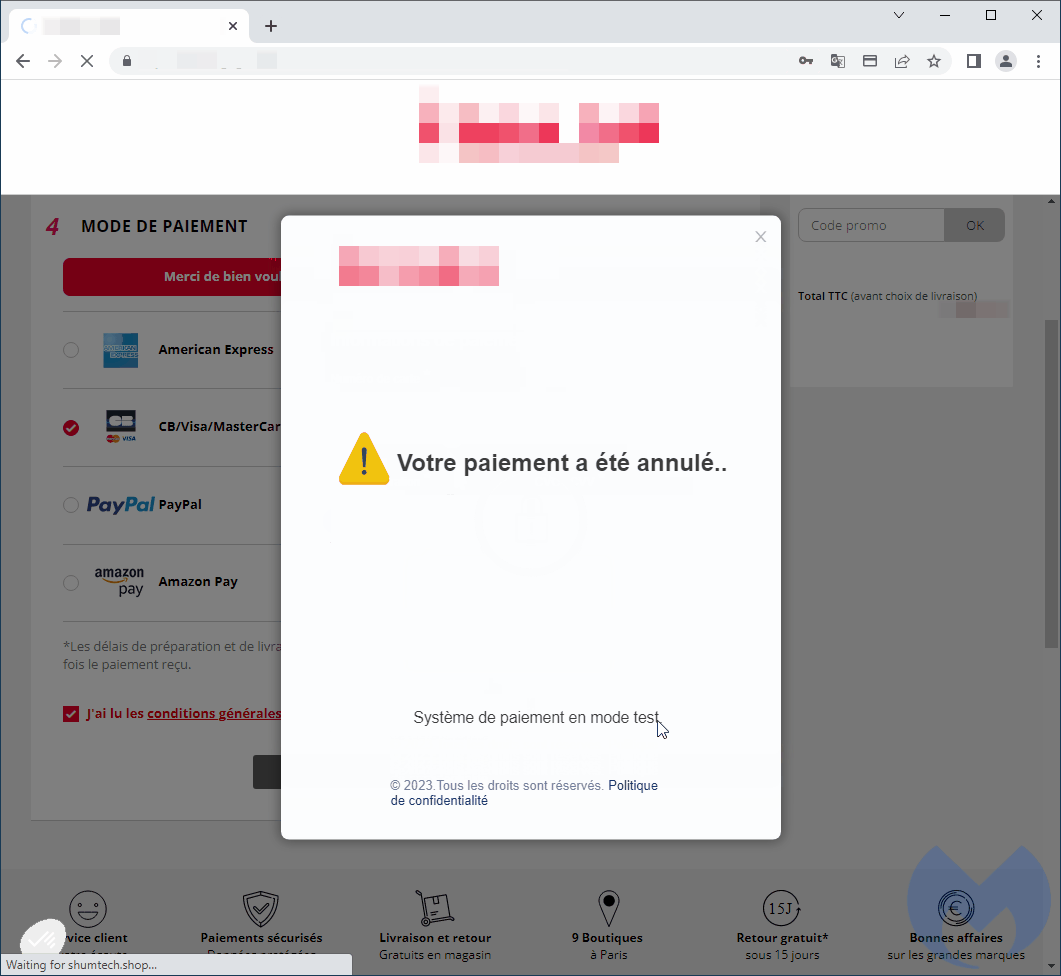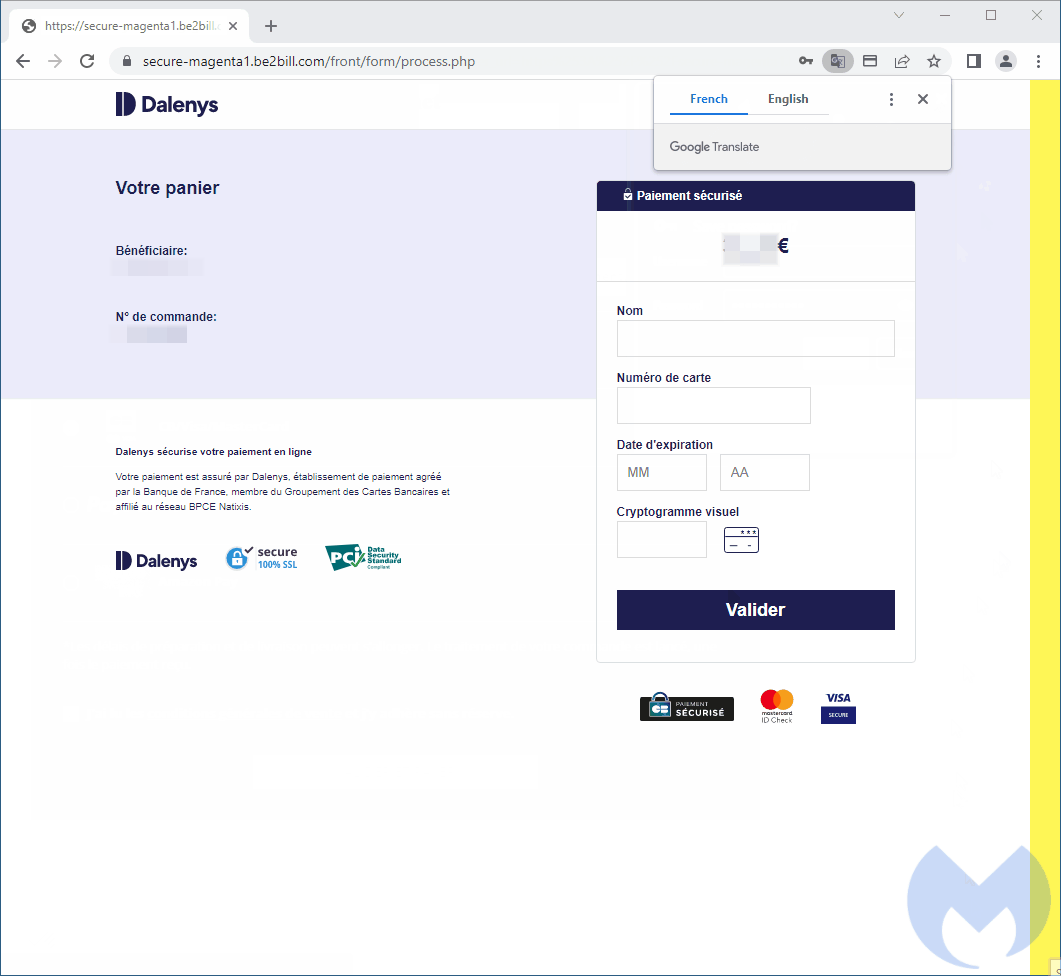
After buyers enter their details on the modal, it momentarily displays a fake charger and then displays a fake error, redirecting the user to the real payment URL.
However, in the background, threat actors have already stolen all entered details including credit card number, expiration date, CVV number and card holder name.
Additionally, the skimmer drops a cookie on users who were successfully targeted to prevent the malicious modal from being loaded again on the same or another site. This avoids collecting duplicate data and minimizes the exposure of the operation.
Malwarebytes analysts blocked the credit card skimmer script to allow the original payment form to load, and the comparison between the two leaves the authentic undone aesthetically.
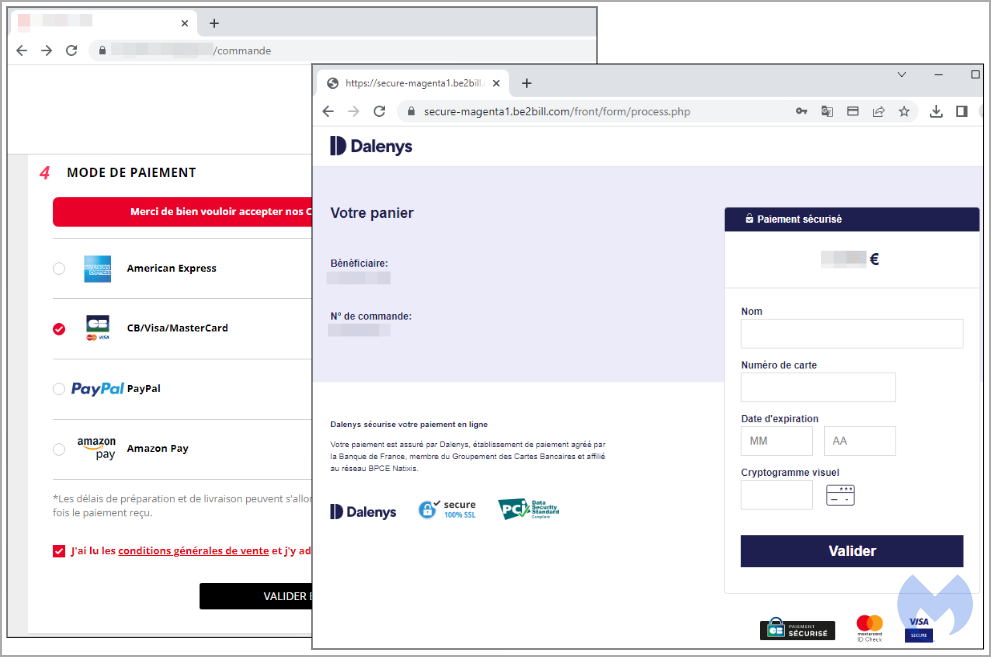
The payment page itself redirects visitors to a third-party processor, and once the banking information is entered, the customer returns to the store page.
If a redirect to an external site is a typical step in online payments, it inspires less confidence in the visitor than the modal form rendered directly on the page.
Unfortunately, Malwarebytes has observed evidence that the trend of using modal forms is gaining traction in the Magecart cybercrime community.
Other examples of websites offering fake payment methods to visitors include a Dutch and Finnish e-commerce site, both of which have a sleek design that helps them pass as genuine.
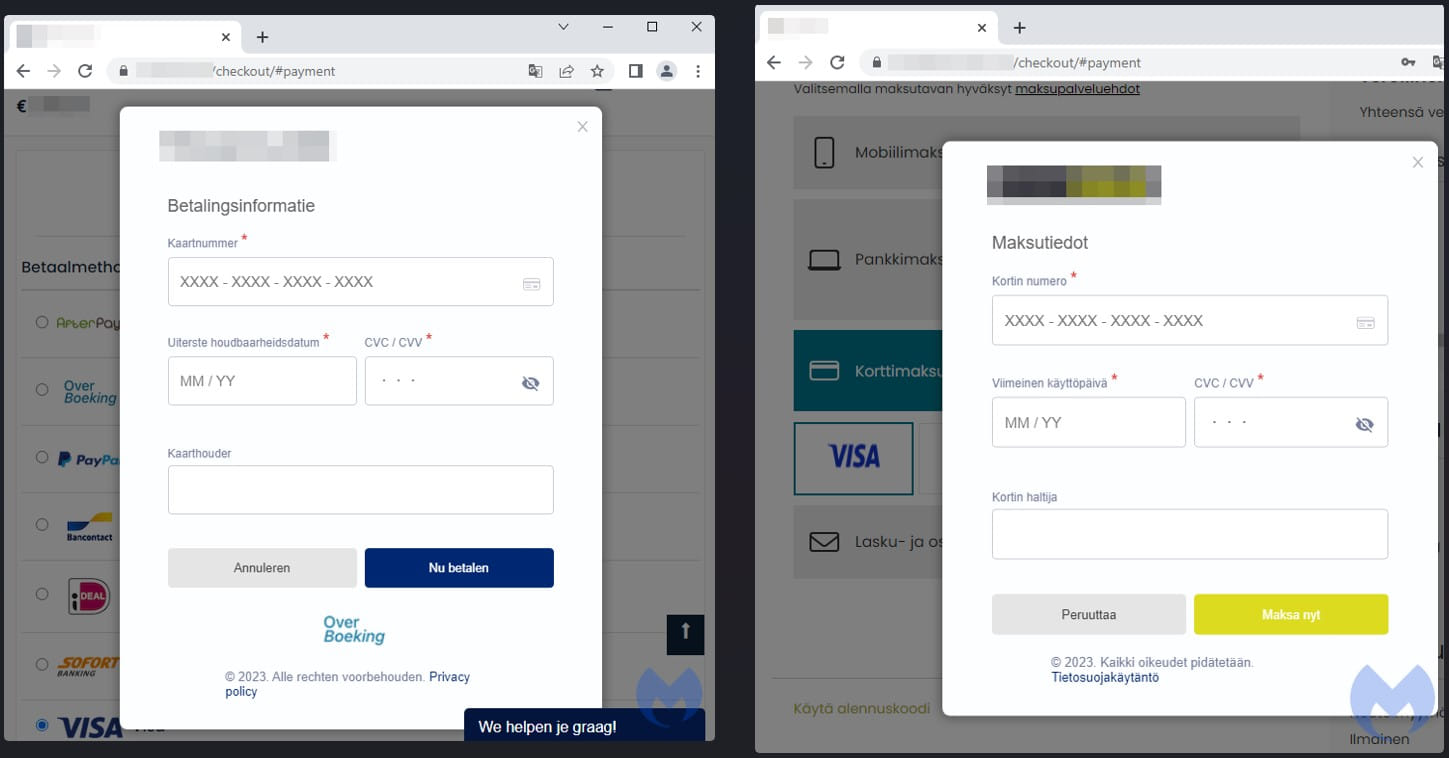
“It is possible that multiple threat actors are involved in these campaigns and customize the skimmers accordingly,” read the report.
“While many hacked stores had a generic skimmer, it seems the custom modals were developed quite recently, maybe a month or two ago.”
Online shoppers should be very vigilant and prefer electronic payment methods or single-use private cards with unnecessary charge limits in the hands of cyber criminals.
[ad_2]
Source link
